Another example of an unauthenticated attacker sending a specially crafted update file that can overflow a buffer can allow them to execute arbitrary code on the device. This can be exploited for remote code execution, for example, by sending a malicious update file to the device. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices. An attacker can receive a specially crafted update file and send it to the device. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices. The HID devices contain a Flash memory to store the firmware. The Flash memory is normally protected by a CC/CCP (Common Code Protection/Common Code Protection) scheme. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices.
HID device vulnerability example
An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices. For example, an attacker could exploit HID devices running at firmware version 1.0.2 using a specially crafted update file and send that file to all of the newly installed devices on a network. The new update file would overwrite the existing Flash memory in each device with data that would allow the attacker to execute arbitrary code on each device and use those devices for remote code execution, for example. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices.
Vulnerabilities found in the device firmware
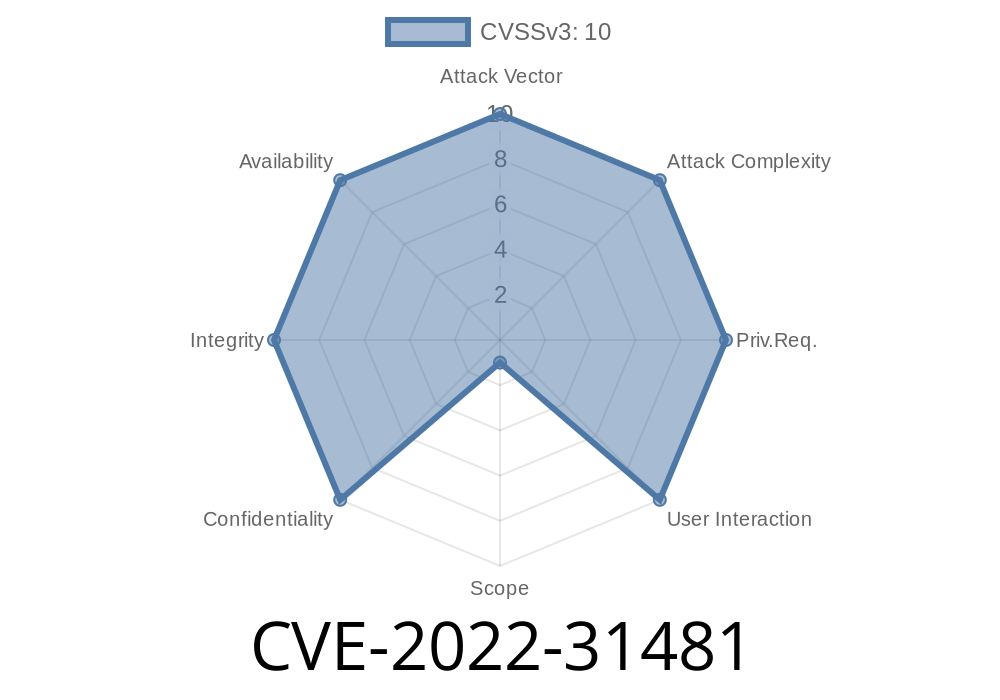
CVE-2022-31481: Another example of an unauthenticated attacker sending a specially crafted update file that can overflow a buffer can allow them to execute arbitrary code on the device. This can be exploited for remote code execution, for example, by sending a malicious update file to the device.
An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices.
Vulnerability overview
Designated CVE-2022-31481
This vulnerability allows an attacker to send a specially crafted update file that will cause the device to overflow a buffer and potentially run arbitrary code on the device. An attacker can receive a specially crafted update file and send it to the device, which can then be exploited to run arbitrary code on the device. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices.
CVE-2023-31482
Another example of an unauthenticated attacker sending a specially crafted update file that can overflow a buffer can allow them to execute arbitrary code on the device. This can be exploited for remote code execution, for example, by sending a malicious update file to the device. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices. An attacker can receive a specially crafted update file and send it to the device. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices. The HID devices contain a Flash memory to store the firmware. The Flash memory is normally protected by a CC/CCP (Common Code Protection/Common Code Protection) scheme. An attacker can send a specially crafted update file to the device that will cause it to overflow a buffer. This can be exploited to run arbitrary code on the device, which can then be used to launch attacks against other devices.
Timeline
Published on: 06/06/2022 17:15:00 UTC
Last modified on: 06/17/2022 14:31:00 UTC