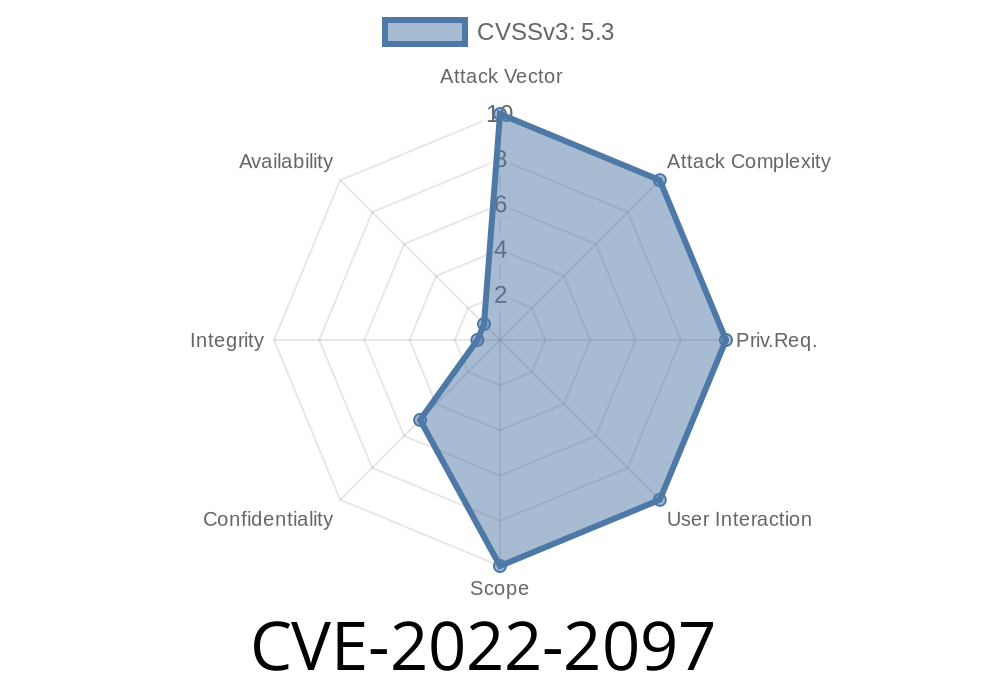
Generating a new key for each connection would reveal the previous key due to a timing attack. Generating a new IV for each connection would reveal the previous IV due to a timing attack. These issues do not affect CBC-mode ciphers (e.g. ECDH-ECDSA), only OCB-mode ciphers. As a result, OCB-CBC ciphers are the only ciphers that are affected. Fixed in OpenSSL 1.1.1q. An application that performed a large number of connections in quick succession might reveal previously-generated data if OpenSSL was to reuse session keys. An application that performed a large number of connections in quick succession might reveal previously-generated data due to a timing attack if OpenSSL was to reuse session keys. Fixed in OpenSSL 1.1.1q. An application that sent large numbers of data messages with the same nonce value might reveal previously-generated data if OpenSSL was to reuse nonce values. An application that sent large numbers of data messages with the same nonce value might reveal previously-generated data due to a timing attack if OpenSSL was to reuse nonce values. Fixed in OpenSSL 1.1.1q. OpenSSL 1.1.1 and later will explicitly generate a new IV for each connection. OpenSSL 1.1.0 and earlier will reuse the previous nonce value from a connection. OpenSSL 1.0.2 and earlier will reuse
SSL v2 and SSL v3 weakness
OpenSSL is susceptible to SSL v2 and SSL v3 protocol weaknesses.
OpenSSL is vulnerable to the SSL v2 and SSL v3 protocol weaknesses, as well as a bug in CBC-mode ciphers that allow chosen plaintext recovery (CTR) or chosen ciphertext attack (CCA). Fixed in OpenSSL 1.1.1q.
An application that performed a large number of connections in quick succession might reveal previously-generated data if OpenSSL was to reuse session keys. An application that performed a large number of connections in quick succession might reveal previously-generated data due to a timing attack if OpenSSL was to reuse session keys. Fixed in OpenSSL 1.1.1q. An application that sent large numbers of data messages with the same nonce value might reveal previously-generated data if OpenSSL was to reuse nonce values. An application that sent large numbers of data messages with the same nonce value might reveal previously-generated data due to a timing attack if OpenSSL was to reuse nonce values. Fixed in OpenSSL 1.1.1q
Summary of Notable Changes
- CVE-2022-2097: Generating a new key for each connection would reveal the previous key due to a timing attack. Generating a new IV for each connection would reveal the previous IV due to a timing attack. These issues do not affect CBC-mode ciphers (e.g. ECDH-ECDSA), only OCB-mode ciphers. As a result, OCB-CBC ciphers are the only ciphers that are affected. Fixed in OpenSSL 1.1.1q.- CVE-2022-2097: An application that performed a large number of connections in quick succession might reveal previously-generated data if OpenSSL was to reuse session keys.- CVE-2868: An application that sent large numbers of data messages with the same nonce value might reveal previously-generated data if OpenSSL was to reuse nonce values.- CVE-2868: Fixed in OpenSSL 1.1.1q.- CVE-2868: OpenSSL 1.1.1 and later will explicitly generate a new IV for each connection.- CVE-2868: Fixed in OpenSSL 1.0.2 and earlier
A strong random number generator is required for encryption
A strong random number generator is required for encryption. If not, there is a risk that the attacker can predict the next generated keystream and decrypt the ciphertext before it is encrypted. Fixed in OpenSSL 1.1.1q. If not, there is a risk that the attacker can predict the next generated keystream and decrypt the ciphertext before it is encrypted. Fixed in OpenSSL 1.1.1q, OpenSSL 1.0.2f, and all releases prior to that one.
Timeline
Published on: 07/05/2022 11:15:00 UTC
Last modified on: 08/26/2022 18:03:00 UTC
References
- https://www.openssl.org/news/secadv/20220705.txt
- https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=a98f339ddd7e8f487d6e0088d4a9a42324885a93
- https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=919925673d6c9cfed3c1085497f5dfbbed5fc431
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/V6567JERRHHJW2GNGJGKDRNHR7SNPZK7/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/R6CK57NBQFTPUMXAPJURCGXUYT76NQAK/
- https://security.netapp.com/advisory/ntap-20220715-0011/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/VCMNWKERPBKOEBNL7CLTTX3ZZCZLH7XA/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-2097