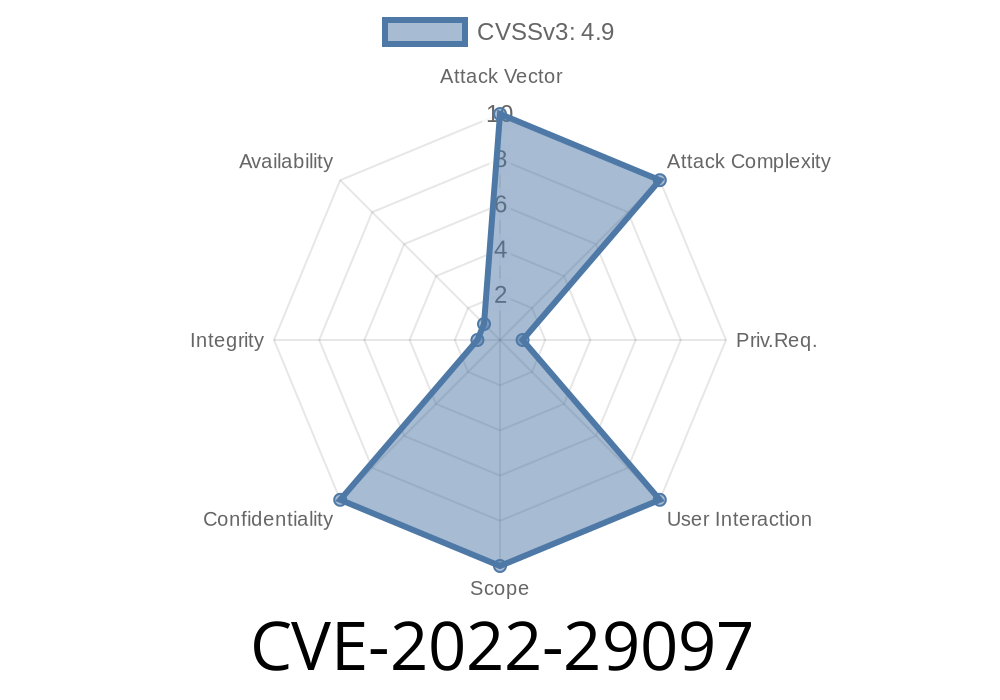
Dell WMS 3.6.2 and onwards contains a Cross-site Request Forgery (CSRF) vulnerability in the Configuration API. A malicious user could potentially exploit this vulnerability, to send malicious requests to the running web application, with the privileges of the running web application.
What type of information could be obtained by an attacker by exploiting these vulnerabilities?
An attacker could potentially view or change the settings of a server.
An attacker could potentially gain access to another location on the same server, or on another server.
What should be done to prevent these vulnerabilities?
Users are advised to install the latest version of Dell WMS, where available.
Patch the system as soon as possible, after applying the update.
For Dell WMS 3.6.1 and below, users are advised to disable Path Traversal, by setting the following property in the wmsd.properties file of the WEB-INF/ directory.
path.traversal=false
For Dell WMS 3.6.2 and onwards, users are advised to disable CSRF, by setting the following property in the wmsd.properties file of the WEB-INF/ directory.
csrf.enabled=false
END
CSRF
Dell WMS 3.6.2 and onwards contains a Cross-site Request Forgery (CSRF) vulnerability in the Configuration API. A malicious user could potentially exploit this vulnerability, to send malicious requests to the running web application, with the privileges of the running web application.
What kind of information could be obtained by an attacker by exploiting these vulnerabilities?
An attacker could potentially view or change the settings of a server. An attacker could potentially gain access to another location on the same server, or on another server.
Dell WMS - XXE Injection Vulnerability
A vulnerability has been identified in Dell WMS 3.6.2 and onwards that could allow an attacker to execute XXE code on a target system.
What type of information could be obtained by an attacker by exploiting these vulnerabilities?
An attacker could potentially view or change the settings of a server.
An attacker could potentially gain access to another location on the same server, or on another server.
What should be done to prevent these vulnerabilities?
Users are advised to install the latest version of Dell WMS, where available.Patch the system as soon as possible, after applying the update.For Dell WMS 3.6.1 and below, users are advised to disable Path Traversal, by setting the following property in the wmsd.properties file of the WEB-INF/ directory., and for Dell WMS 3.6.2 and onwards, users are advised to disable CSRF, by setting the following property in the wmsd.properties file of the WEB-INF/ directory
Dell WMS 3.6.2 and beyond
Dell WMS 3.6.2 and beyond contains a Cross-site Request Forgery vulnerability in the Configuration API. A malicious user could potentially exploit this vulnerability, to send malicious requests to the running web application, with the privileges of the running web application.
What type of information could be obtained by an attacker by exploiting these vulnerabilities?
An attacker could potentially view or change the settings of a server.
An attacker could potentially gain access to another location on the same server, or on another server.
What should be done to prevent these vulnerabilities?
Users are advised to install the latest version of Dell WMS, where available.
Patch the system as soon as possible, after applying the update.
For Dell WMS 3.6.1 and below, users are advised to disable Path Traversal, by setting the following property in the wmsd.properties file of the WEB-INF/ directory.
path.traversal=false
Dell WMS 3.6.2 and onwards - Cross-site Request Forgery (CSRF) vulnerability
Dell WMS 3.6.2 and onwards contains a Cross-site Request Forgery (CSRF) vulnerability in the Configuration API. A malicious user could potentially exploit this vulnerability, to send malicious requests to the running web application, with the privileges of the running web application.
Timeline
Published on: 06/24/2022 17:15:00 UTC
Last modified on: 07/06/2022 14:50:00 UTC