Windows User Profile Service (uPRO) is a new feature that allows domain users to manage their home directory in the Users location. This new service can be used to access files in the Users location.
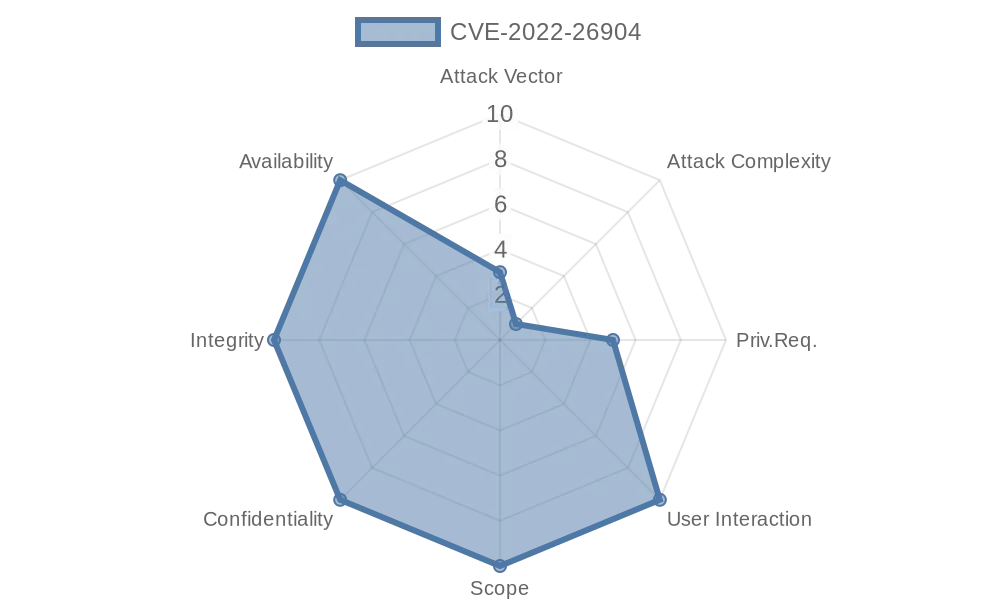
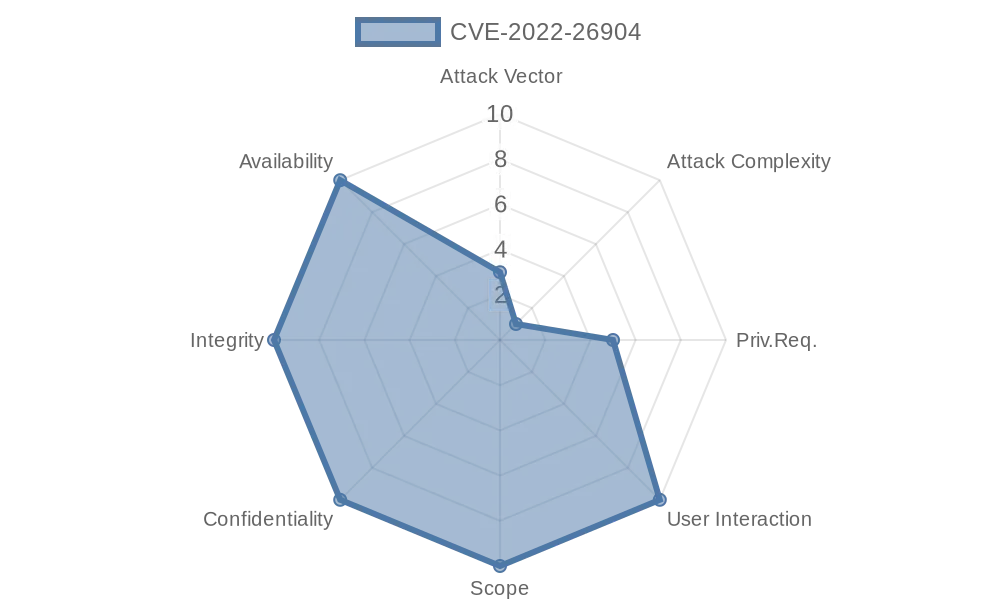
CVE-2022-26904 vulnerability CVSSv3 score is 7.0 (high) and the vector looks like
A vulnerability has been discovered in Windows User Profile Service, which a malicious user can exploit to achieve elevation of privilege on an affected system. uPRO is not enabled by default and must be installed using Group Policy. An attacker successfully exploiting this vulnerability could access sensitive information and execute arbitrary code with SYSTEM privileges.
This is a 3rd (!!!) bypass for the same thing. It's a continuation of the exploit CVE-2022-21919, which is, in turn, a bypass for another issue, CVE-2021-34484. The original Twitter post https://twitter.com/billdemirkapi/status/1508527492285575172 mentioned that CVE-2022-21919 was already being exploited in the wild by using the binary from https://github.com/klinix5/ProfSvcLPE/blob/main/DoubleJunctionEoP/Release/UserProfileSvcEoP.exe.
What's the Windows User Profile Service?
The Windows User Profile Service is a new feature that allows domain users to manage their home folder in the Users location. This new service can be used to access files in the Users location. The Windows User Profile Service is not enabled by default and must be installed using Group Policy. An attacker who successfully exploited this vulnerability could access sensitive information and execute arbitrary code with SYSTEM privileges.
Reasons for CVE-2022-26904 vulnerability
This vulnerability has been discovered in Windows User Profile Service, which can be exploited by a malicious user to achieve elevation of privilege on affected system. The Windows User Profile Service is not enabled by default and must be installed using Group Policy. An attacker who successfully exploited this vulnerability could access sensitive information and execute arbitrary code with SYSTEM privileges.
The exploit code for this, originally at https://github.com/klinix5/SuperProfile but which got taken down, is now available at https://github.com/rmusser01/SuperProfile and its associated forks. Rapid7 team modified and uploaded it as the Metasploit module https://github.com/rapid7/metasploit-framework/pull/16382.