Industrial automation keeps factories humming and energy flowing. But when software that controls manufacturing is vulnerable, the consequences can be severe — from data leaks to production sabotage. Today, let’s dive deep into CVE-2022-29826, a flaw in Mitsubishi Electric's GX Works3 programming suite that could give attackers major leverage.
What is GX Works3?
For those new to industrial automation, GX Works3 is the official software for programming and managing Mitsubishi's iQ-R and iQ-F series PLCs (Programmable Logic Controllers). These are the brains behind everything from assembly lines to water treatment plants.
The Vulnerability: Cleartext Storage of Sensitive Information
CVE-2022-29826 original advisory is about how GX Works3 (versions 1.086Q and before) stores sensitive data in cleartext — unencrypted, easy to read. An attacker, even *without* a user account, could grab the config or program files and dig out sensitive details.
How Bad is It?
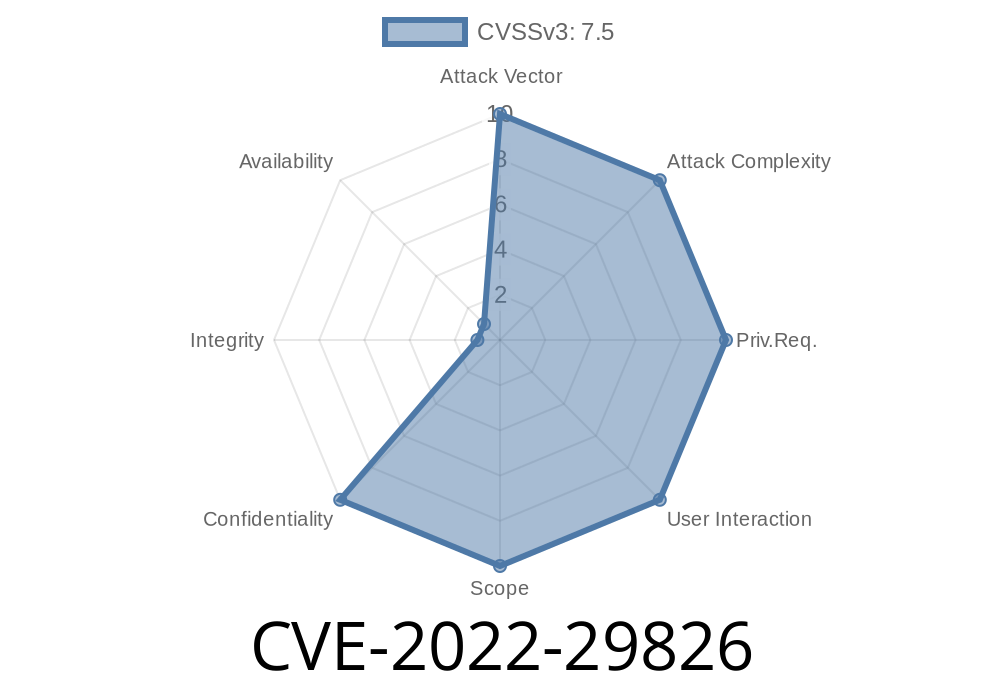
Severity Score: 7.5 (High) on NIST NVD.
User Interaction: None
Translation: if someone can reach your network, they could grab these files and learn everything about your PLC setup.
GX Works3 project files (.gx3, etc.) store
- PLC ladder logic/programs
Possibly licensing and user info
These files are typically saved to workstations, shared network drives, or even central servers.
The problem? Passwords and settings are found as plain text.
1. Locate Project File
Suppose an attacker gets into your network — phishing, weak WiFi password, or an unpatched server vulnerability. They scan file shares for something like Project1.gx3.
# Search all network drives for project files
find /mnt/shared -iname "*.gx3" 2>/dev/null
GX Works3 files can be opened with a simple text editor or hex editor. Sensitive lines may look like
PLC_Password=supersecret123
Connection=192.168..88, Port=5007, User=admin, Pass=plcadminpass
Even if the file isn’t *completely* plain text, info can often be carved out with standard tools
# Find password-like strings in the file
strings Project1.gx3 | grep -i pass
3. Replay the Credentials
Now, with real PLC credentials, the attacker can use GX Works3 or compatible tools to *illegally connect to and modify the PLCs*. At this point, they could:
Real-World Impact Example
Imagine an attacker changing water flow schedules in a treatment plant, or disabling safety logic in a chemical process. Industrial incidents like the 2021 Florida Water Utility hack have shown how software insecurity can have life-and-death consequences.
Update GX Works3
Mitsubishi released version 1.091Q (or later) to fix this vulnerability. Download here (vendor site).
*Always* run the latest version.
Restrict File Share Access
Only trusted users should be able to read/write project files. Use strong access controls and network segmentation.
Store project files on encrypted drives or use encrypted containers like BitLocker or VeraCrypt.
Use file integrity monitoring (FIM) and watch logs for strange access patterns.
References and Further Reading
- JVN Japan Vulnerability Advisory
- NVD CVE-2022-29826 Entry
- Mitsubishi Security Advisory
- Mitre CVE Record
Final Thoughts
This bug is a reminder: industrial software isn’t immune to old-school security risks. Any time sensitive data is kept in cleartext, attackers get an easy win. If you use Mitsubishi’s GX Works3 (or similar PLC tools), update now, and review your storage practices. Prevention today can save a world of trouble tomorrow.
Stay secure, and if you have automation projects, always treat your config files like the sensitive keys they are!
Timeline
Published on: 11/25/2022 00:15:00 UTC
Last modified on: 11/28/2022 21:01:00 UTC