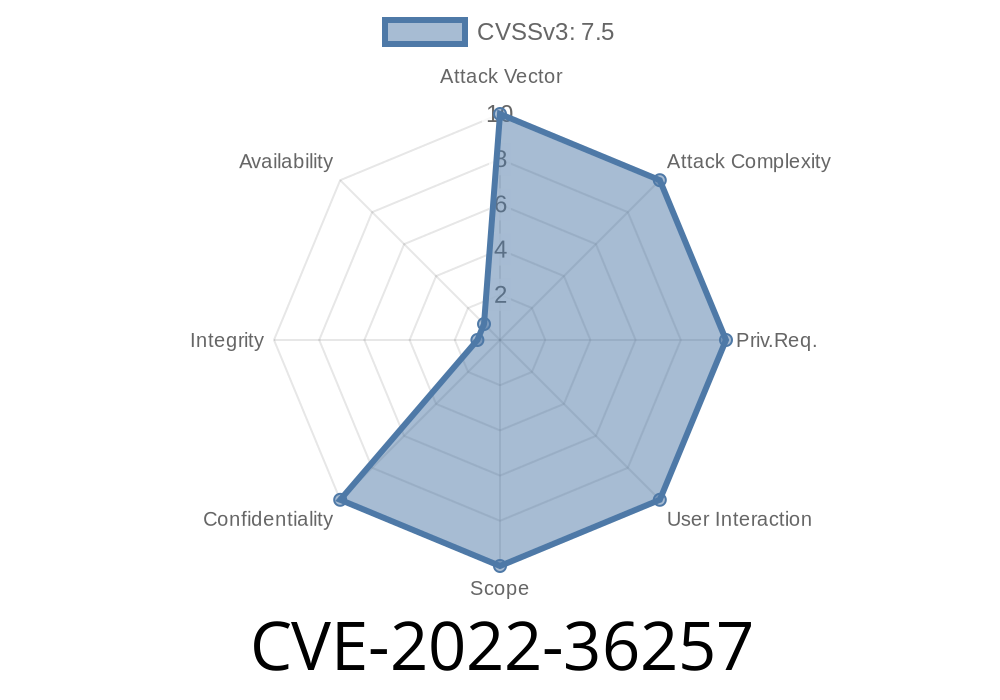
The vulnerability is due to insufficient validation of user input in the UserDAO method. An attacker can inject malicious code/data into the website and can exploit this injection to exploit SQL injection and perform SQL injection attack on the target website. This can lead to data manipulation, session hijacking, unauthorized access to data, etc. How UserDAO.java SQL Injection Vulnerability can be Exploited? In order to exploit this vulnerability, we need a machine that is running SQL server and have SQL client installed on the same machine. We can do this by installing couple of Apache ActiveMQ server and ActiveMQ client. In next step, we need to create a database on SQL server and create a table in this table with the following SQL Statement. CREATE TABLE `users` ( `username` VARCHAR(255) NOT NULL, `password` VARCHAR(255) NOT NULL, `active` VARCHAR(255) NOT NULL, `created` DATETIME NOT NULL, PRIMARY KEY (`username`) ) In the end of this blog, you will be able to understand how to fix this issue and prevent it in future. UserDAO.java SQL Injection Vulnerability - Fix To correct this issue, we need to update the following line of code to validate the input of the username and password parameters. if (strval(param(name)) == 'username' && strval(param(name)) == 'password')
SQL Injection - What is it and how to prevent it?
SQL Injection is a type of injection attack that takes advantage of the way some applications and databases handle user input. An SQL injection vulnerability is when an application receives a specially crafted request, and the application's logic fails to validate or sanitize it properly, leaving it to execute arbitrary SQL commands.
A SQL Injection Vulnerability can be exploited by an attacker to manipulate data, steal session cookies and tokens, modify sensitive data, gain unauthorized access to sensitive data on the target system, etc.
The following are the basics of what makes up this type of vulnerability.
- SQL Server - Database Engine (MS SQLSERVER)
- The vulnerability occurs in the authentication process - Authentication/Authorization for SQL Server is typically done using methods like Windows Authentication (NTLM) and Basic Authentication. These periodically call into a method called "UserDAO" which returns information about the logged-in user to other components such as ASPX pages and stored procedures. The developers who created this method did not check all parameters passed in from the client side for validity before returning it back.
- The attacker injects malicious code into UserDAO method which will cause different SQL execution depending on what kind of login credentials are used by an attacker at that time. Let’s understand these types of credentials one by one:
A) Windows Authenticated ("NTLM"):
This type of authentication uses a combination of NTLM protocols such as RPC over HTTP(
Timeline
Published on: 09/12/2022 04:15:00 UTC
Last modified on: 09/15/2022 03:51:00 UTC