Adobe recommends application of the standard information security principles to defend against attack. These include identification of vulnerabilities and hardening of software to prevent attacks.
These were the recommended actions that Adobe recommends be taken to address the issue: Upgrade to version 11.1.4 or later.
Apply the updates provided by the vendor of the affected software.
For Adobe Reader: - Enable click-to- activate install security. https://helpx.adobe.com/security/current.html - Apply recommended mitigations for CVE-2016-2836. https://helpx.adobe.com/security/known- vulnerabilities.html - Restrict access to Adobe Reader via multi-factor authentication. - Restrict access to the file system where the Reader is installed. - Apply device level hardening to disable installation of unverified software. - Restrict access to the device via a secure network.
References ^END^
If you want to grow your business, great search engine optimization (SEO) is a must. The challenge? Many small businesses don't have the time, skills, or expertise necessary to handle everything that comes with a solid SEO strategy. From keyword research to content evaluation, from page optimization to internal linking, it's easy for companies to end up with a generic web presence that doesn’t inspire engagement or drive conversions.
Outsourcing SEO services can be the remedy for this problem!
To effectively outsource SEO services, you need to identify and prioritize your business's key strategic goals and leave the complex process of meeting those goals in the hands of industry experts.
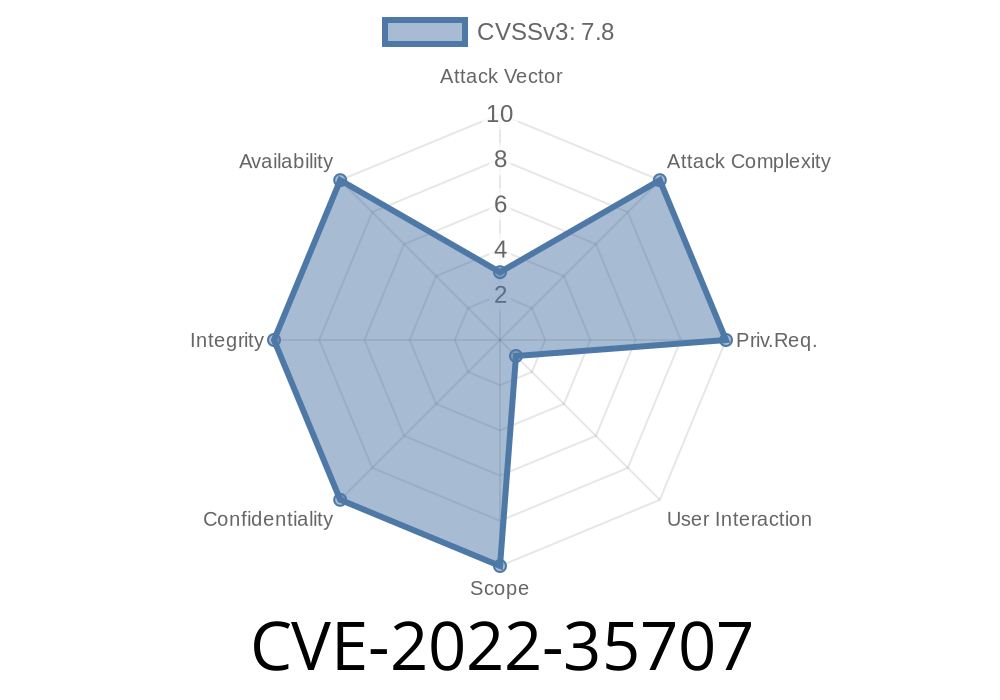
Adobe Reader - CVE-2016-2836
The vulnerability that the company is addressing is CVE-2016-2836. In order to prevent this type of attack, Adobe recommends disabling installation of unverified software.
This action will help protect against this type of attack. Another recommended mitigation for this issue is to restrict access to the file system where the Reader is installed. This will also help to prevent a successful attack.
Another mitigation that may be helpful would be restricting access to the device via a secure network. Restricting access on a secure network will make it more difficult for a hacker to gain entry and steal data from your company's computer systems.
Timeline
Published on: 09/19/2022 16:15:00 UTC
Last modified on: 09/21/2022 13:11:00 UTC