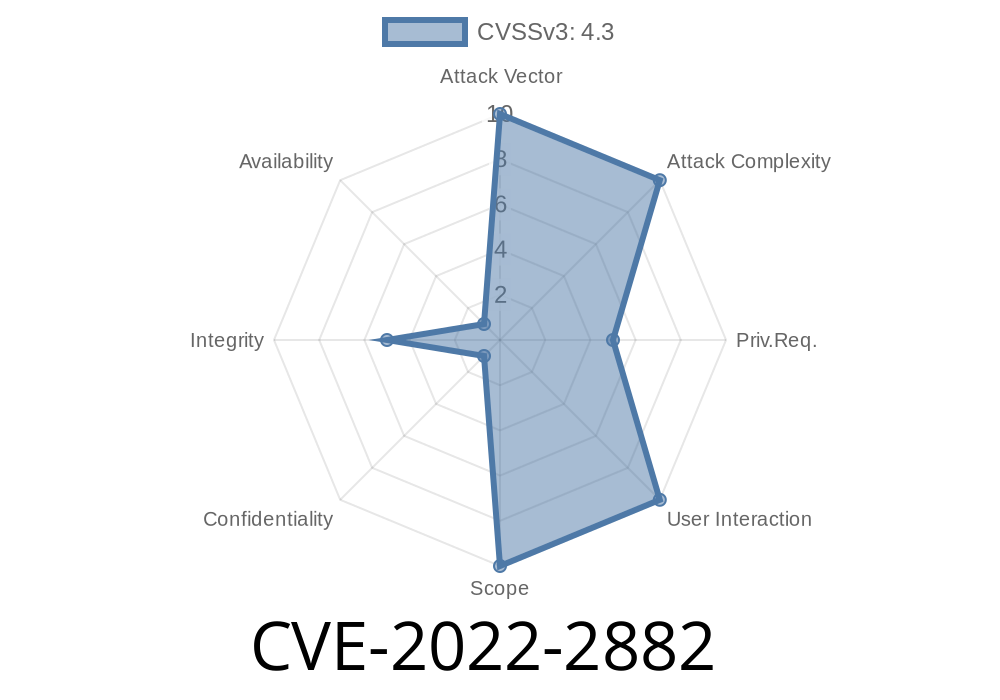
This issue has been addressed in GitLab 15.5. We recommend that you upgrade as soon as possible.
The severity of this issue depends on the type of operations that your organization relies on with GitHub. For example, if you use GitHub for code review, then it’s likely that a malicious maintainer could cause a significant disruption to your organization. This issue has been addressed in GitLab 15.5. We recommend that you upgrade as soon as possible. The severity of this issue depends on the type of operations that your organization relies on with GitHub. For example, if you use GitHub for code review, then it’s likely that a malicious maintainer could cause a significant disruption to your organization. Impact In the worst case scenario, this issue could allow a malicious maintainer to hijack and modify your integration’s access token and use it to access your source code and perform whatever malicious activity they wish. How to upgrade quickly For enterprises with strict security controls, we recommend that you upgrade only if necessary. To upgrade quickly, you can use the following steps: Upgrade the version of GitLab on all hosts that utilize GitHub for code review.
Upgrade the version of the external integration on all hosts with an outdated version.
Once upgraded, you should be secure against this issue
Description of the issue
The severity of this issue depends on the type of operations that your organization relies on with GitHub. For example, if you use GitHub for code review, then it’s likely that a malicious maintainer could cause a significant disruption to your organization. Impact In the worst case scenario, this issue could allow a malicious maintainer to hijack and modify your integration’s access token and use it to access your source code and perform whatever malicious activity they wish.
How to upgrade quickly For enterprises with strict security controls, we recommend that you upgrade only if necessary. To upgrade quickly, you can use the following steps: Upgrade the version of GitLab on all hosts that utilize GitHub for code review.
Upgrade the version of the external integration on all hosts with an outdated version.
Once upgraded, you should be secure against this issue
What is the issue?
A malicious maintainer could hijack and modify your integration's access token, use it to access your source code, and perform whatever malicious activity they wish.
What is the impact of this issue?
This issue allows a malicious maintainer to hijack and modify your integration’s access token and use it to access your source code and perform whatever malicious activity they wish. It can also allow them to perform activities on your behalf like deleting branches or pushing commits. The severity of this issue depends on the type of operations that your organization relies on with GitHub. For example, if you use GitHub for code review, then it’s likely that a malicious maintainer could cause a significant disruption to your organization.
If you use GitHub for code review only, then you’re fine now
If you use GitHub for code review only, then you’re fine now. If your organization is primarily software development and not operations, you should skip this upgrade. Impact In the worst case scenario, this issue could allow a malicious maintainer to hijack and modify your integration’s access token and use it to access your source code and perform whatever malicious activity they wish. How to upgrade quickly For enterprises with strict security controls, we recommend that you upgrade only if necessary. To upgrade quickly, you can use the following steps: Upgrade the version of GitLab on all hosts that utilize GitHub for code review.
Upgrade the version of the external integration on all hosts with an outdated version.
Once upgraded, you should be secure against this issue
Timeline
Published on: 10/28/2022 15:15:00 UTC
Last modified on: 10/28/2022 18:40:00 UTC