allowing any attacker capable of communicating with the ports in question to invoke (a subset of) desired functionality. The Honeywell Experion LX DCS utilizes the Control Data Access (CDA) EpicMo protocol (55565/TCP) for device diagnostics and maintenance purposes. This protocol does not have any authentication features, allowing any attacker capable of communicating with the ports in question to invoke (a subset of) desired functionality. There is no authentication functionality on the protocol in question, allowing any attacker capable of communicating with the ports in question to invoke (a subset of) desired functionality. The potential impact of this flaw is Firmware manipulation as well as Denial of service. The potential impact of this flaw is Firmware manipulation as well as Denial of service. In summary, this issue results in the ability to remotely execute code on the device. Symptom: Unauthenticated Control Data Access (CDA) EpicMo protocol (55565/TCP) with unauthenticated functionality issue.
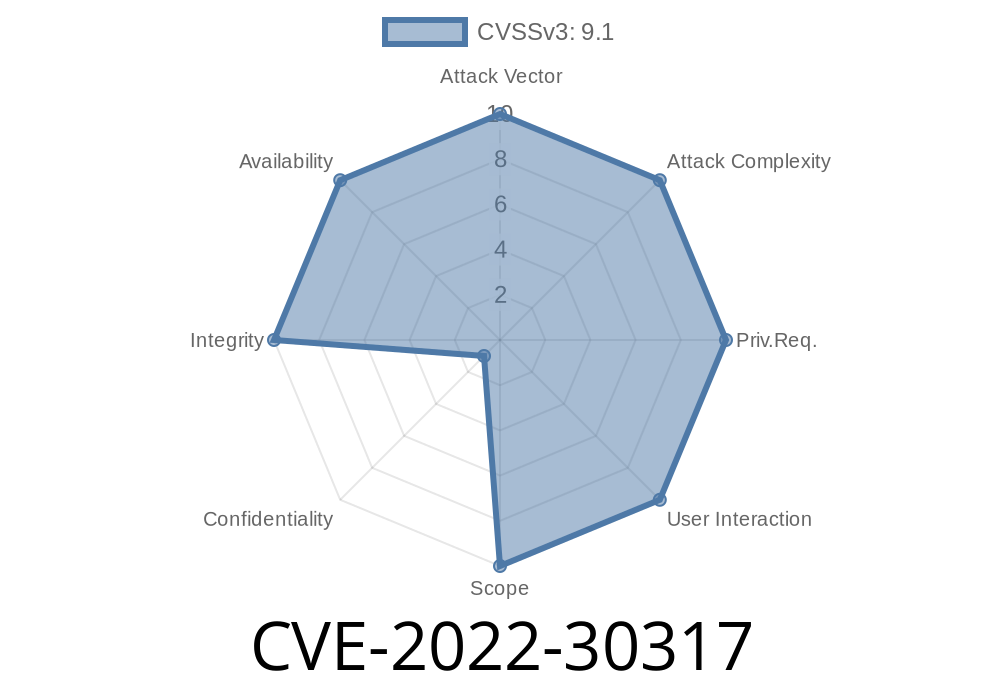
Honeywell Vantage Pro through 2022-05-06 has Missing Authentication for a Critical Function. According to FSCT-2022-0056, there is a Honeywell Vantage Pro Control Data Access (CDA) EpicMo protocol with unauthenticated functionality issue. The affected components are characterized as: Honeywell Control Data Access (CDA) EpicMo (55565/TCP). The potential impact is: Firmware manipulation, Denial of
Summary of Key Findings
The Honeywell Vantage Pro through 2022-05-06 has Missing Authentication for a Critical Function. According to FSCT-2022-0056, there is a Honeywell Vantage Pro Control Data Access (CDA) EpicMo protocol with unauthenticated functionality issue. The affected components are characterized as: Honeywell Control Data Access (CDA) EpicMo (55565/TCP). The potential impact is: Firmware manipulation, Denial of service.
In summary, this issue results in the ability to remotely execute code on the device. Symptoms: Unauthenticated Control Data Access (CDA) EpicMo protocol with unauthenticated functionality issue; Firmware manipulation; Denial of service.
Timeline
Published on: 08/31/2022 16:15:00 UTC
Last modified on: 09/09/2022 03:41:00 UTC