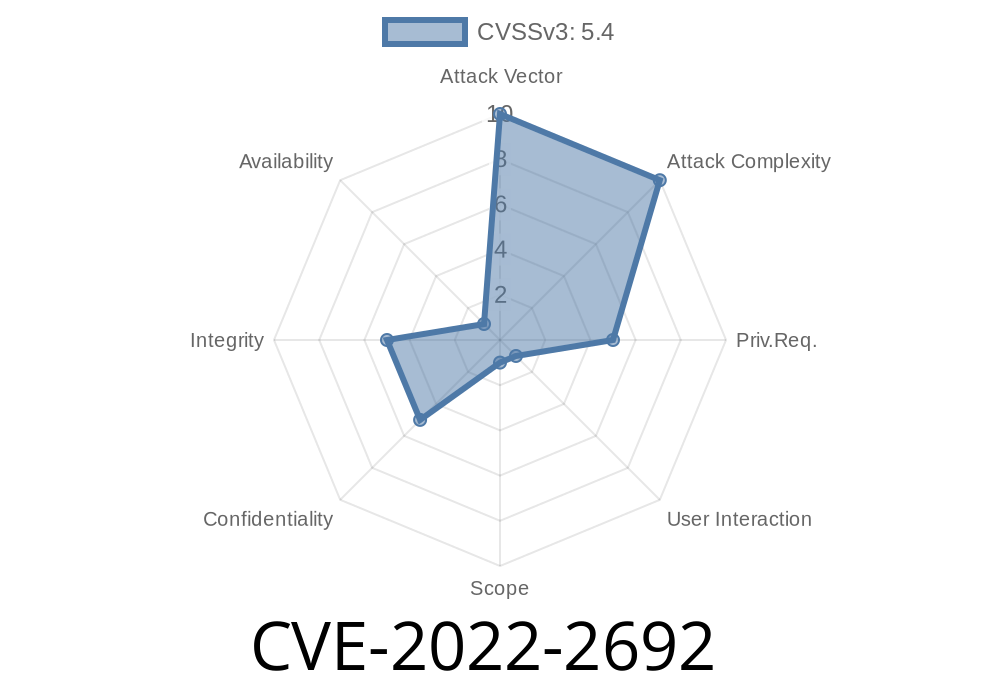
A second vulnerability, which was classified as problematic, was found in SourceCodester Wedding Hall Booking System. This affects an unknown part of the file /whbs/admin/?page=user of the component Staff User Profile. The manipulation of the argument Phone Number/Fax leads to cross site request forgery. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-205816. The first vulnerability was discovered by Stefan Esser from RedTeam Research . The second vulnerability was discovered by Gjoko Miqev from Vupen . Both security researchers have responsibly disclosed these vulnerabilities to the manufacturer.
SourceCodester Wedding Hall Booking System Vulnerability
Dr. Gjoko Miqev, a security researcher from Vupen, discovered an issue in SourceCodester Wedding Hall Booking System. The second vulnerability affects an unknown part of the file /whbs/admin/?page=user of the component Staff User Profile. This is a cross site request forgery vulnerability with remote exploitation potential. SourceCodester Wedding Hall Booking System has been disclosed to the public and may be used by attackers. The associated identifier of this vulnerability is VDB-205816.
VDB-205816: SourceCodester Wedding Hall Booking System
Cross Site Request Forgery Vulnerability
The vulnerability was classified as a cross site request forgery and then the researcher found an unknown part of the file /whbs/admin/?page=user of the component Staff User Profile, which leads to cross site request forgery. The manipulation of the argument Phone Number/Fax leads to cross site request forgery. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-205816. The first vulnerability was discovered by Stefan Esser from RedTeam Research and then Gjoko Miqev from Vupen found out another vulnerability in SourceCodester's system. Both security researchers have responsibly disclosed these vulnerabilities to the manufacturer.
Timeline
Published on: 08/06/2022 18:15:00 UTC
Last modified on: 08/11/2022 14:03:00 UTC