For GitLab Enterprise and Enterprise Extended users, it may also be possible to steal their PGP private keys by performing a similar attack. This issue affects all versions of GitLab before 15.1.6, all versions starting from 15.2 before 15.2.4, all versions starting from 15.3 before 15.3.2. For all versions affected, it may be possible for an attacker to guess a user's password by brute force by sending crafted requests to a specific endpoint, even if the victim user has 2FA enabled on their account. In particular, this affects all versions of GitLab EE, starting from version 5.0. For all versions affected, it may be possible for an attacker to steal their PGP private keys by performing a similar attack. It may be possible to force GitLab to store an arbitrary CSRF token by sending a crafted request to a specific end point, even if the victim user has 2FA enabled on their account. It is recommended to enable 2FA for all users especially for those that have the role of "Author", "Repository Manager" or "Administrator" on their GitLab instance. It is also recommended to enable CSRF protection for those routes that are accessed by users on the "create account" or "change password" end points. For all versions affected, it may be possible to leak data by sending a crafted request to a specific end point, even if the victim user has 2FA enabled on their account.
Affected versions and the impact
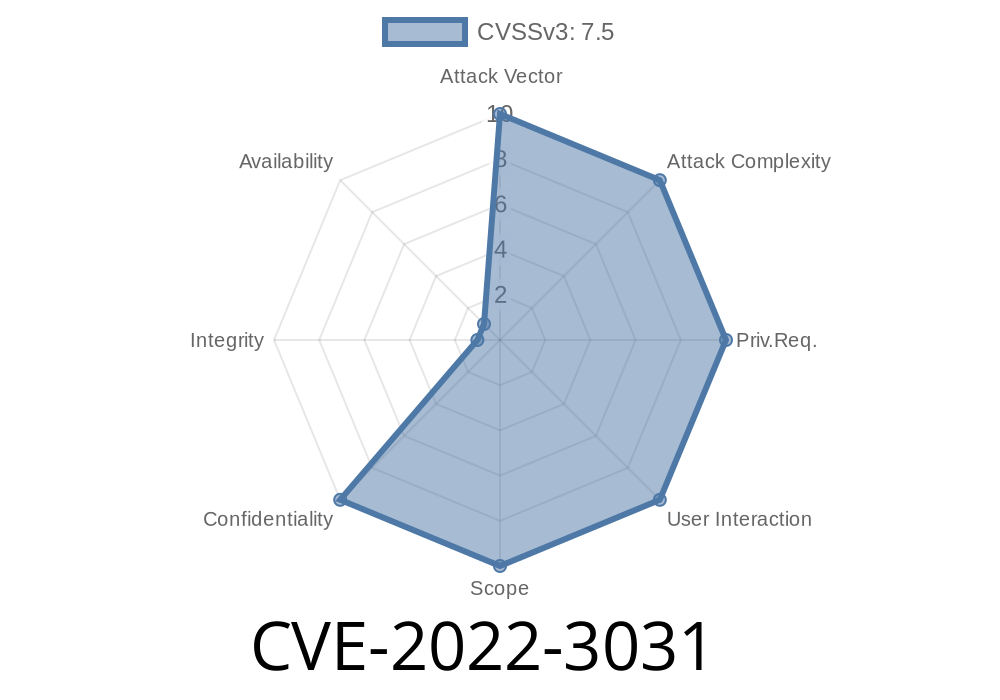
The vulnerability affects all versions of GitLab before 15.1.6, all versions starting from 15.2 before 15.2.4, all versions starting from 15.3 before 15.3.2 which are released on the date of publishing this post and prior to April 1, 2019 (version 6.9).
For all affected versions, an attacker may be able to guess a user's password by brute force by sending crafted requests to a specific endpoint even if the victim user has 2FA enabled on their account. Additionally, an attacker may be able to steal their PGP private keys by performing a similar attack, it may be possible to force GitLab to store an arbitrary CSRF token by sending a crafted request to a specific end point and it may be possible for an attacker to leak data by sending a crafted request to a specific end point even if the victim user has 2FA enabled on their account
Gitaly (CVE-2022)
2
FA and CSRF Protection for GitLab Enterprise Users
All versions of GitLab EE before 5.0 are vulnerable to the above attack, as well as all versions starting from 15.2 before 15.2.4, so it is recommended that you upgrade to at least that version if you are using any of those versions to mitigate this issue. All versions of GitLab EE after 5.0 are not vulnerable to any attacks related to these vulnerabilities, and all versions of GitLab EE beginning with version 6.0 are also not vulnerable. For all versions affected, please follow the mitigation steps below:
If you use a password-protected private key file on your GitLab instance:
1) Make sure your private key file is only readable by users who have "Author" or "Repository Manager" privileges
2) Make sure your private key file is only accessible via HTTPS (not HTTP) https://
How to detect if you are affected
It is recommended to test your account and ensure that you are not affected by this. The following steps can be used to test your account:
1) Login with a user that doesn't have 2FA enabled (for example, "admin")
2) Navigate to the "Administration" > "Manage Users" page
3) Create a new user and provide an email address on the "New User Setup" page. You will then see a request sent to GitLab's logout endpoint. This request can be verified in the "Requests Logs & Events" tab of the Admin UI in order for an attacker to force GitLab's service to store an arbitrary CSRF token. Additionally, this request can be used as a way of checking if you are vulnerable to CSRF attacks, if you don't allow requests from unauthorized domains or IP addresses.
Timeline
Published on: 10/17/2022 16:15:00 UTC
Last modified on: 10/19/2022 15:17:00 UTC