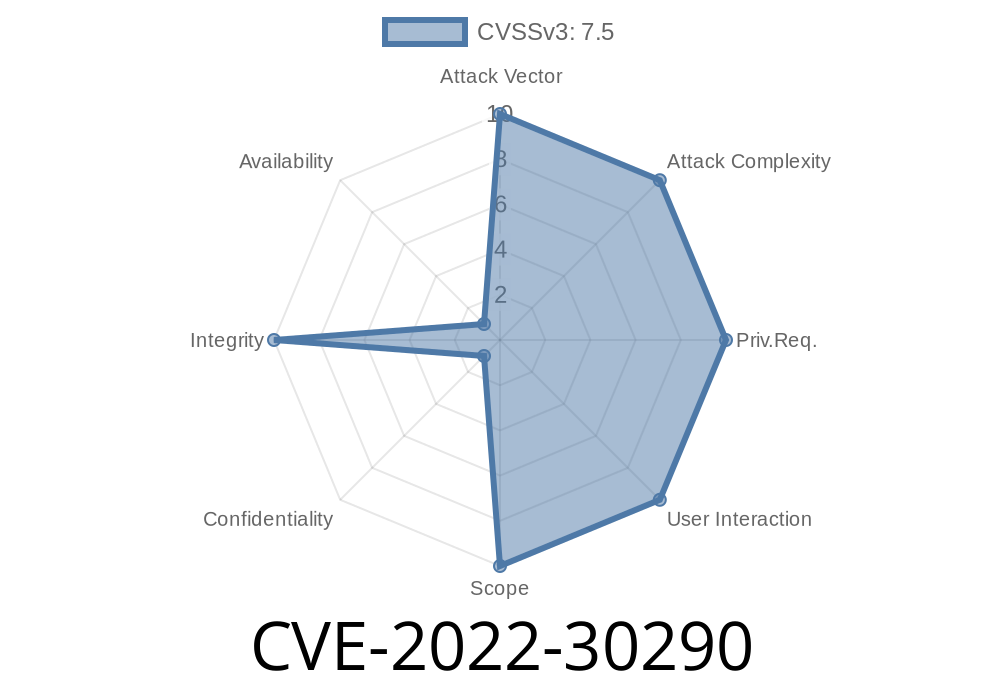
The vulnerability has been fixed in version 5.2.5. If you are using any version prior to 5.2.5, it’s recommended to upgrade your installation as soon as possible. OpenCTI is a social network for customer relationship management with a wide range of usage cases. One of its most common usage cases is to grant access to the system to customers or partners. An access control vulnerability has been identified in the profile endpoint of OpenCTI that can be exploited by malicious users to maliciously change their registered e-mail address, as well as their API key, without any limitation. The flaw has been fixed in version 5.2.5. If you are using any version prior to 5.2.5, it’s recommended to upgrade your installation as soon as possible.
General security advice for OpenCTI
Whenever a vulnerability has been identified in an application, it is important to monitor your installed versions and upgrade as soon as possible, in this case, to the fixed version.
The vulnerability was identified on the 9th October 2017. The vendor responsible for OpenCTI has released a fix on the 14th October 2017.
What’s an access control vulnerability?
An access control vulnerability is a flaw in the system that allows malicious users to access data they aren't supposed to have. This flaw can be exploited by malicious users by changing their registered e-mail address, as well as their API key on the user management endpoint. Once they’ve gained access to this information, they are able to manipulate it like normal. They can change their current profile information or create a new account.
What is the OpenCTI Vulnerability?
The vulnerability is located in the profile endpoint of OpenCTI. This endpoint can be exploited by malicious users to change their registered e-mail address and/or their API key without any limitation. The flaw has been fixed in version 5.2.5. If you are using any version prior to 5.2.5, it’s recommended to upgrade your installation as soon as possible
Timeline
Published on: 07/05/2022 13:15:00 UTC
Last modified on: 07/11/2022 13:39:00 UTC