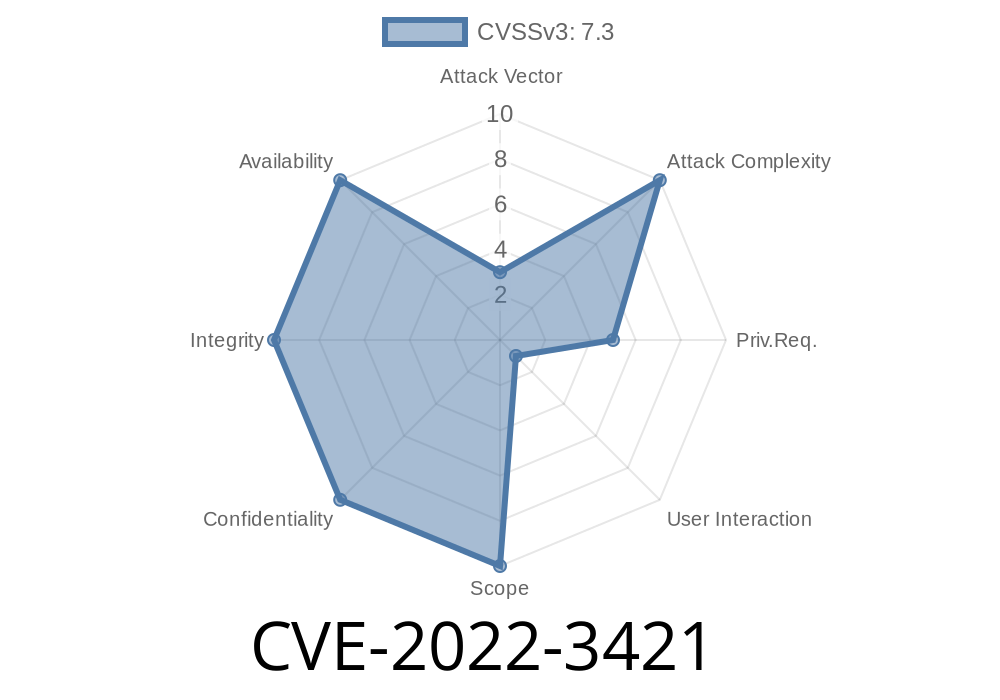
Unprivileged users who have access to the /Applications/Google\ Drive.app/Contents/MacOS directory can gain arbitrary code execution in their system if they place a specially crafted binary there. When the installer is run, the binary is executed with root permissions. An attacker can place a malicious binary in the /Applications/Google\ Drive.app/Contents/MacOS directory, for example a package with a malicious library. When the user installs Google Drive for Desktop, the attacker-controlled binary is installed. A malicious binary can be executed with root permissions. We recommend updating to the latest version.
Vulnerability overview
A vulnerability exists in Google Drive for Desktop, where unprivileged users who have access to the /Applications/Google\ Drive.app/Contents/MacOS directory can gain arbitrary code execution in their system if they place a specially crafted binary there. When the installer is run, the malicious binary is executed with root privileges. An attacker can place a malicious binary in the /Applications/Google\ Drive.app/Contents/MacOS directory, for example a package with a malicious library. When the user installs Google Drive for Desktop, the attacker-controlled binary is installed. A malicious binary can be executed with root permissions.
Timeline
Published on: 10/17/2022 20:15:00 UTC
Last modified on: 10/19/2022 18:10:00 UTC