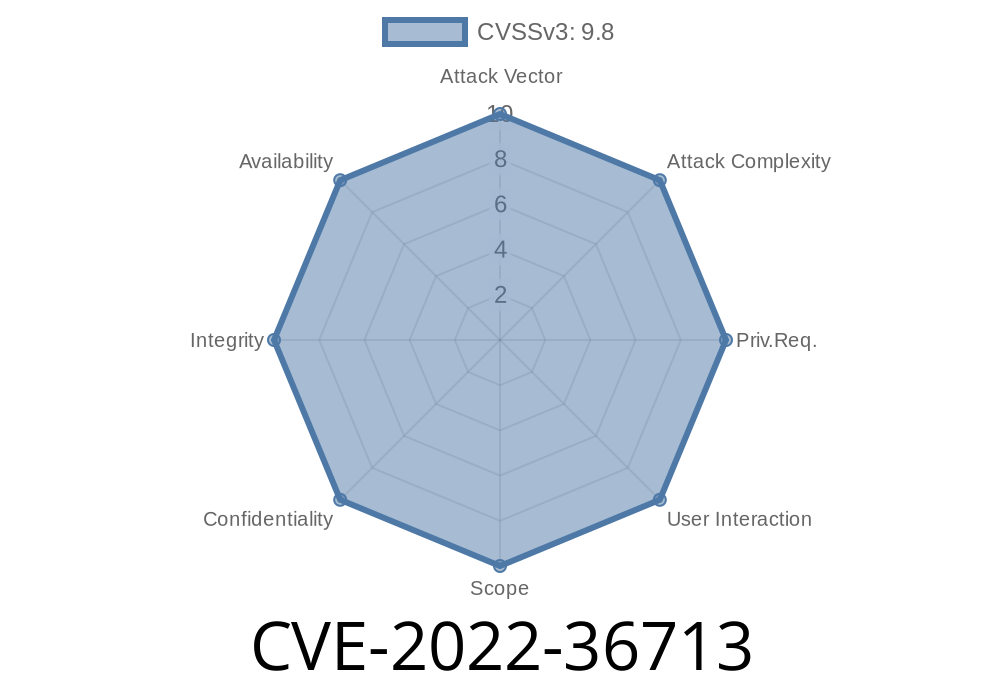
A user with knowledge of SQL injection can exploit this to execute arbitrary SQL commands, bypassing the application's validation mechanisms. In a scenario where another user does not have knowledge of SQL injection, the application will appear to function correctly.
Additionally, the application was found to be vulnerable to a XSS attack. This could be exploited by sending a malicious email to a recipient and having the user view the email in a webmail client. The malicious link in the email would then execute actions in the application via the user's session.
It was discovered that the application's 'Create' page did not have a CSRF protection mechanism. This would allow an attacker to perform a man-in-the-middle attack by tricking a user into logging in via a malicious URL. The attacker could then use this session to perform actions in the application via the user's session.
In addition to the above issues, the application was found to be vulnerable to a remote code execution vulnerability via the admin interface. This could be exploited by a malicious user by having access to the application's backend.
It was discovered that the application did not have a proper error handling mechanism in place. In a scenario where an error occurred during the application's operations, an error page would be displayed instead of the intended one
Look for common pitfalls in a database
-driven application
Database-driven applications are typically written to be easy to use and very flexible, but they can have a downside. These applications often contain many layers of abstraction to make them easier for beginners to learn, but this also makes them vulnerable when it comes to user input.
A database-driven application is vulnerable if the user input or validation is not properly handled. For example, users who know about SQL injection can exploit this vulnerability in order to execute arbitrary SQL commands. In a scenario where another user does not have knowledge of SQL injection, the application will appear to function correctly.
Additionally, the application was found to be vulnerable to a XSS attack. This could be exploited by sending a malicious email to a recipient and having the user view the email in a webmail client. The malicious link in the email would then execute actions in the application via the user's session.
Bypassing the Code
A user with knowledge of SQL injection could exploit this vulnerability to bypass the application's validation mechanisms and execute arbitrary SQL commands, bypassing the application's validation mechanisms.
References:
- https://www.infosecurity-magazine.com/news/new-study-explores-5-ways-search-engine-optimization
6 Reasons Why Digital Marketing Is Important
Timeline
Published on: 08/30/2022 00:15:00 UTC
Last modified on: 09/01/2022 06:58:00 UTC