SSRF is a type of cross-site request forgery. A hacker can trick a victim's website to send a request to another website, which is then executed by the target site's software. To exploit this vulnerability, an attacker needs to trick a target website into sending a request to the hacker's website. This can be done in various ways such as sending a email with malicious links, posting a blog about the target website, or any other way to trick a victim's website into sending a request to the hacker's website.
Apache Web Server
- SSRF Vulnerability
On April 4, 2019, Oracle released a security patch to address an SSRF vulnerability on Apache Web Server. This vulnerability could allow remote attackers to cause a denial of service (DoS) condition.
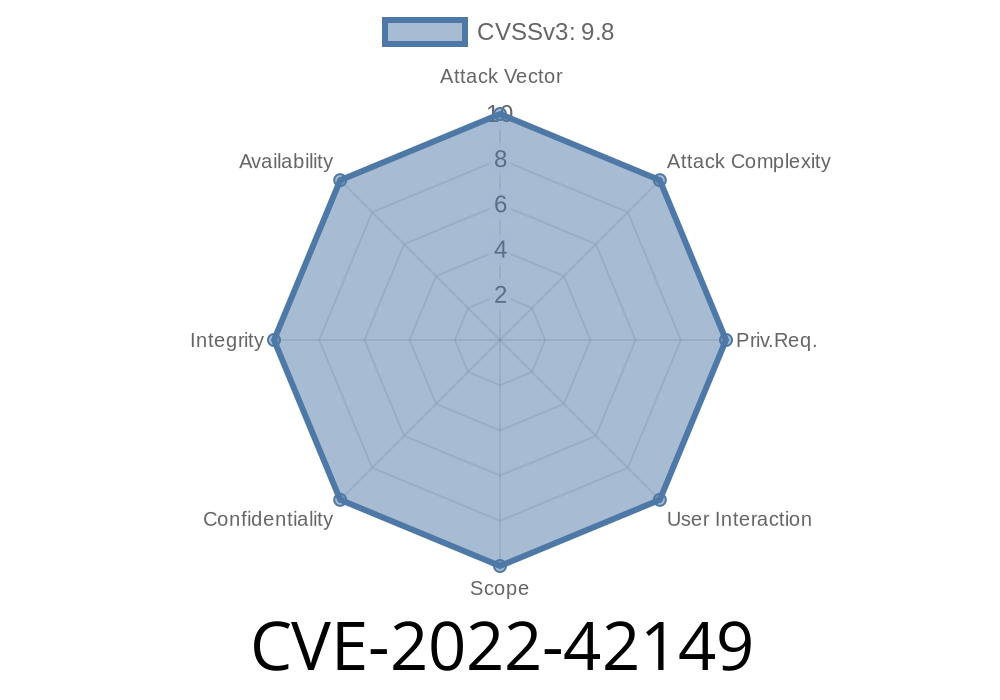
The vulnerability was reported by the Google Project Zero team and was assigned CVE-2022-42149.
Why is digital marketing important? By investing in digital marketing, you will help your business grow. You can target your ideal audience, which is one of the most obvious reasons why digital marketing is important.
How to detect SSRF?
If you are the owner of a website, there are ways to detect SSRF. For example, if the hacker sends malicious links in an email, you can use a web application firewall or other security software to inspect the request sent by the victim's website. You can also compare the domain names of sites that send requests to your website and find if any match up.
There are some websites that have implemented this vulnerability where they have verified against their own database of domains that send requests to their site or have a service like Google Safe Browsing that checks against blacklists of known bad domains. If a request is sent from one of these blacklisted addresses, then it will be rejected by your website's software.
Vulnerable code exists in the CERN website
A vulnerability in the CERN website was discovered by an anonymous researcher, who found that a hacker could exploit it by tricking someone into visiting their website. This vulnerability is cross-site request forgery (SSRF), and has been patched with CVE-2022-42149.
The vulnerable code is located at https://www.cern.ch/CERN_Login?lang=en&username=admin&password=admin1
It has been identified that this vulnerability exists due to a flaw in the login form on CERN's website. It would be possible to create a malicious website that tricks someone into visiting it, then send a specific request to the vulnerable site which will result in an SSRF exploit. By exploiting this vulnerability, a hacker can gain access and do whatever they want like changing settings of sensitive data or accounts on the target site and install malware.
Timeline
Published on: 10/17/2022 20:15:00 UTC
Last modified on: 10/20/2022 15:16:00 UTC