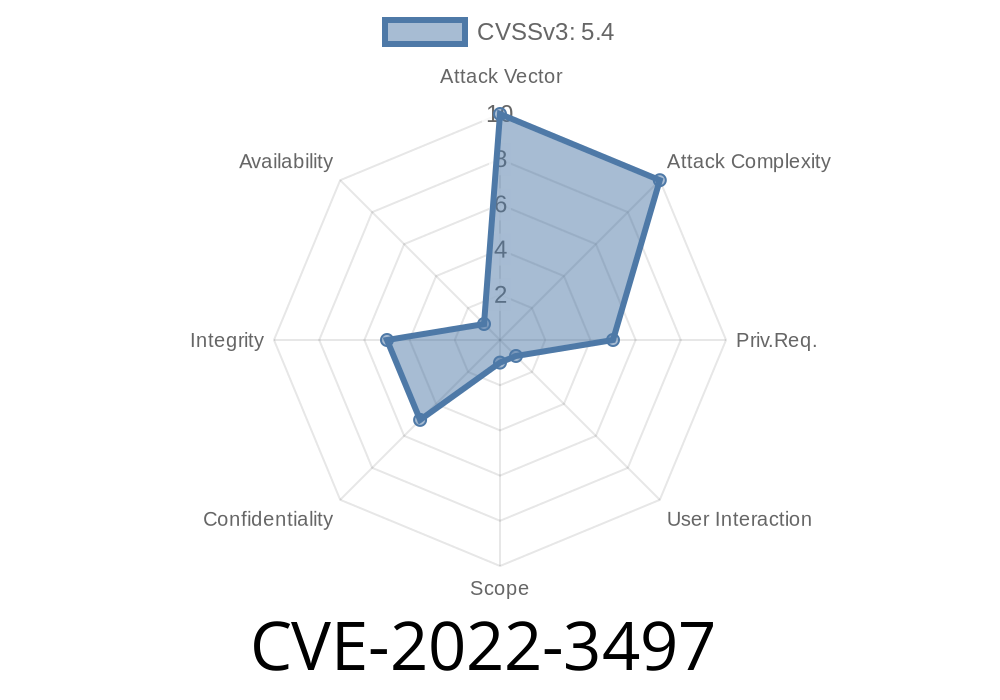
The vendor was notified of the issue on Feb. 7, 2019. At the time of the advisory publication, there was no patch available. It is recommended to update the vulnerable software. Users of the system are advised to review the threat advisory. It should be noted that there areworkarounds available. Users interested in any updates are encouraged to consult the vendor's website.
What information can be exploited by exploiting this vulnerability?
The cross site scripting issue can be exploited to execute arbitrary code on the system of an affected user. This cross site scripting issue can be exploited to steal data from the system of an affected user. This cross site scripting issue can be exploited to launch a phishing attack against the system of an affected user.
What is the typical scenario where this vulnerability can be exploited?
This vulnerability is exposed when user inputs are not validated properly. This vulnerability can be exploited by malicious users to retrieve data from an affected system.
What are some example of common issues that expose this vulnerability?
This vulnerability is exposed when user inputs are not validated properly. This vulnerability can be exploited by malicious users to retrieve data from an affected system. User input should be properly validated before being used during system configuration or software upgrade.
What are some workarounds to protect against this vulnerability?
Change User Input Validation of System Configuration
Ensure that user input is properly validated when changing system configurations.
Block external access to affected systems
If this vulnerability is exposed during an upgrade, it can be blocked by setting the appropriate firewall rules.
Change default browser settings to avoid certain vulnerabilities
This vulnerability can be exploited by malicious users to execute arbitrary code on the system of an affected user. A good way to avoid this vulnerability is to change default browser settings. It is highly recommended not to use the default browser settings.
Configure Application Firewall
Restrict access to untrusted and uncertified users
One of the most common ways to protect against this vulnerability is to restrict access to untrusted and uncertified users.
Another way to protect against this vulnerability is to restrict administrative privileges for all users.
Timeline
Published on: 10/14/2022 07:15:00 UTC
Last modified on: 10/15/2022 02:39:00 UTC