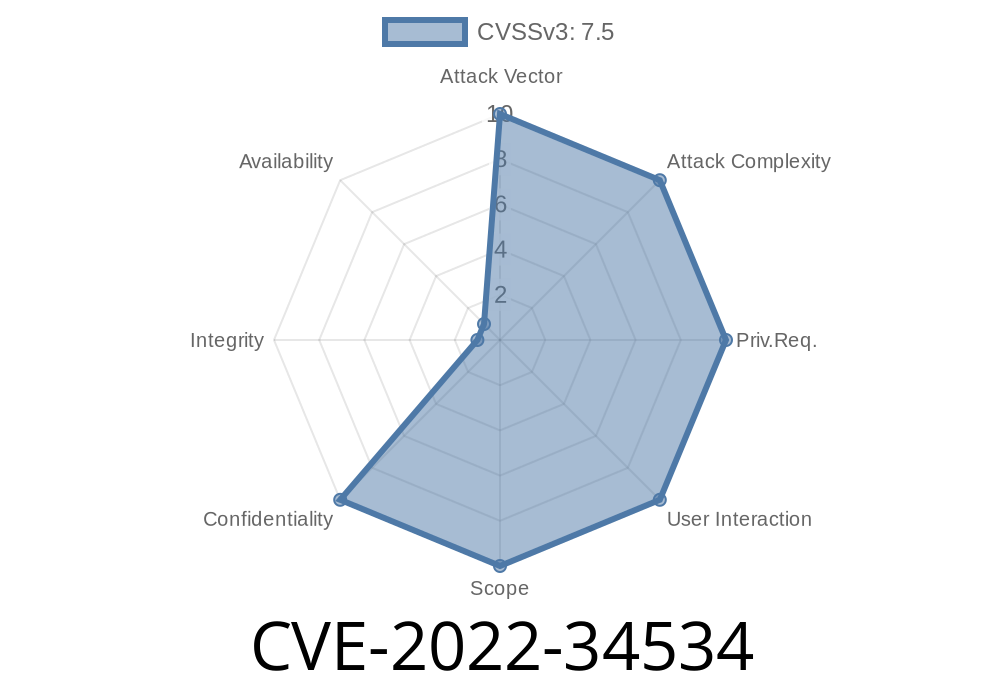
An attacker can craft a request in order to inject data into the server. The server then processes the request and passes the data on to the API. An attacker may use a variety of methods to inject data into the server. These methods include, but are not limited to, sending an invalid request, sending a request over a request, sending a request to an invalid API, etc.
If an attacker is able to inject data into a request, the data may be processed and passed on to the API. An attacker may use a variety of methods to inject data into the server. These methods include, but are not limited to, sending an invalid request, sending a request over a request, sending a request to an invalid API, etc. If an attacker is able to inject data into a request, the data may be processed and passed on to the API. An attacker may use a variety of methods to inject data into the server. These methods include, but are not limited to, sending an invalid request, sending a request over a request, sending a request to an invalid API, etc. An attacker may also use a crafted API call to inject data into the server. An attacker may use a variety of methods to craft an API call to inject data into the server. These methods include, but are not limited to, sending an invalid API call, sending a request over a request, sending a request to an invalid API, etc.
How Do I Prevent SQL Injection?
The best way to prevent SQL injection is through proper input validation. This means ensuring that data sent by the user is only allowed in specific fields and when the data does not meet a certain criteria, the application will not process it. Additionally, you should make sure that your application has parameterized queries, which are queries that can be specified with POST data rather than GET.
Example: CVE-2022-34535
An attacker can craft a request in order to inject data into the server. The server then processes the request and passes the data on to the API. An attacker may use a variety of methods to inject data into the server. These methods include, but are not limited to, sending an invalid request, sending a request over a request, sending a request to an invalid API, etc.
An attacker may also use a crafted API call to inject data into the server. An attacker may use a variety of methods to craft an API call to inject data into the server. These methods include, but are not limited to, sending an invalid API call, sending a request over a request, sending a request to an invalid API, etc.
INFO
An urn or other type of variable that is used for storage of information within functions
Ensure that your application is secure
If an attacker is able to craft a request in order to inject data into the server, the data may be processed and passed on to the API. This could have a variety of impacts on your application. These impacts could include, but are not limited to, leaking sensitive information, compromising user accounts, or allowing attackers to use your application as part of their own attack. If an attacker is able to craft a request in order to inject data into the server, the data may be processed and passed on to the API. This could have a variety of impacts on your application. These impacts could include, but are not limited to, leaking sensitive information, compromising user accounts, or allowing attackers to use your application as part of their own attack. An attacker might also craft an API call in order to inject data into the server. An attacker might use a variety of methods in order to craft an API call in order to inject data into the server. These methods include, but are not limited to, sending an invalid API call, sending a request over a request, sending a request to an invalid API/etc.
Timeline
Published on: 07/19/2022 20:15:00 UTC
Last modified on: 07/26/2022 22:37:00 UTC