An attacker can leverage this vulnerability to perform remote code execution. Remote attackers can host malicious DLLs in the server’s entry attachments and convince users to open them with Remote Desktop Manager. An attacker can also forge an attachment and send it to users with Remote Desktop Manager. Remote users with access to the server’s entry attachment can cause remote code execution. An attacker can host malicious DLLs in the server’s entry attachments and convince users to open them with Remote Desktop Manager. An attacker can also forge an attachment and send it to users with Remote Desktop Manager. Remote users with access to the server’s entry attachment can cause remote code execution. Remote attackers can host malicious DLLs in the server’s entry attachments and convince users to open them with Remote Desktop Manager. An attacker can also forge an attachment and send it to users with Remote Desktop Manager. Remote users with access to the server’s entry attachment can cause remote code execution. Remote attackers can host malicious DLLs in the server’s entry attachments and convince users to open them with Remote Desktop Manager. An attacker can also forge an attachment and send it to users with Remote Desktop Manager. Remote users with access to the server’s entry attachment can cause remote code execution. Remote attackers can host malicious DLLs in the server’s entry attachments and convince users to open them with Remote Desktop Manager
Vulnerability details
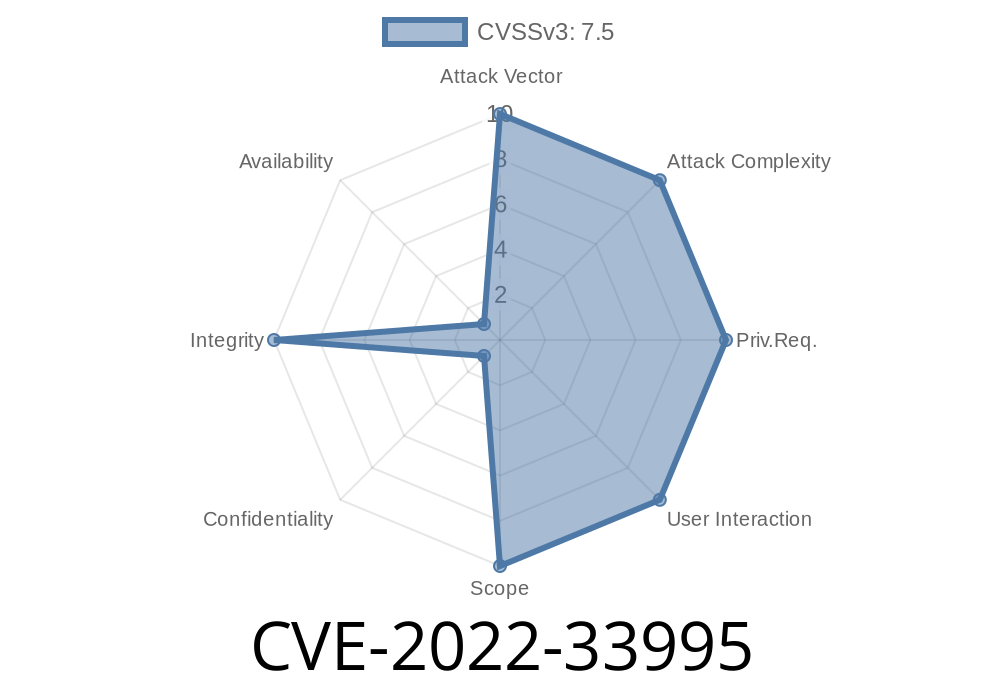
CVE-2022-33995 is a vulnerability in Remote Desktop Manager that allows an attacker to remotely execute code on the server.
Remote code execution in Windows 8 and Server 2012
Microsoft released Windows 8 and Server 2012 on October 31, 2012. Microsoft provided updates to these products to address known vulnerabilities, including CVE-2022-33995. Due to an error in the way that Microsoft addressed this vulnerability in these OSes, users may be vulnerable to remote code execution.
Coverage
This vulnerability affects Remote Desktop Manager.
Microsoft Windows Remote Desktop Vulnerability and Exploitation
This vulnerability is exploited when a user clicks on an attachment sent to them with Remote Desktop Manager. The user is then taken to the attacker’s website where they are met with a fake login dialog and tricked into filling in the credentials. They are then able to gain access to their computer as if they were logged in locally.
The attack vector of this vulnerability is considered high and would require specific actions by the target machine in order for exploitation to occur. This vulnerability can only be exploited when users have access to a server’s entry attachment, which can be controlled by organizations.
Timeline
Published on: 06/21/2022 15:15:00 UTC
Last modified on: 06/28/2022 20:53:00 UTC