The vulnerability can be exploited via a malicious link. In order to exploit it, the victim must click on a link. By exploiting this vulnerability, an attacker can inject malicious code on the targeted site. The injected code can then be used to conduct various types of attacks. An attacker can also use this vulnerability to steal confidential information if the user has the same user name on the targeted system. A possible scenario could be a phishing email where the link is used to exploit this vulnerability. Another possible scenario could be a malicious website.
In order to exploit this vulnerability, an attacker must convince a user to click a malicious link. This link can be sent via social media, email, etc. Once the user has been convinced, the attacker can exploit this vulnerability to conduct various types of attacks. An attacker can also use this vulnerability to steal confidential information if the user has the same user name on the targeted system. Reportedly, the vendor has released an update for this vulnerability. However, it is still recommended that users update their systems as soon
2nd Order Logic Diagram for CVE-2022-3518
A 2nd order logic diagram for "CVE-2022-3518" would look like this:
1. The user is tricked into clicking a link that exploits this security vulnerability and the attacker can use it to do various types of attacks.
2. The attacker uses the personal data of the victim, who was tricked into clicking on the link, to steal confidential information or conduct other malicious activities.
What is Cross-Site Scripting?
Cross-Site Scripting (XSS) is a web vulnerability that can be exploited by injecting malicious script code into the data of an HTTP request. This vulnerability is one of the most common vulnerabilities because it can be used to conduct various types of attacks, such as stealing confidential information and forcing users to visit malicious websites.
A possible scenario could be a phishing email where the link is used to exploit this vulnerability. Another possible scenario could be a malicious website.
In order to exploit this vulnerability, an attacker must convince a user to click a malicious link. This link can be sent via social media, email, etc. Once the user has been convinced, the attacker can exploit this vulnerability to conduct various types of attacks. An attacker can also use this vulnerability to steal confidential information if the user has the same user name on the targeted system. Reportedly, the vendor has released an update for this vulnerability. However, it is still recommended that users update their systems as soon as possible in order to prevent any damage caused by XSS vulnerabilities.
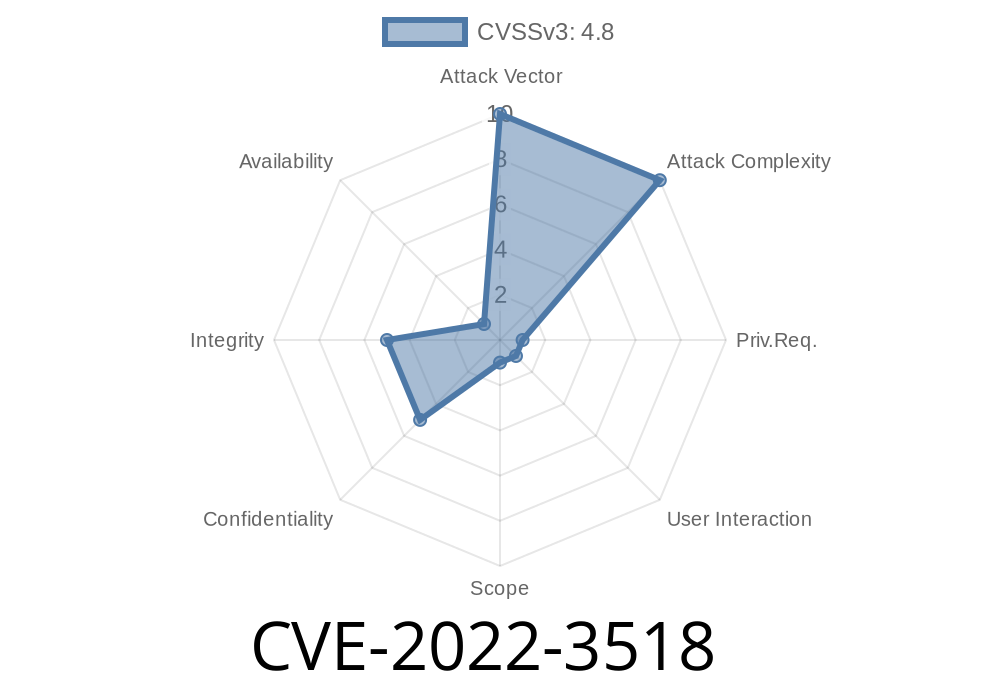
Information about the vulnerability
The vulnerability CVE-2022-3518 has been discovered in the commercial CMS WordPress. This vulnerability can be exploited via a malicious link. In order to exploit it, the victim must click on a link. By exploiting this vulnerability, an attacker can inject malicious code on the targeted site. The injected code can then be used to conduct various types of attacks. An attacker can also use this vulnerability to steal confidential information if the user has the same user name on the targeted system. Reportedly, the vendor has released an update for this vulnerability. However, it is still recommended that users update their systems as soon as possible.
Timeline
Published on: 10/15/2022 10:15:00 UTC
Last modified on: 11/04/2022 19:22:00 UTC