Macs are known for being pretty secure, but every once in a while, a dangerous bug pops up. One such bug was CVE-2022-32897, a memory corruption issue in Apple’s macOS Monterey. In this post, we’ll walk you through what this bug was, how it could have been exploited, and how Apple fixed it. Grab your coffee – let’s get into it!
What is CVE-2022-32897?
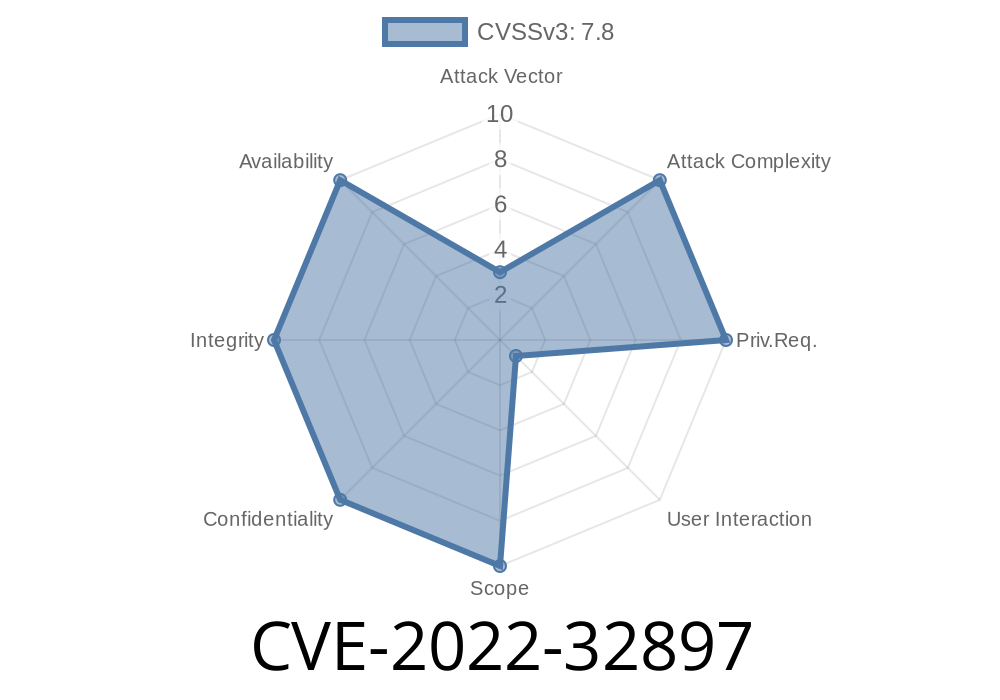
CVE-2022-32897 is a memory corruption vulnerability that affected macOS Monterey up to version 12.4. This bug was hiding in the way macOS processes TIFF image files. If an attacker created a specially crafted TIFF file (a common graphics format), and you opened or previewed it on your Mac, it could trigger this bug, allowing the attacker to run any code they want on your computer.
Apple’s own advisory put it simply
> “Processing a maliciously crafted tiff file may lead to arbitrary code execution. A memory corruption issue was addressed with improved validation.”
>
> https://support.apple.com/en-us/HT213345
How Did This Happen?
The TIFF format—used since the 198s—lets programs store images with lots of details. But it’s also complicated, and decoding it wrong can invite bugs.
The core of CVE-2022-32897 was that when macOS tried to open a malicious TIFF file, it didn’t properly validate some parts of that file. As a result, malicious data could overwrite key areas of memory (a “memory corruption”). That could allow an attacker’s code to run — possibly giving them full control of your Mac.
Example Exploit Scenario (Simplified)
Let’s say someone sends you an infected TIFF image via email, or you visit a website that loads this file. If your system (before 12.5) opens or previews it — even as a thumbnail — the hidden code inside could hijack the application. If the app has high privileges, it could install malware, steal data, or take over the system.
Example PoC (Proof-of-Concept) — For Research Only!
While the full exploit code is not public (and we won’t share anything dangerous), here’s a Python snippet that helps visualize what an attacker *might* do: craft a TIFF file with oversized or invalid tag values, crunching a vulnerable parser.
# Malicious TIFF generator (concept only)
header = b"II*\x00" # Little-endian header
# Fake directory entry: tries to trigger read/write out of bounds
directory_entry = b'\x00\x00\x08\x00' * 10 # Overlong, invalid tags
malicious_tiff = header + directory_entry
with open("evil.tiff", "wb") as f:
f.write(malicious_tiff)
print("Evil TIFF created.")
*Note: This does NOT exploit the bug; it's a harmless conceptual illustration!*
Could lead to arbitrary code running on your computer — a full hack
A technical breakdown of similar bugs:
Project Zero – Exploiting image parsing bugs
The Fix: Safer Image Validation
Apple patched the vulnerability in macOS Monterey 12.5 by adding stronger checks when TIFF files are imported or previewed. The update validates the size, type, and data in each field of the TIFF, blocking malformed files from corrupting memory.
Apple’s update info:
https://support.apple.com/en-us/HT213345
If you haven’t updated your Mac, now’s the time! Go to System Preferences > Software Update and install the latest version.
References
* Apple Security Update 2022-07-20 (HT213345)
* NIST NVD Entry for CVE-2022-32897
* Project Zero: Image Parsing Vulnerabilities
* Wikipedia: TIFF File Format
Stay smart, stay updated, and remember: sometimes a picture really is worth a thousand hacks!
Timeline
Published on: 06/10/2024 20:15:12 UTC
Last modified on: 07/03/2024 01:38:33 UTC