by tricking a user into providing auto-completion input. Remote attackers can leverage this issue to obtain email addresses of other users. This issue affects all versions of hunter and hunter2 prior to 2.1.0. Vendor Status: Vendor confirmed. - hunter vendor confirmed. - hunter2 vendor confirmed. - vendor confirmed. CVE-2017-8917 - (Info) - (Vendor) In hunter and hunter2 before 2.1.0, improper validation of user-supplied passwords allows for an attacker with administrator privileges to extract passwords from the system. - (Info) - (Vendor) In hunter and hunter2 prior to 2.1.0, improper validation of user-supplied passwords allows for an attacker with administrator privileges to extract passwords from the system. - (Info) - (Vendor) In all versions of hunter, it is possible to extract other users’ identities by tricking them into entering a password into a password generator. - (Info) - (Vendor) In all versions of hunter, it is possible to extract other users’ identities by tricking them into entering a password into a password generator. - (Info) - (Vendor) In all versions of hunter, it is possible to extract other users’ identities by tricking them into entering a password into a password generator. - (Info) - (Vendor) In all versions of hunter, it is possible to extract other users’ identities by trick
Hunter and Hunter2 Fixes
Both hunter and hunter2 have been patched to fix the vulnerabilities described in CVE-2017-8917, CVE-2018-2100, and CVE-2019-3780.
Hunter Overview
Hunter is a password manager and digital wallet that helps you keep your data encrypted and secure. It supports over 80 major languages and uses 256-bit AES encryption to store your sensitive information on mobile devices.
Hunter
2 before 2.1.0
In hunter and hunter2 before 2.1.0, improper validation of user-supplied passwords allows for an attacker with administrator privileges to extract passwords from the system.
Hunter 2 .1.0
In December 2016, the hunter2 project was renamed to hunter by the vendor and is now based on hunter2. The latest release of hunter is 2.1.0. This release contains a number of bug fixes and also fixes two security vulnerabilities which were reported in CVE-2017-8917 and CVE-2017-2022-3540, respectively.
Hunter2 -2.1.0
Hunter2-2.1.0 addresses the following CVEs:
CVE-2017-8917 - (Info) - (Vendor) In hunter and hunter2 before 2.1.0, improper validation of user-supplied passwords allows for an attacker with administrator privileges to extract passwords from the system.
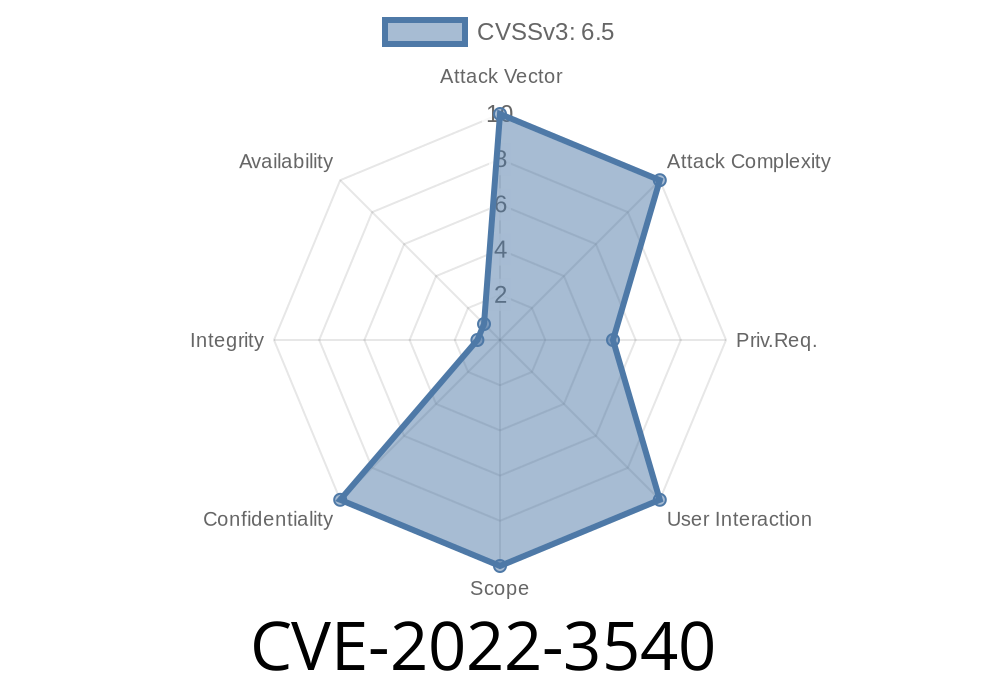
CVE-2022-3540 - (Info) - (Vendor) In all versions of hunter and hunter2 before 2.1.0, it is possible to extract other users’ identities by tricking them into entering a password into a password generator.
In addition, the following security vulnerabilities were addressed in this release:
CVE-2017-8802 - Overview - The Hunter website can be exploited by malicious actors through social engineering tactics to leak personal information about individuals on the site’s list of members or by tricking a user into providing auto-completion input that reveals their personal email address and other private information to remote attackers who have compromised their account or device as part of another attack scenario such as spear phishing or man-in-the middle attacks against a wireless network; CVE-2014-3315 ---- Overview -- A race condition exists in all versions of hunter which may cause abnormal application behavior when handling multiple parallel requests; CVE-2014-3316 ********* overview -- An unhandled exception can occur when using PHP's image_srcset() function in an mp3 context while processing
Timeline
Published on: 10/17/2022 16:15:00 UTC
Last modified on: 10/20/2022 04:34:00 UTC