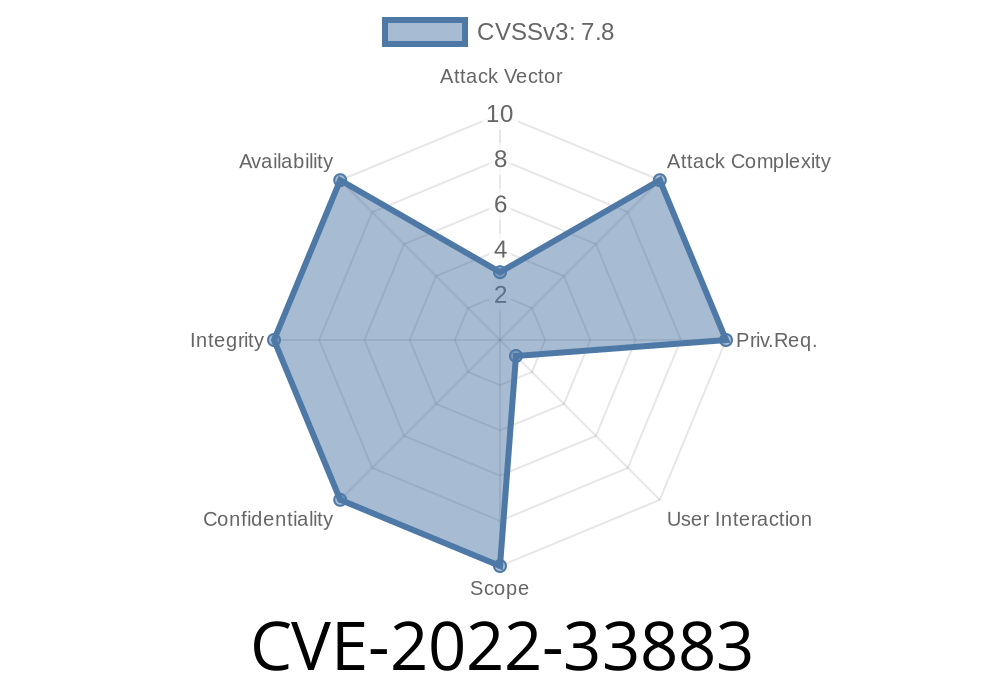
Memory corruption vulnerabilities could be exploited even when application has the system rights.
Moldflow applications could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow application could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow applications could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow applications could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow application could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow applications could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow application could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow application could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow application could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow application could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow application could be tricked into consuming malicious files. This consumption could lead to code execution.
Moldflow application could be tricked into consuming malicious files
Check for Memory Corruption vulnerabilities
All applications have memory corruption vulnerabilities. The only way to prevent these vulnerabilities is to ensure that those who have access to the application do not have the ability to exploit those vulnerabilities. This is where the concept of least privilege comes into play. If a user has a low level of access, their privileges are limited so they cannot abuse those privileges and create an exploit. However, if an application grants one user all rights without any limitations, this vulnerability can be exploited by that user.
Timeline
Published on: 10/03/2022 15:15:00 UTC
Last modified on: 10/04/2022 20:52:00 UTC