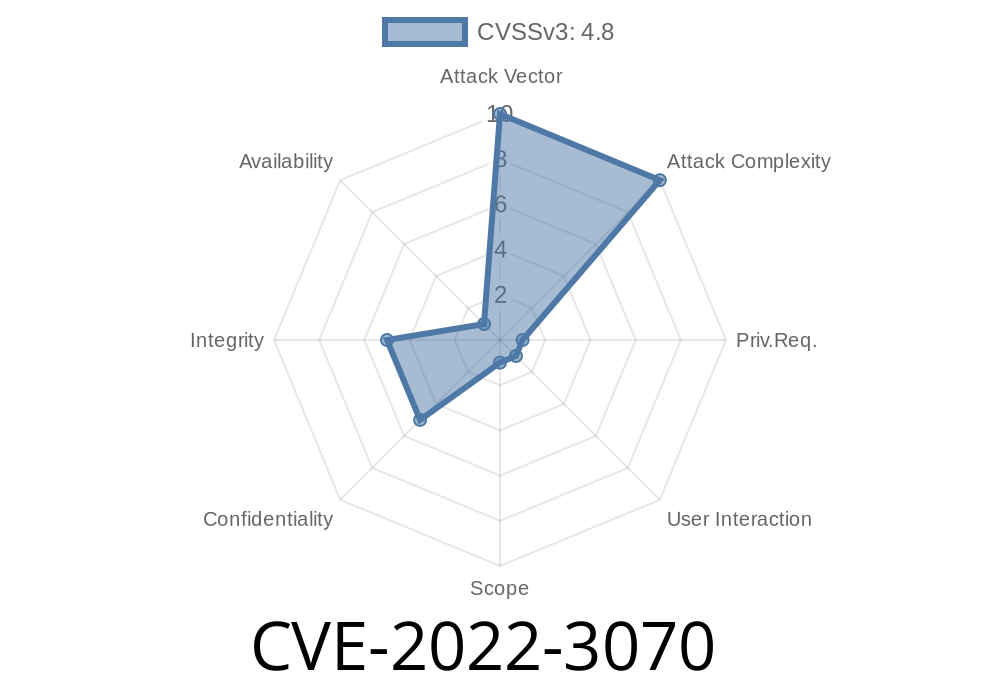
This allows attackers with low privilege levels to inject malicious code into the generated PDFs, thus escalating their privileges on the site. Plugins that generate PDFs are usually installed by high privilege users. This makes it critical that the code that is being injected into the PDFs is sanitised and validated before it is inserted into the PDF. To make sure that the code that is being injected is validated and sanitised, you must use the Generate PDF WordPress plugin v3.6 and up. To avoid this issue, you must upgrade to the latest version of the plugin.
CVE-2022-3071
This allows attackers with low privilege levels to inject malicious code into the generated PDFs, thus escalating their privileges on the site. Plugins that generate PDFs are usually installed by high privilege users. This makes it critical that the code that is being injected into the PDFs is sanitised and validated before it is inserted into the PDF. To make sure that the code that is being injected is validated and sanitised, you must use the Generate PDF WordPress plugin v3.6 and up. To avoid this issue, you must upgrade to the latest version of the plugin.
Timeline
Published on: 09/26/2022 13:15:00 UTC
Last modified on: 09/27/2022 04:38:00 UTC