A flaw in the way the Linux kernel handled non-BLK devices when unloading may lead to information leak or, in some cases, potential local privilege escalation.
A flaw in the way the Linux kernel handled non-BLK devices when unloading may lead to information leak or, in some cases, potential local privilege escalation. IBM AIX could allow a local user with the CAP_SYS_RAWIO capability to gain root privileges.
A flaw in the way the Linux kernel handled non-BLK devices when unloading may lead to information leak or, in some cases, potential local privilege escalation. IBM AIX could allow a local user with the CAP_SYS_RAWIO capability to gain root privileges. A flaw in the Linux kernel may allow an unprivileged local user to gain root privileges.
A flaw in the Linux kernel may allow an unprivileged local user to gain root privileges. A vulnerability in IBM AIX may allow a local attacker with the ability to issue CAP_SYS_RAWIO to gain root privileges.
A vulnerability in IBM AIX may allow a local attacker with the ability to issue CAP_SYS_RAWIO to gain root privileges. A vulnerability in the vmemmap_alloc_ns() function in the Linux kernel may allow a local user with the ability to issue CAP_SYS_RAWIO to gain root privileges.
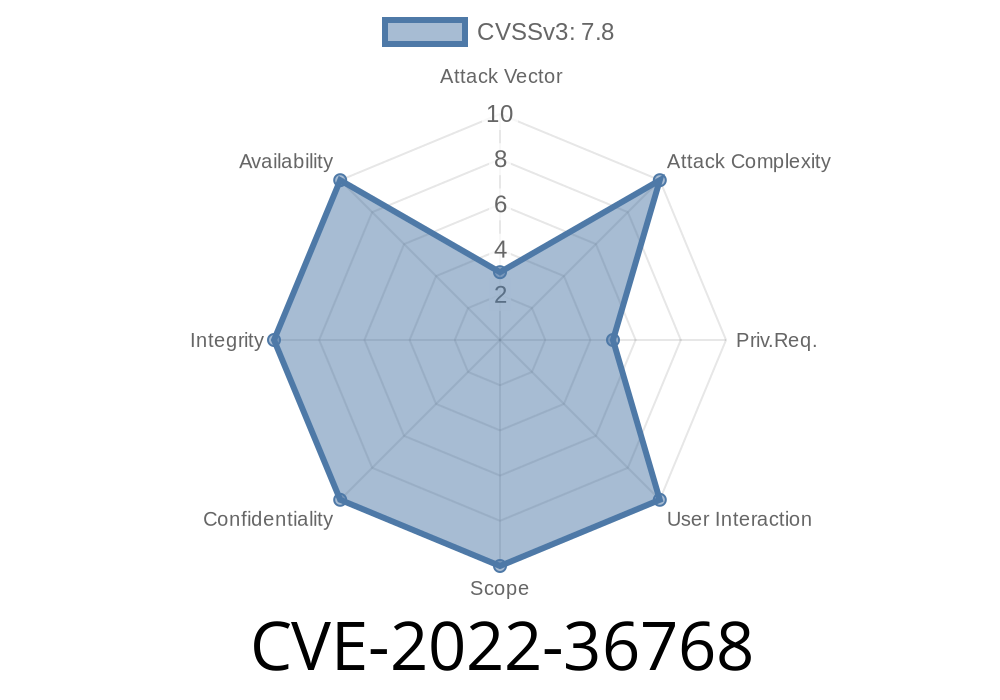
A vulnerability in the vmemmap_alloc_ns()
Linux Kernel
Non-BLK Device Unloading Information Leak
A flaw in the way the Linux kernel handled non-BLK devices when unloading may lead to information leak or, in some cases, potential local privilege escalation. IBM AIX could allow a local user with the CAP_SYS_RAWIO capability to gain root privileges.
A flaw in the way the Linux kernel handled non-BLK devices when unloading may lead to information leak or, in some cases, potential local privilege escalation. A vulnerability in IBM AIX may allow a local attacker with the ability to issue CAP_SYS_RAWIO to gain root privileges.
Vulnerable package(s)
A vulnerability in the vmemmap_alloc_ns() function in the Linux kernel may allow a local user with the ability to issue CAP_SYS_RAWIO to gain root privileges. A vulnerable package is: KERNEL-3.10.0-327.bpo.2-amd64
Authentication, Authorization and Session Management
There are so many benefits to implementing a cloud-based network, but one of the most significant is security. Cloud computing places trust in the provider, not a user or company. So, how do you make sure this trust is well-earned?
A vulnerability in the vmemmap_alloc_ns() function in the Linux kernel may allow a local user with the ability to issue CAP_SYS_RAWIO to gain root privileges
A vulnerability in the vmemmap_alloc_ns() function in the Linux kernel may allow a local user with the ability to issue CAP_SYS_RAWIO to gain root privileges. A flaw in IBM AIX may allow a local attacker with the ability to issue CAP_SYS_RAWIO to gain root privileges.
Should I patch?
Patch or not?
A vulnerability in the vmemmap_alloc_ns() function in the Linux kernel may allow a local user with the ability to issue CAP_SYS_RAWIO to gain root privileges. Patch only if your system is vulnerable.
A vulnerability in the vmemmap_alloc_ns() function in the Linux kernel may allow a local user with the ability to issue CAP_SYS_RAWIO to gain root privileges. Patch only if your system is vulnerable. A flaw in IBM AIX could allow a local user with the CAP_SYS_RAWIO capability to gain root privileges. Patch only if your system is vulnerable.
Timeline
Published on: 09/13/2022 21:15:00 UTC
Last modified on: 09/16/2022 02:57:00 UTC