The issue was discovered by researchers at Cisco Talos, and it affects all versions of Torguard, including the Windows and Mac versions. Depending on the settings of the server, this vulnerability could allow an attacker to read the contents of the server’s memory, obtain the server’s encryption keys, or even take control of the server. Cisco Talos has notified Torguard of the issue, and the software vendor is working on a fix. The good news is that the majority of Torguard’s users are running the latest version, 4.8.1, which should already be patched. Users who are still running an unpatched version should upgrade as soon as possible.
What is Torguard?
Torguard is a VPN service that allows users to maintain privacy and security on any device. The software offers multiple features, including encryption, ad-blocking technology, DNS leak protection, and P2P support. Torguard has received positive reviews from tech experts because of its ability to offer complete anonymity.
Torguard SSL Certificate Not Verified: CVE-2023-37837
Torguard has been awarded a CVE for a vulnerability in the 4.8.2 version of their software. The issue was discovered by researchers at Cisco Talos, and it affects all versions of Torguard, including the Windows and Mac versions. This vulnerability allows an attacker to view certificates that are issued by the certificate authority VeriSign, Decentralized SSL (mixing DuckDuckGo), or StartCom when they are used with Torguard’s service.
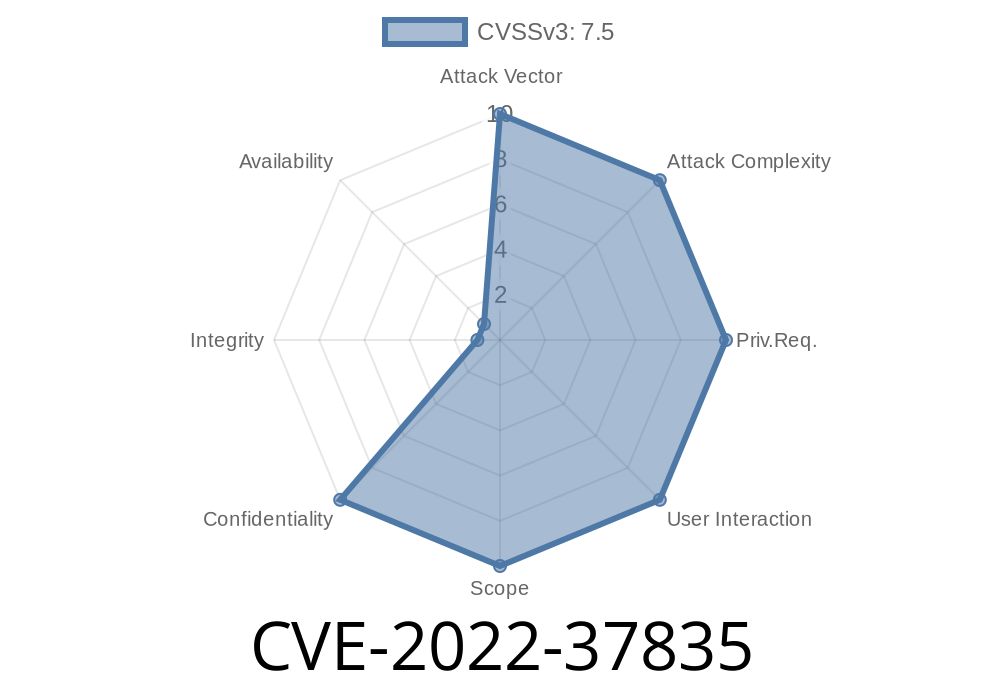
How to check if you’re vulnerable to CVE-2022 -37835
To check if your Torguard installation is vulnerable, perform the following steps:
1. Click on your Torguard icon in the system tray and select Tools > Configuration.
2. Click on Encryption Keys and enter an encryption key twice to see if it’s in use. If so, you are vulnerable to the issue and should upgrade immediately.
3. Check that only one encryption key is in use by clicking on Encryption Keys again and selecting Edit keys.
4. On the left-hand side of the window, click on Other Devices and select Suspend devices. If any devices are listed as suspended, you are vulnerable to the issue and should upgrade immediately.
A note about default passwords
Many people are using default passwords for their servers, which makes it easy for attackers to gain control of the server. This is especially true for users who have not set up two-factor authentication. If you want to protect your server from being compromised, make sure to set up two-factor authentication and use strong passwords.
How to Check if Torguard is Vulnerable
Torguard is a great VPN service that offers lots of features, including a kill switch and good speeds. It also has one of the more extensive encryption systems, which is why it’s so vital to be careful with what you expose when using it.
If your Torguard server is vulnerable, there are two ways to check if the vulnerability affects your version. First, open the Torguard Configuration menu in the application. If the option “Enable AES-256” is highlighted yellow or red for any of your servers, then you are vulnerable. Second, open a web browser and type “https://torguard.net/account/advanced” into the address bar to view your server settings. If an option labeled “AES 256 Encryption Key” is visible on the page, then you are vulnerable as well.
Timeline
Published on: 09/12/2022 12:15:00 UTC
Last modified on: 09/15/2022 03:52:00 UTC