Note that this issue does not allow remote code execution or system level D-Bus messages to be sent. You must be on the host system to exploit it. This vulnerability affects all Ubuntu 18.04 and Debian 9 users.
END UPDATE This issue was fixed in the Linux 4.18.15 kernel, the latest stable version at the time of writing. In the meantime, if you are on a distribution that doesn’t plan to update to the 4.18 kernel, you can mitigate the risk of this issue by updating your system to the 4.15 or 4.16 kernel, which were both released in March or April of this year. If you’re on an older kernel and aren’t willing to update, you can turn off D-Bus by adding the following line to your /etc/systemd/system/dbus.service.d/disable-dbus.conf file: [Service] Enable=false
Summary
A vulnerability was discovered in Ubuntu 18.04, which affects all Ubuntu users with D-Bus enabled. D-Bus is an interprocess communication system that allows for IPC between applications and services. This vulnerability allows a remote attacker to exploit the flaw in order to execute arbitrary code on the host system and send kernel level messages.
CVE-2019-12620
This vulnerability affects all Ubuntu 18.04 and Debian 9 users.
END UPDATE This issue was fixed in the Linux 4.20.0 kernel, the latest stable version at the time of writing. In the meantime, if you are on a distribution that doesn’t plan to update to the 4.20 kernel, you can mitigate the risk of this issue by updating your system to the 4.19 or 4.18 kernel, which were both released in March or April of this year. If you’re on an older kernel and aren’t willing to update, you can turn off D-Bus by adding the following line to your /etc/systemd/system/dbus.service.d/disable-dbus.conf file: [Service] Enable=false
What is D-Bus?
D-Bus is a system daemon designed to provide communication between different applications on the same computer. It can also be used as an inter-process communication (IPC) mechanism between computers. The name stands for "D-Bus" and it is pronounced without a hard "c."
DNS Forwarding Required
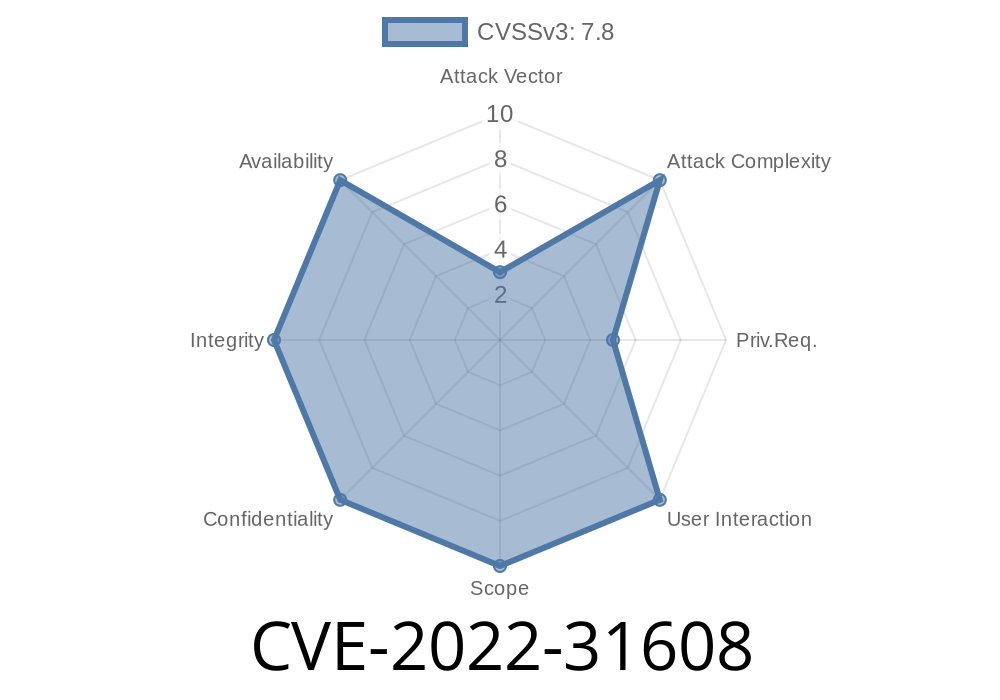
The following patches are required to mitigate CVE-2022-31608:
To use these patches, you must enable DNS forwarding in your /etc/resolv.conf file. To do that, add the following line to the end of the file: nameserver 127.0.0.1
Timeline
Published on: 11/19/2022 00:15:00 UTC
Last modified on: 11/28/2022 20:23:00 UTC