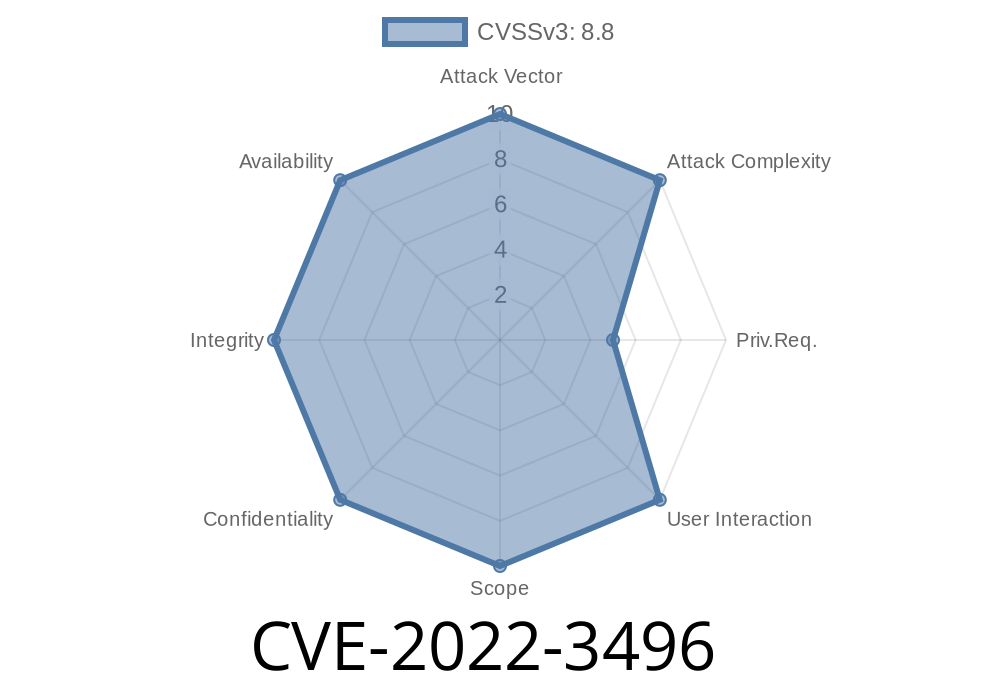
The affected component can be exploited by remote attackers via a request sent to the targeted server. The hacker doesn’t require authentication to exploit this issue. The request needs to be sent over a vulnerable system. The exploit may lead to a takeover of the targeted system. Depending on the nature of the targeted system, it may be possible to obtain access to sensitive data or to create new accounts. The administrator of the vulnerable system must update to the latest version of the application as soon as possible. This will prevent the remote attackers from taking over the system and exploiting the vulnerability.
Vulnerabilities of this type must be classified as critical. It is important to apply the necessary updates as soon as possible. After application, users must be sure to have up-to-date antivirus software installed.
How Did We Find This Vulnerability?
There are a number of methods for the discovery of vulnerabilities, including manual testing and automated scanning. The types of vulnerabilities that are exploited in this instance are those that result from insecure coding practices.
Manual testing can be performed by reviewing the code for potential flaws. This can be done through looking at the source code or by using static analysis tools. Automated scanning is another method that may be used to find vulnerabilities. These programs scan applications to search for security risks, with specific focus on known vulnerabilities such as SQL injection or cross-site scripting flaws. It can also look for any other kind of security risk, including those related to memory corruption, buffer overflows, and privilege escalation. Once a vulnerability is found, it can be confirmed using either manual confirmation or automated tools such as fuzzers.
Summary of The Cisco ASA Vulnerability
In this security advisory, Cisco has disclosed a vulnerability in the ASA that allows hackers to take over vulnerable systems with no authentication. This vulnerability is classified as critical because it allows for a takeover of the targeted system. It was discovered by Cisco, so they have already released an update to address the issue. If you are using the affected product, make sure you have updated your software as soon as possible. This will help to prevent hackers from taking over your system and exploiting the vulnerability.
The affected component can be exploited by remote attackers via a request sent to the targeted server. The hacker doesn’t require authentication to exploit this issue. The request needs to be sent over a vulnerable system. The exploit may lead to a takeover of the targeted system. Depending on the nature of the targeted system, it may be possible to obtain access to sensitive data or create new accounts. The administrator of the vulnerable system must update to the latest version of the application as soon as possible following disclosure. This will prevent remote attackers from taking over and exploiting this vulnerability
Timeline
Published on: 10/14/2022 07:15:00 UTC
Last modified on: 10/15/2022 02:38:00 UTC