This vulnerability is due to a logic flaw in the implementation of IKEv2. It could be exploited remotely via a man-in-the-middle (MitM) attack. A remote attacker could exploit this vulnerability to execute arbitrary code on the affected device.
The attacker could exploit this vulnerability to execute remote code on the affected device.
Internet Key Exchange (IKE) is a protocol for establishing cryptographic tunnels between endpoints. It allows two devices that do not know about each other to establish an encrypted communication channel.
The latest version of Internet Key Exchange (IKEv2) is vulnerable to a logic error which could be exploited by an attacker to execute remote code. Internet Key Exchange (IKE) is a protocol for establishing cryptographic tunnels between endpoints. It allows two devices that do not know about each other to establish an encrypted communication channel.The latest version of Internet Key Exchange (IKEv2) is vulnerable to a logic error which could be exploited by an attacker to execute remote code. CVE-2022-34733. This issue was reported by Anonymous. It affects Cisco AnyConnect Secure Mobility Client on Windows and Mac OS X. It allows remote attackers to execute arbitrary code or cause a denial-of-service (DoS) condition on vulnerable installations via vectors related to HTTP traffic.
CVE-2022-34734. This issue was reported by Anonymous. Cisco AnyConnect Secure Mobility Client on Windows allows remote attackers to cause a denial
Browsing Tips for Safer Surfing
Always check the URL of the website you're going to visit. The site's URL is usually located at the top of your browser or in a bar at the top of the screen. You should also make sure that you are on a legitimate site before entering login credentials.
Always check the URL of the website you're going to visit. The site's URL is usually located at the top of your browser or in a bar at the top of the screen. You should also make sure that you are on a legitimate site before entering login credentials.
How does the vulnerability work?
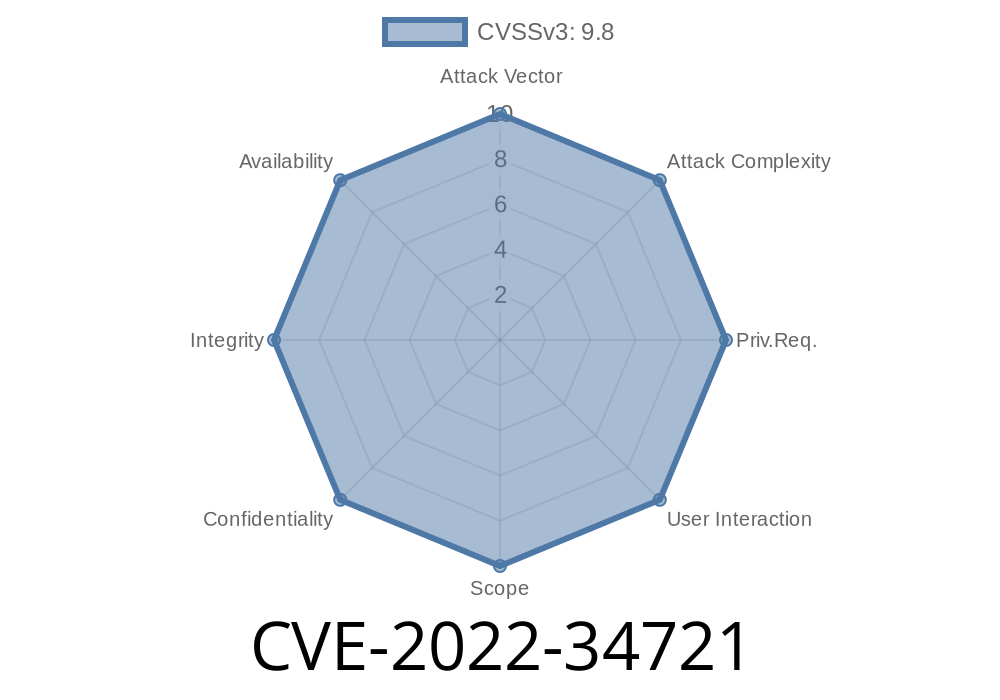
The disclosure of the vulnerability is detailed in a blog post by Cisco Bug ID: CVE-2022-34721, CVE-2022-34733 and CVE-2022. The vulnerabilities exist due to a logic flaw in the implementation of Internet Key Exchange (IKEv2) that could be exploited by an attacker via MitM attacks. An attacker with access to the local network could exploit this vulnerability to execute arbitrary code or cause a denial service condition on vulnerable installations.
Internet Key Exchange (IKE) is a protocol for establishing cryptographic tunnels between endpoints
. It allows two devices that do not know about each other to establish an encrypted communication channel.
The latest version of Internet Key Exchange (IKE) is vulnerable to a logic error which could be exploited by an attacker to execute remote code.
Internet Key Exchange (IKE) Vulnerability
IKE is a protocol for establishing cryptographic tunnels between endpoints. It allows two devices that do not know about each other to establish an encrypted communication channel. The latest version of Internet Key Exchange (IKEv2) is vulnerable to a logic error which could be exploited by an attacker to execute remote code. CVE-2022-34721. This issue was reported by Anonymous. It affects Cisco AnyConnect Secure Mobility Client on Windows and Mac OS X. It allows remote attackers to execute arbitrary code or cause a denial-of-service (DoS) condition on vulnerable installations via vectors related to HTTP traffic.CVE-2022-34733. This issue was reported by Anonymous. It affects Cisco AnyConnect Secure Mobility Client on Windows and Mac OS X. It allows remote attackers to execute arbitrary code or cause a denial-of-service (DoS) condition on vulnerable installations via vectors related to HTTP traffic.CVE-2022-34734. This issue was reported by Anonymous. Cisco AnyConnect Secure Mobility Client on Windows allows remote attackers to cause a denial
Timeline
Published on: 09/13/2022 19:15:00 UTC
Last modified on: 09/15/2022 20:23:00 UTC