Function is a client library and CLI enabling the development and deployment of Kubernetes functions. Developers using a malicious or compromised third-party buildpack could expose their registry credentials or local docker socket to a malicious `lifecycle` container. This issues has been patched in PR #1442, and is part of release 1.8.1. This issue only affects users who are using function buildpacks from third-parties; pinning the builder image to a specific content-hash with a valid `lifecycle` image will also mitigate the attack. In addition to the security issues outlined above, there are a few minor known issues in the release: The function CLI does not work on Windows. It is recommended to use a cross-built Linux environment.
It is not possible to deploy functions using external custom domains.
Function 1.8.1 introduces a breaking change in the `args` field of the function definition. This is a breaking change for functions that have previously been created with the 1.8.0 version. If a function that was created in 1.8.0 is upgraded to 1.8.1, the `args` field must be updated with an appropriate value.
What is a buildpack?
A Kubernetes buildpack is a set of scripts which are deployed locally on the cluster and then executed to perform various tasks in order to transform an image into a set of container images.
The first step in using buildpacks is to create an account with a third-party builder, including ClusterHQ's buildpack. For example, you could use our CLDNS buildpack that builds Docker images for Node.js applications. Then, you'll need to add the third-party buildpack as one of your default ones so it is used when building containers in the cluster.
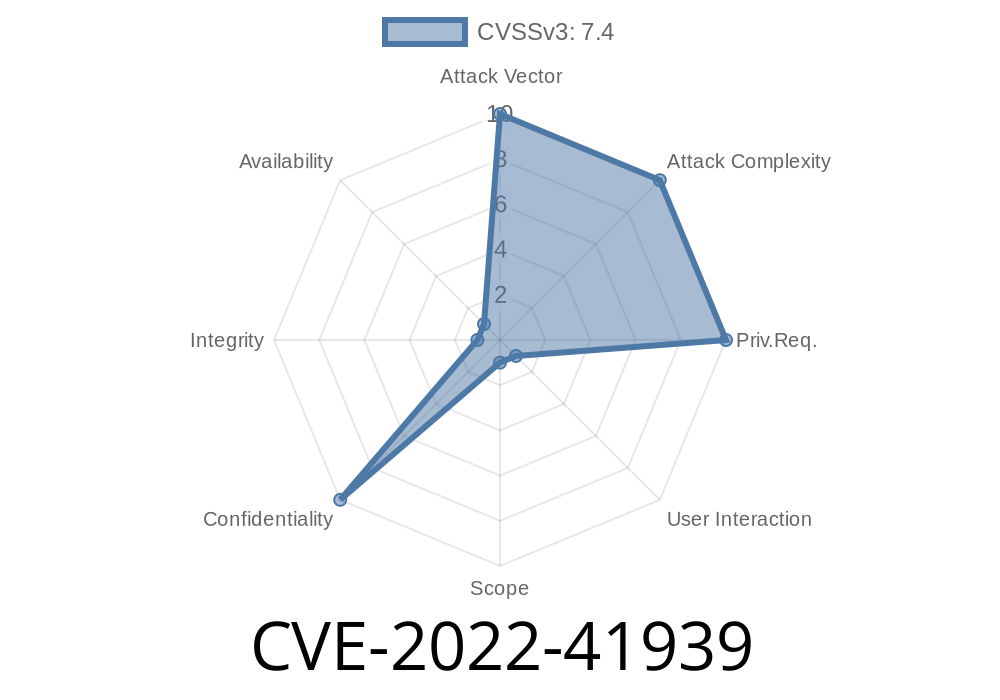
Function Security Vulnerability Summary
A vulnerability has been found in the `args` field of the function definition. A malicious buildpack could be used to expose registry credentials and local docker socket to a malicious `lifecycle` container.
This issue only affects users who are using function buildpacks from third-parties; pinning the builder image to a specific content-hash with a valid `lifecycle` image will also mitigate the attack.
In addition to the security issues outlined above, there are a few minor known issues in this release: The function CLI does not work on Windows. It is recommended to use a cross-built Linux environment. It is not possible to deploy functions using external custom domains. Function 1.8.1 introduces a breaking change in the `args` field of the function definition. This is a breaking change for functions that have previously been created with the 1.8.0 version. If a function that was created in 1.8.0 is upgraded to 1.8.1, the `args` field must be updated with an appropriate value
Function Security Improvements
The release also includes security and usability improvements, including:
**PR 1442**
Function 1.8.1 includes a fix for CVE-2019-19739 (private registry keys exposed in `lifecycle` container) as well as the following additional fixes:
* Reduce the risk of code injection vulnerability by allowing override of function context to be set with environment variables.
* Improve diagnostics for failures deploying functions to Kubernetes clusters by adding an informative message indicating that a user needs to create an account on GitHub.
Timeline
Published on: 11/19/2022 01:15:00 UTC
Last modified on: 11/26/2022 03:21:00 UTC
References
- https://github.com/knative/func/blob/5ca77d38744d3481cc0b795f607c5859b19588fc/buildpacks/builder.go#L37-L41
- https://github.com/knative/func/releases/tag/knative-v1.8.1
- https://github.com/knative/func/pull/1442
- https://github.com/knative/func/security/advisories/GHSA-5336-2g3f-9g3m
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-41939