When visiting this path, the user’s input is validated against the standard parameter “id” to ensure that only numbers are entered.
However, the id parameter is actually a part of the SQL query, so any malicious user input can actually be executed in the SQL query, allowing for SQL injection. An attacker can leverage this vulnerability to execute arbitrary SQL commands and steal users’ data.
Moreover, the WordPress Book Details screen allows users to search for any book by inputting an id value in the search box.
This allows attackers to exploit the fact that the id parameter is part of the SQL query to obtain sensitive information about WordPress installations by using this search feature.
How to exploit the vulnerability?
An attacker can exploit this vulnerability by submitting their own id value to the search feature, then using the SQL query to access sensitive information about WordPress installations.
Example of vulnerable code:
Vulnerability discovery and exploitation techniques PCI-DSS
Certificate Transparency
Bug Bounty
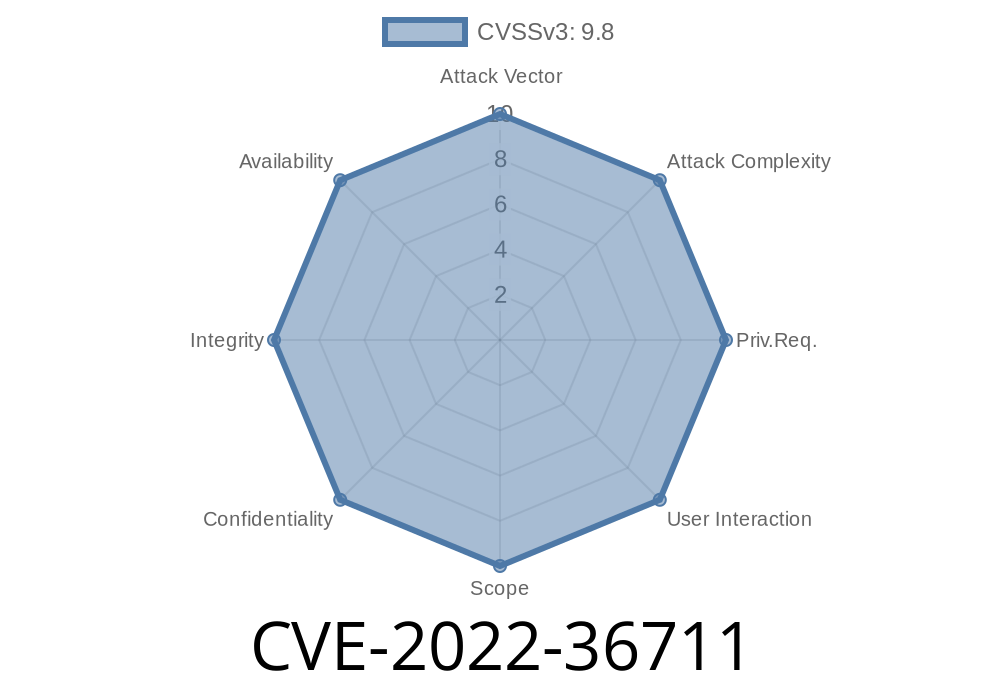
Wordpress SQL Injection Vulnerability - CVE-2023 -36711
When visiting this path, the user’s input is validated against the standard parameter “id” to ensure that only numbers are entered.
However, the id parameter is actually a part of the SQL query, so any malicious user input can actually be executed in the SQL query, allowing for SQL injection. An attacker can leverage this vulnerability to execute arbitrary SQL commands and steal users’ data.
Moreover, the WordPress Book Details screen allows users to search for any book by inputting an id value in the search box.
This allows attackers to exploit the fact that the id parameter is part of the SQL query to obtain sensitive information about WordPress installations by using this search feature.
Timeline
Published on: 08/30/2022 00:15:00 UTC
Last modified on: 09/01/2022 06:51:00 UTC