An attacker can exploit this vulnerability by uploading malicious files to the target’s account. A successful exploit can result in session hijacking or information disclosure. Vesta v1.0.0-5 was also found to contain a SQL injection vulnerability at /web/api/v1/groups/GroupData.php via the group_data_fields parameter. An attacker can exploit this issue by injecting malicious data into the group_data_fields parameter. A successful exploit can result in database takeover. Vesta v1.0.0-5 was discovered to have a cross-site request forgery (CSRF) vulnerability at /web/api/v1/groups/GroupData.php via the group_data_fields parameter. An attacker can exploit this issue by tricking the victim into updating the group_data_fields parameter. A successful exploit can result in session hijacking or information disclosure. Vesta v1.0.0-5 was also found to have a SQL injection vulnerability at /web/api/v1/teams/TeamData.php via the team_data_fields parameter. An attacker can exploit this issue by injecting malicious data into the team_data_fields parameter. A successful exploit can result in database takeover.
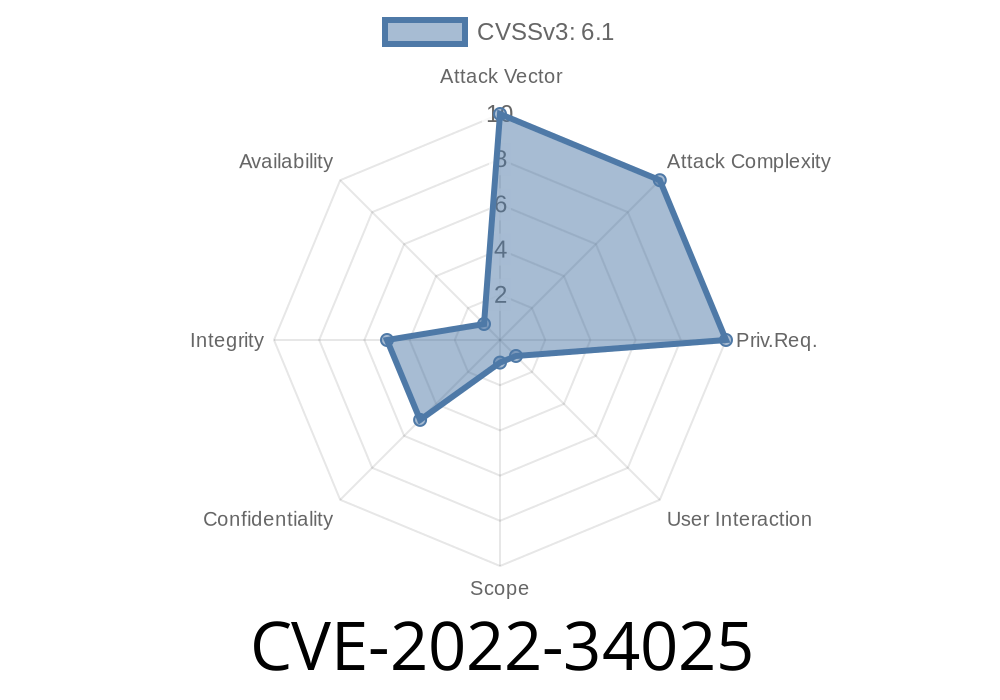
Vesta v1.0.0-5 was discovered to have a cross-site scripting (XSS) vulnerability at /web/api/v1/teams/TeamData.php
Vulnerable Codes /web/api/v1/teams/TeamData.php
Vulnerabilities found in Vesta v1.0.0-5
Vesta v1.0.0-5 was discovered to have a cross-site request forgery (CSRF) vulnerability at /web/api/v1/teams/TeamData.php via the team_data_fields parameter. An attacker can exploit this issue by tricking the victim into updating the team_data_fields parameter. A successful exploit can result in session hijacking or information disclosure.
Vesta v1.0.0-5 was also found to have a SQL injection vulnerability at /web/api/v1/teams/TeamData.php via the team_data_fields parameter. An attacker can exploit this issue by injecting malicious data into the team_data_fields parameter. A successful exploit can result in database takeover.
Vesta v1.0.0-4
A cross-site scripting vulnerability was found in Vesta v1.0.0-4 at /web/api/v1/teams/TeamData.php wherein the team_data_fields parameter could be exploited by injecting malicious data into the team_data_fields parameter. A successful exploit can result in session hijacking or information disclosure. Vesta v1.0.0-5 was also found to have a SQL injection vulnerability at /web/api/v1/teams/TeamData.php via the team_data_fields parameter. An attacker can exploit this issue by injecting malicious data into the team_data_fields parameter. A successful exploit can result in database takeover
Timeline
Published on: 07/19/2022 19:15:00 UTC
Last modified on: 07/25/2022 19:06:00 UTC