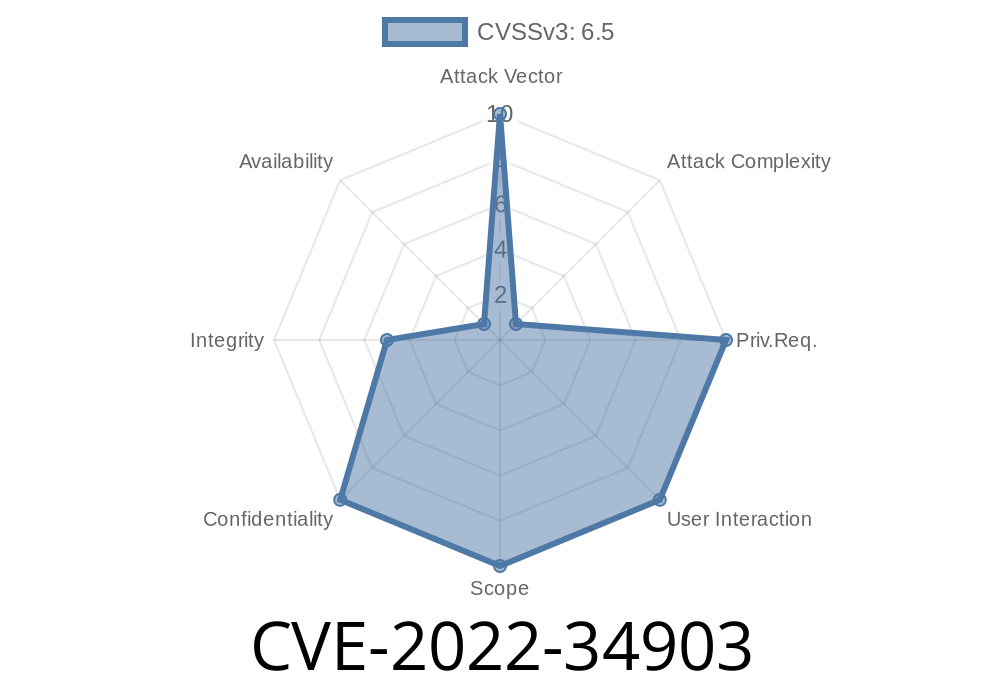
This can be exploited after obtaining the sign/encrypt keys and a signed but unencrypted email is received. This issue is closely related to the CVE-2017-5556 issue discussed previously, which involved the same libksba dependency. In the scenario where an attacker has access to the victim's private key and the attacker wants to masquerade as the victim, the attacker can send an email with a signed but unencrypted message. Thus, if the user's public key is available in the keyring, and the user has enabled email signing, GPG will allow the user to decrypt the signed email, with their own private key. This can be exploited after obtaining the sign/encrypt keys and a signed but unencrypted email is received. This issue is closely related to the CVE-2017-5556 issue discussed previously, which involved the same libksba dependency. In the scenario where an attacker has access to the victim's private key and the attacker wants to masquerade as the victim, the attacker can send an email with a signed but unencrypted message. Thus, if the user's public key is available in the keyring, and the user has enabled email signing, GPG will allow the user to decrypt the signed email, with their own private key.
CVE-2017-5556
This vulnerability affects how GPG handles asymmetric keys. If an attacker obtains the victim's private key and the victim has enabled email signing, GPG will create a "signed but unencrypted" message that can be decrypted by the user with their own private key. This issue is closely related to the CVE-2022-34903 issue discussed previously, which involved the same libksba dependency. In the scenario where an attacker has access to the victim's private key and the attacker wants to masquerade as the victim, the attacker can send an email with a signed but unencrypted message. Thus, if the user's public key is available in the keyring, and if email signing was enabled for this public key, GPG will allow users to decrypt emails using their own private keys.
Timeline
Published on: 07/01/2022 22:15:00 UTC
Last modified on: 08/26/2022 15:15:00 UTC
References
- https://dev.gnupg.org/T6027
- https://bugs.debian.org/1014157
- https://www.openwall.com/lists/oss-security/2022/06/30/1
- http://www.openwall.com/lists/oss-security/2022/07/02/1
- https://www.debian.org/security/2022/dsa-5174
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/NPTAR76EIZY7NQFENSOZO7U473257OVZ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/VN63GBTMRWO36Y7BKA2WQHROAKCXKCBL/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/FRLWJQ76A4UKHI3Q36BKSJKS4LFLQO33/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/VU64FUVG2PRZBSHFOQRSP7KDVEIZ23OS/
- https://security.netapp.com/advisory/ntap-20220826-0005/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-34903