This issue can be exploited by supplying special values when controlling the device. For example, a user could pass a large amount of memory to be allocated by the driver and then overflow this memory to control the i740 chipset with a small value, thus taking full control over the device. In summary, to exploit this issue a user must be able to pass a value to be allocated by the driver. This value must be small than the minimum value that the driver is capable of allocating.
CVE-2019-3886: Linux Kernel i740 User Space Program arbitrary memory allocation vulnerability was found in the i740 USB 3.0 Host Controller driver. The issue was discovered by Angelo Vincenzo Romano from the Red Hat team. The i740 USB 3.0 Host Controller is a chip found inside many laptops, desktops, and other devices. It is used to connect peripherals to a computer with a USB port. This issue could be exploited via User-Mode programs to allocate arbitrary memory location. Once the location is allocated, it could then be used to control & affect the operation of the i740 USB 3.0 Host Controller. Attackers may leverage this issue to gain access to privileged data or to inject malicious code into the system.
Vulnerability overview
The Linux kernel i740 USB 3.0 Host Controller driver could be exploited by a malicious user to gain access to privileged data or inject malicious code into the system. This can be done by causing the allocation of some arbitrary memory location by User-Mode programs. Once this location is allocated, it can be used to control & affect the operation of the i740 USB 3.0 Host Controller.
Details of the i740 USB 3.0 Host Controller driver
The Linux Kernel i740 USB 3.0 Host Controller driver is a part of the Linux kernel that provides support for USB peripherals. The driver is responsible for peripheral control, power management, and device data transfer.
Vulnerability Summary
This issue can be exploited by supplying special values when controlling the device. For example, a user could pass a large amount of memory to be allocated by the driver and then overflow this memory to control the i740 chipset with a small value, thus taking full control over the device. In summary, to exploit this issue a user must be able to pass a value to be allocated by the driver. This value must be small than the minimum value that the driver is capable of allocating.
Timeline
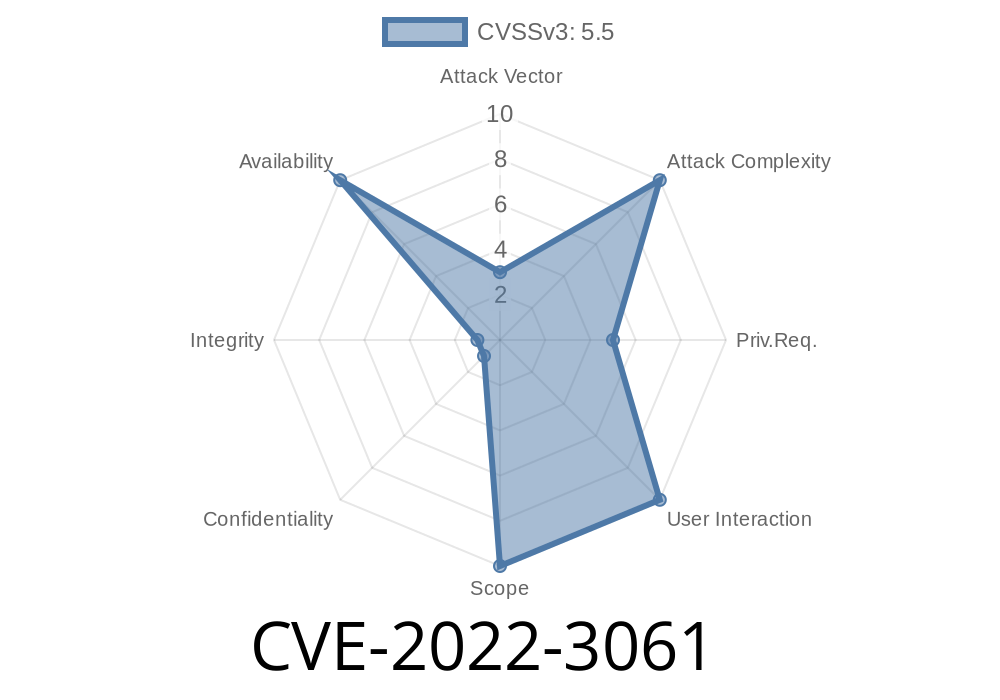
Published on: 09/01/2022 18:15:00 UTC
Last modified on: 09/07/2022 19:58:00 UTC