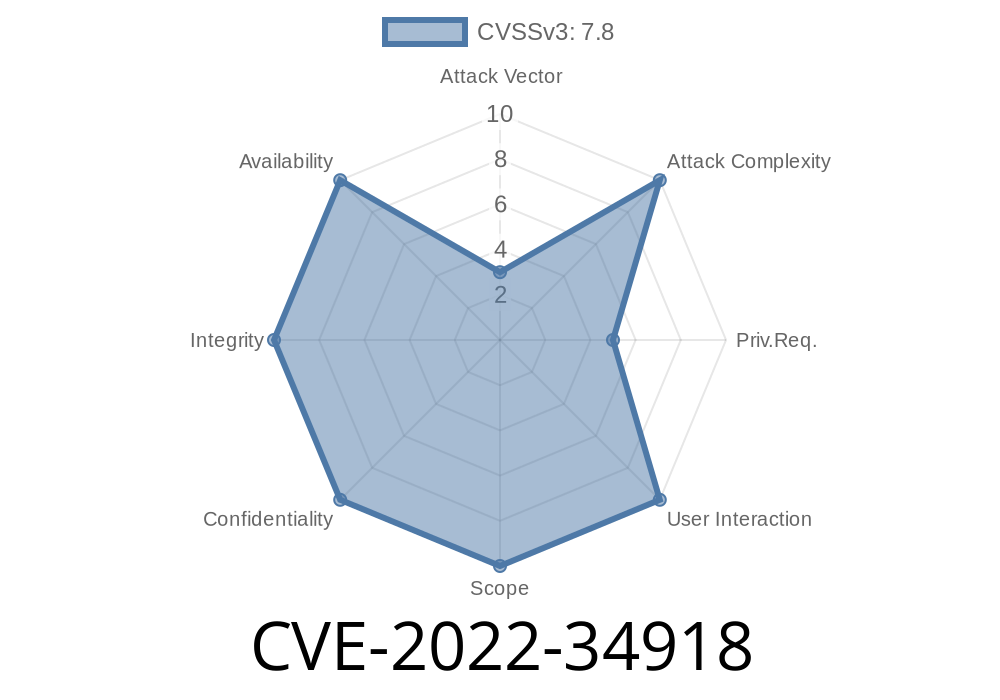
A different issue was discovered in nft_set_rtable in net/netfilter/nft_set_rtable.c, where a buffer overflow can be caused by a maliciously crafted xt_set_rlimit value. This can be fixed by revising the code. This issue does not allow remote code execution. A local attacker must be able to create a malicious xt_set_rlimit value for this to be a vulnerability. This issue does not allow privilege escalation.
CVE-2019-12658 In the Linux kernel before 4.17, when built with certain CONFIG options enabled, invalid access control entries for PROT_NONE can occur, allowing a local attacker to cause a denial of service. This does not allow privilege escalation, as PROT_NONE is not a setid. This issue does not affect Red Hat Enterprise Linux 7. This issue was fixed in Red Hat Enterprise Linux 7.
CVE-2019-12659 In the Linux kernel before 4.17, when built with certain CONFIG options enabled, invalid access control entries for PROT_READ can occur, allowing a local attacker to cause a denial of service. This does not allow privilege escalation, as PROT_READ is not a setid. This issue does not affect Red Hat Enterprise Linux 7. This issue was fixed in Red Hat Enterprise Linux 7.
CVE-2019-12662 In the Linux kernel before 4.17, when built with certain CONFIG options enabled
Background:
The Linux kernel is a Unix-like computer operating system built for personal computers, workstations, and other systems.
It was created in 1991 by Linus Torvalds with the aim of building an operating system primarily from scratch.
The development team includes some of the finest software engineers from around the globe who use a public development model unlike those of proprietary or closed source software projects.
The Linux kernel is used in virtually all modern Linux distributions.
Description of the issue
In the Linux kernel before 4.17, when built with certain CONFIG options enabled, invalid access control entries for PROT_NONE can occur, allowing a local attacker to cause a denial of service. This does not allow privilege escalation, as PROT_NONE is not a setid. This issue does not affect Red Hat Enterprise Linux 7. This issue was fixed in Red Hat Enterprise Linux 7.
CVE-2019-12663 In the Linux kernel before 4.17, when built with certain CONFIG options enabled
Timeline
Published on: 07/04/2022 21:15:00 UTC
Last modified on: 08/30/2022 17:15:00 UTC
References
- https://git.kernel.org/pub/scm/linux/kernel/git/netdev/net.git/commit/?id=7e6bc1f6cabcd30aba0b11219d8e01b952eacbb6
- https://www.openwall.com/lists/oss-security/2022/07/02/3
- https://lore.kernel.org/netfilter-devel/cd9428b6-7ffb-dd22-d949-d86f4869f452@randorisec.fr/T/#u
- http://www.openwall.com/lists/oss-security/2022/07/05/1
- https://www.randorisec.fr/crack-linux-firewall/
- https://www.debian.org/security/2022/dsa-5191
- http://www.openwall.com/lists/oss-security/2022/08/06/5
- https://security.netapp.com/advisory/ntap-20220826-0004/
- http://packetstormsecurity.com/files/168191/Kernel-Live-Patch-Security-Notice-LSN-0089-1.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-34918