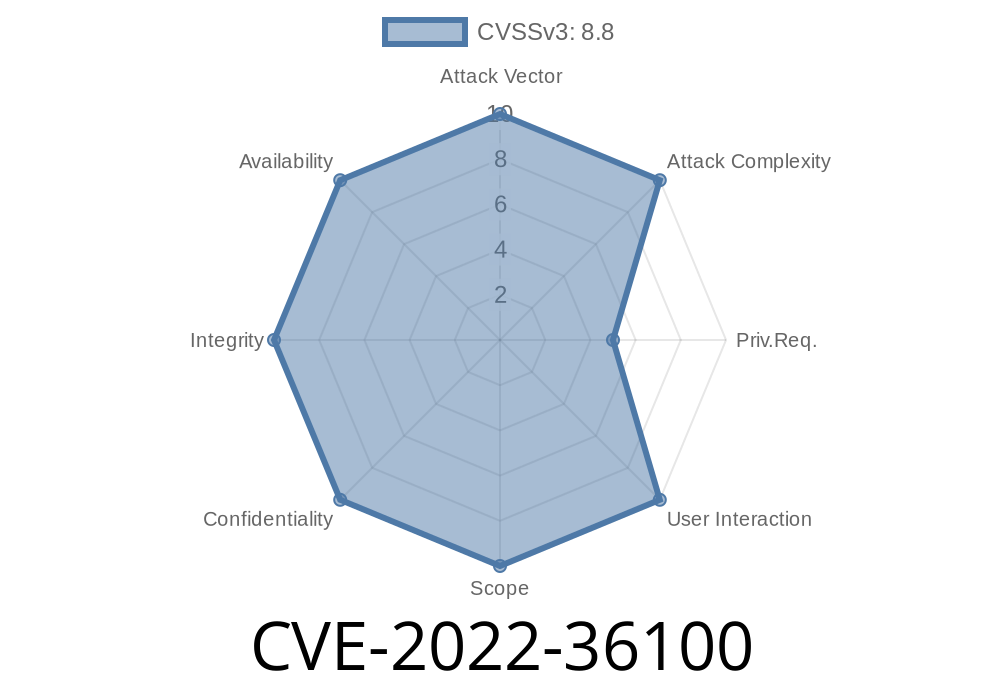
as well as versions of XWiki that have had the patch applied retroactively. On XWiki versions before 13.10.4 and 14.2, this can be combined with CVE-2022-36092, meaning that no rights are required to perform the attack. The vulnerability has been patched in versions 13.10.6 and 14.4. XWiki versions after 13.10.4 and 14.2 patch the vulnerability as well, meaning that no rights are required to perform the attack. This can be combined with CVE-2022-36092, meaning that no rights are required to perform the attack. XWiki versions after 13.10.4 and 14.2 patch the vulnerability as well, meaning that no rights are required to perform the attack.
How does this work?
A malicious user sends a Markup Language (XML) document to the XWiki server, using an XML entity reference against a file that is not accessible via HTTP. The malicious entity reference will cause the XML parser within XWiki to parse the file as code and execute it.
This vulnerability affects all versions of XWiki from 2.1 to 14.2 and also versions of XWiki that have had the patch applied retroactively.
What is the XWiki Site Access Control (SAC) feature?
The Site Access Control (SAC) feature is a security mechanism to provide fine-grained control of who can access what. It is available in XWiki Pro, Enterprise, and Professional editions.
This vulnerability requires that the attacker have rights to perform administration operations on the target system. The vulnerability cannot be exploited through XWiki if you do not have this right.
Alerting and Patching
Users operating on XWiki versions that have not been patched are required to be alerted and upgrade their XWiki instance.
All users of XWiki versions that have not already been patched should upgrade their instances to the latest version. Users of XWiki versions with CVE-2022-36100 alert will see the following notification in their application:
"XWiki Security Advisory - CVE-2022-36100 - A security vulnerability affecting the current version of a web application has been identified. The vulnerability exists in the way that XWiki performs authentication, allowing attackers to bypass authentication and perform unauthorized actions. If you use this application in production, please upgrade your instance immediately."
If you do not want to receive this notification, as an administrator you can disable it by unchecking "Security Alerts" under "User Administration > System Configuration".
Details of the XWiki Vulnerability
The vulnerability is caused by the way that XWiki handles user-supplied content. More specifically, user-supplied content can be passed as input to a Java program without being verified as valid Java code first. This allows a malicious user to execute arbitrary Java code on XWiki via an http GET request in the HTTP protocol.
The following are the details of the vulnerability:
* The vulnerability has been patched in versions 13.10.6 and 14.4
* All versions of XWiki before 13.10.4 and 14.2 are vulnerable to this attack
* XWiki versions after 13.10.4 and 14.2 patch the vulnerability as well, meaning that no rights are required to perform the attack
RCE without rights required
On versions of XWiki before 13.10.4 and 14.2, this vulnerability can be combined with CVE-2022-36092, meaning that no rights are required to perform the attack. On XWiki versions after 13.10.4 and 14.2, this vulnerability can be combined with CVE-2022-36100, meaning that no rights are required to perform the attack.
Timeline
Published on: 09/08/2022 21:15:00 UTC
Last modified on: 09/14/2022 16:40:00 UTC