To be authenticated, a user needs to go through the process of adding a new credential to his/her user profile, which means the user has to be logged in and have a sufficiently active session. If a user is not logged in and does not have an active session, the user will be logged out, and the request will fail. This can be exploited by an attacker who, for example, sends malicious V3 API requests to the system with credentials belonging to a non-existent user and activates that user’s session, as the user gets redirected to the attacker’s site. (For example, the attacker’s site may have a login form that is disguised to look like the login form of the target application, and the attacker may have altered the request’s URL at this stage to send the request to the login form of the target application. An example of such a scenario is described here.) In addition to this, V3 API requests are vulnerable to a unique series of SQL injection attacks. A user can be exploited by an attacker who, for example, sends malicious V3 API requests to the system with credentials belonging to a non-existent user and activates that user’s session, as the user gets redirected to the attacker’s site. (For example, the attacker’s site may have a login form that is disguised to look like the login form of the target application, and the attacker may have altered the request’s
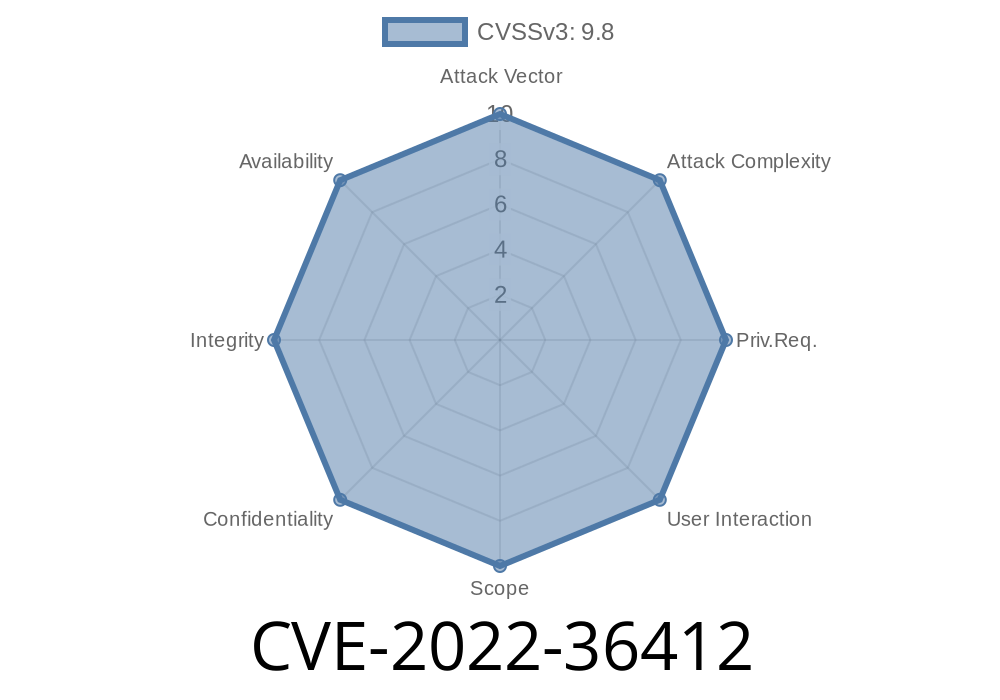
Vulnerability overview
1) An attacker may send a malicious V3 API request to the system with credentials belonging to a non-existent user and activates that user’s session
2) In addition to this, V3 API requests are vulnerable to a unique series of SQL injection attacks. A user can be exploited by an attacker who, for example, sends malicious V3 API requests to the system with credentials belonging to a non-existent user and activates that user’s session, as the user gets redirected to the attacker’s site. (For example, the attacker’s site may have a login form that is disguised to look like the login form of the target application, and the attacker may have altered the request’s URL at this stage to send the request to the login form of the target application.)
The vulnerability is found in Ektron v3 Web Services RESTful interface. The vulnerability affects every stage of authentication on Ektron v3 Web Services RESTful interface.
Vulnerability overview:
There are two different vulnerabilities found in the v3 API, which can be exploited by an attacker to gain unauthorized access to an administrator’s account.
The first vulnerability is that all V3 API requests are vulnerable to a unique series of SQL injection attacks. A user can be exploited by an attacker who, for example, sends malicious V3 API requests to the system with credentials belonging to a non-existent user and activates that user’s session, as the user gets redirected to the attacker’s site. (For example, the attacker’s site may have a login form that is disguised to look like the login form of the target application, and the attacker may have altered the request’s URL at this stage to send the request to the login form of the target application. An example of such a scenario is described here.) In addition to this, V3 API requests are vulnerable to a unique series of SQL injection attacks.
V3 API SQL Injection
The vulnerability is caused by the way the system handles requests. The request handling process takes place in two different steps: first, the user logs in, and then he/she receives a request from the system. In step two, after a user’s session is activated, the system sends confirmation to him/her that the session is active. However, in this second step of the process, there is no mechanism that would make sure that SQL injection attacks cannot be performed on V3 API requests.
Timeline
Published on: 07/26/2022 14:15:00 UTC
Last modified on: 08/02/2022 20:05:00 UTC