In 2022, a critical security flaw was discovered in the widely-used Awesome Support WordPress plugin. Tracked as CVE-2022-3511, the vulnerability allows low-privileged users—like subscribers—to access and download support ticket exports that they should never see. This exploit relies on an Insecure Direct Object Reference (IDOR) vulnerability.
In this post, I’ll break down what caused the problem, include code snippets, walk you through how an attacker could take advantage of it, and share links to official sources. The goal is to keep it simple and understandable for everyone who uses or manages WordPress sites.
What is the Awesome Support Plugin?
Awesome Support is a full-featured helpdesk and support ticket system for WordPress. It’s been installed over 10,000 times and is popular with businesses that want to handle customer support inside WordPress.
Like many helpdesk tools, the plugin allows users (customers) to submit tickets so that the support staff can manage and answer them. It also includes features to export those tickets, usually for admin-level users.
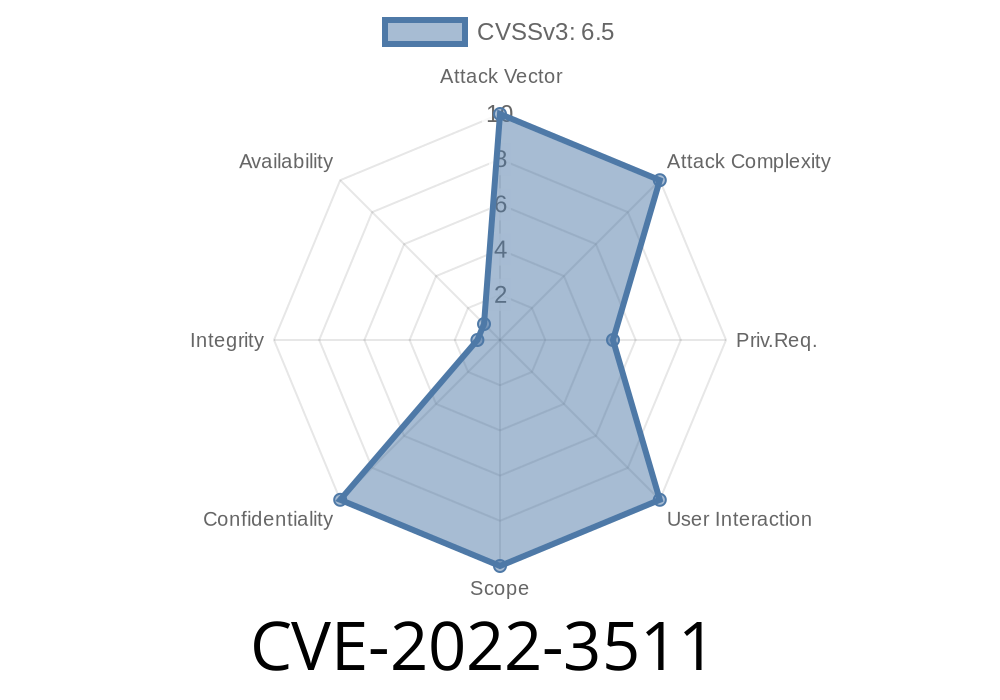
Type: Insecure Direct Object Reference (IDOR)
- CVE: CVE-2022-3511
Severity: Medium to High
- Exploit: Low-privileged users (even subscribers) can download exported support tickets that do *not* belong to them.
How Did It Happen? (Technical Details)
When someone requests to export support tickets, the plugin serves up an archived file (like a CSV, Excel, or ZIP). However, the plugin *did not verify whether the export being downloaded actually belonged to the user making the request*. Instead, it trusted that the requesting user had permission based only on the export’s ID.
An attacker could simply try different IDs (or file names) and download any ticket export—even exports made by admins or for other clients. Classic IDOR!
Simplified Exploit Scenario
Step 1: Low-privileged user (say, a ‘subscriber’) logs in.
Step 2: User notices a download request for an exported ticket archive looks like this
https://example.com/wp-admin/admin-ajax.php?action=awesome_support_export_download&export_id=123
Step 3: User changes the export_id in the URL to another number (like 124, 125, etc.).
Step 4: The server responds by downloading an export created by someone else!
### Code Snippet (Pseudo/PHP Example)
The vulnerable code (simplified for clarity) looks like this
// Vulnerable handler in Awesome Support plugin
function as_export_download_handler() {
$export_id = $_GET['export_id'];
// Fetch the export file based on export_id
$file_path = get_export_file_path_by_id($export_id);
// NO check if current_user_can('manage_support') or owns the export
// Just serve the file
if (file_exists($file_path)) {
header('Content-Type: application/zip');
header('Content-Disposition: attachment; filename="'.basename($file_path).'"');
readfile($file_path);
exit;
}
}
add_action('wp_ajax_awesome_support_export_download', 'as_export_download_handler');
The problem:
There is no verification of whether the user requesting the file is authorized to download it!
Go to the URL pattern for ticket export download and note the export IDs.
3. Increment (or brute-force) export IDs to find and download ALL exported tickets, gaining access to sensitive information belonging to others.
Risks
- Privacy breach: Sensitive ticket data (personal info, support issues, emails, attachments) leaked.
References
- NVD page for CVE-2022-3511
- WPScan Vulnerability Database Entry
- Awesome Support Plugin Download (WordPress.org)
Fix & Mitigation
The issue was patched in Awesome Support version 6.1.2. The developers added proper access controls to ensure that only the user who owns the export (or an administrator) could download a given export.
Patched code might check like so
$current_user_id = get_current_user_id();
$export_owner_id = get_export_owner_id($export_id);
if ($current_user_id !== $export_owner_id && !current_user_can('manage_support')) {
wp_die('Unauthorized');
}
Want to stay safe?
Audit your WordPress users and remove unneeded low-privileged accounts.
- Check for leaks: If you were running a vulnerable version, consider whether sensitive tickets may have been accessed.
Conclusion
CVE-2022-3511 is a textbook case of why direct object reference vulnerabilities are dangerous—in this case, letting any logged-in user access data dumps that should be strictly private. Regularly update your plugins and be wary of custom features that can expose user data without strict checks.
Have questions or want to check your site?
Drop a comment below or reach out to the WordPress security community for help.
Stay safe, and *always* keep your plugins up to date!
Timeline
Published on: 11/28/2022 14:15:00 UTC
Last modified on: 11/30/2022 03:42:00 UTC