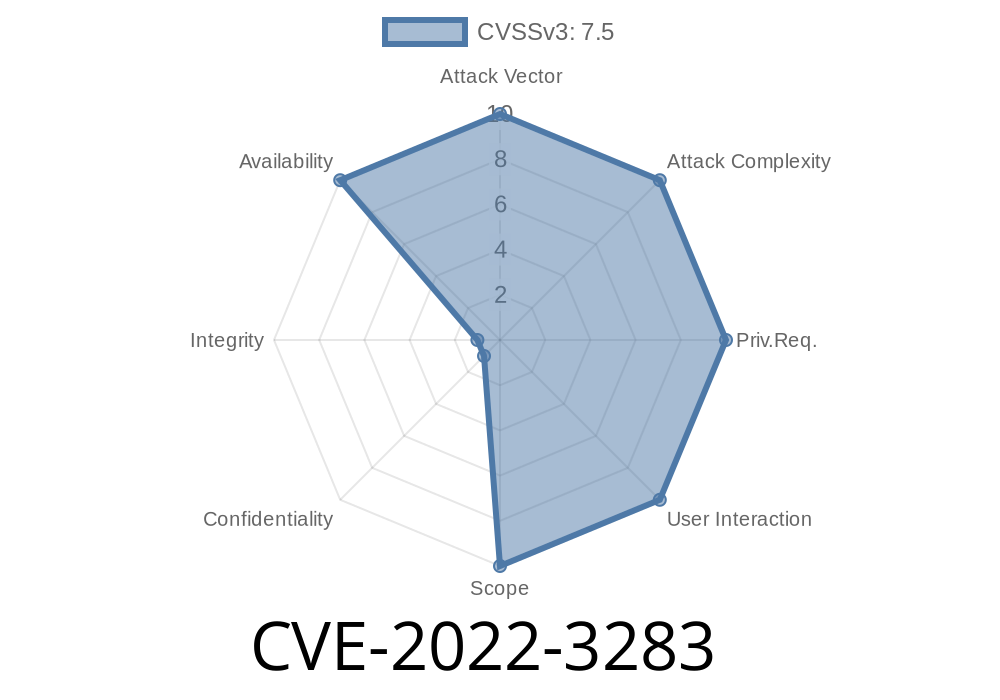
GitLab recommends always using HTTPS when accessing the software, as well as updating to the latest version. Additionally, it is recommended to avoid cloning issues with custom content as it could lead to unexpected results. As always, be careful when clicking links in emails or chats. A potential SQL injection vulnerability was discovered in GitLab affecting all versions before before 15.2.5, all versions starting from 15.3 before 15.3.4, all versions starting from 15.4 before 15.4.1 A user with the ‘’admin’’ account could have exploited this flaw to obtain sensitive information from the database. An attacker could have used this information to create a new user with administrative rights, assign them to a team, assign them access rights, or simply view the database to obtain sensitive information.
How to stay safe?
When using the software, always use HTTPS. Additionally, it is recommended to avoid cloning issues with custom content as it could lead to unexpected results. As always, be careful when clicking links in emails or chats.
GitLab Issues and What to Do
Always use HTTPS and update to the latest version of GitLab.
Avoid cloning issues with custom content, as it could lead to unexpected results.
Be careful when clicking links in emails or chats
SQL Injection
SQL injection is a type of attack that allows an attacker to execute arbitrary SQL commands through a targeted system. In order to exploit this vulnerability, the user must have permission to log into GitLab. The issue was fixed in 15.2.5 and all later versions of GitLab.
Authentication and Session Management
Authentication and session management are important in any software application. While GitLab’s authentication methods are robust, it is still recommended to ensure that critical data and functions aren’t affected by a potential SQL injection vulnerability. It is possible for an attacker with the ‘’admin’’ account to access sensitive information if they have been able to exploit the flaw and create a new user with administrative rights, assign them to a team, assign them access rights, or simply view the database to obtain sensitive information. Make sure that users only have permissions that they need and limit what data can be accessed by each user.
Timeline
Published on: 10/17/2022 16:15:00 UTC
Last modified on: 10/20/2022 14:17:00 UTC