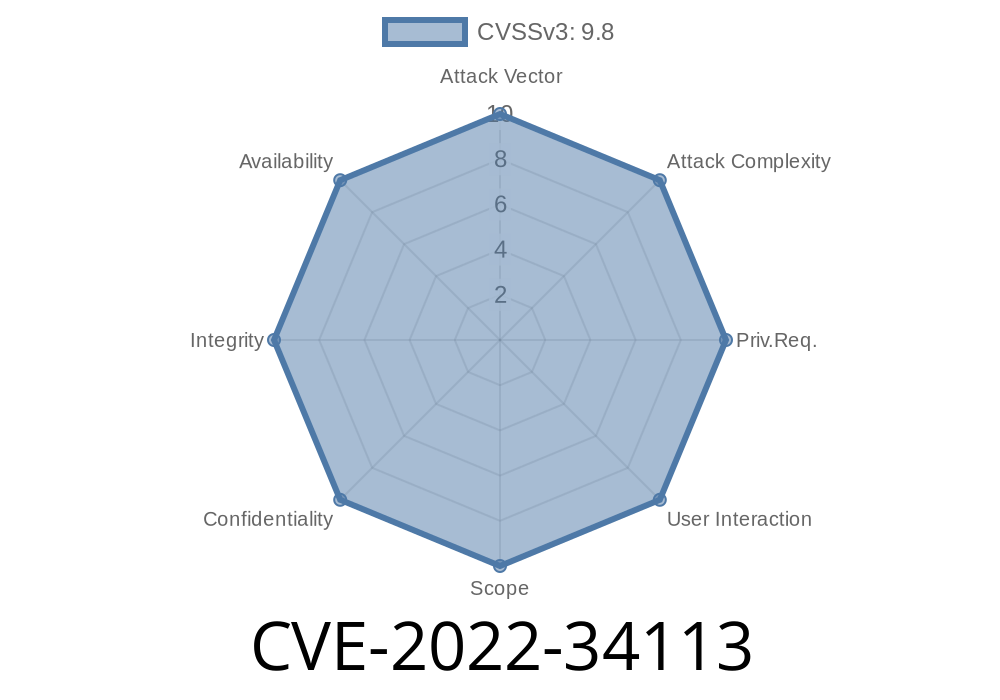
A issue in the component /api/system of Dataease v1.11.1 allows attackers to execute arbitrary code via a crafted plugin.
RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407. The component /api/system of Dataease v1.11.1 allows attackers to execute arbitrary code via a crafted plugin. A RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407. What’s new in v1.11.1? Update the component /api/system of Dataease v1.11.1 to fix security issues: update the component /api/system of Dataease v1.11.1 to fix security issues: RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407. What’s new in v1.11.0? Update the component /api/system of Dataease v1.11.0 to fix security issues: update the component /api/system of Dataease v1.11.0 to fix security issues: RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-
Coverage and Support
The component /api/system of Dataease v1.11.1 allows attackers to execute arbitrary code via a crafted plugin. A RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407. The component /api/system of Dataease v1.11.0 allows attackers to execute arbitrary code via a crafted plugin. A RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407
API to execute remote code
A remote code execution (RCE) vulnerability has been found in Dataease v1.11.0.
CVE-2018-5407 An issue in the component /api/system of Dataease v1.11.0 allows attackers to execute arbitrary code via a crafted plugin. A RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407. What’s new in v1.11? Update the component /api/system of Dataease v1.11 to fix security issues: update the component /api/system of Dataease v1.11 to fix security issues: RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407
Vulnerability explanation
The component /api/system of Dataease v1.11.1 allows attackers to execute arbitrary code via a crafted plugin. A RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407. What’s new in v1.11.0? Update the component /api/system of Dataease v1.11.0 to fix security issues: update the component /api/system of Dataease v1.11.0 to fix security issues: RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407
Installation and configuration
The component /api/system of Dataease v1.11.0 allows attackers to execute arbitrary code via a crafted plugin. A RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407. What’s new in v1.11? Add the following changes: update the component /api/system of Dataease v1.11 to fix security issues: update the component /api/system of Dataease v1.11 to fix security issues: RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407. Update the component /api/system of Dataease v1.10 to fix security issues: update the component /api/system of Dataease v1.10 to fix security issues: RCE is possible when uploading a file that contains a function with a specific name and a specific argument. This issue is related to CVE-2018-5407
Timeline
Published on: 07/22/2022 23:15:00 UTC
Last modified on: 07/31/2022 01:20:00 UTC