An attacker can also inject other commands into the URL, such as /install, /upgrade, /reboot, /shutdown, /restart, /sk, /scom, /sfl, /sfr, /siz, /sx, /sxl, /sxr, /sxw, /sz, /szx, /szxw, /szx, /szxd, /szxdl, /szxdw, /szxf, /szxr, /szxs, /szxsr, /szxsx, /szxsxr, /szxsxr, /szxsxr, /szxsxr, /szxsxr, /szxsxr, /szxsxr, /szxsxr, /szxsxr, /szxsxr, /szxsxr, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /sx, /s
Install Command Injection /scom
/scom
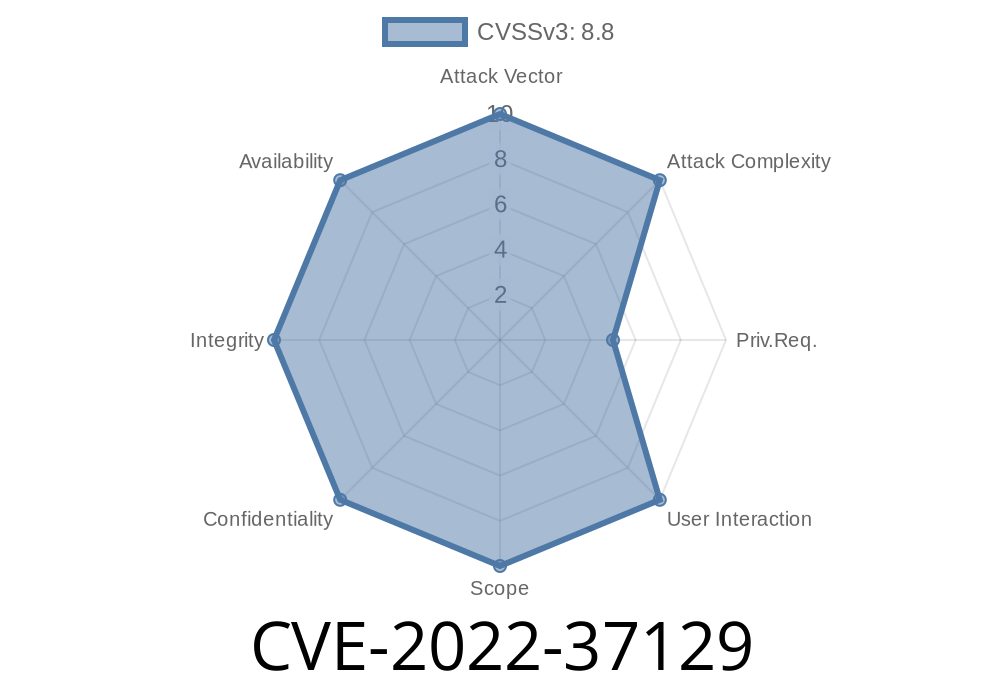
This command injection vulnerability may allow an attacker to execute commands on the affected system without authentication. This vulnerability is rated critical because it could be exploited remotely without authentication, and allows attackers to gain elevated privileges on a vulnerable system.
Vulnerability: Incorrect access control in URL parsing
A vulnerability in the way that the URL parsing function of the HTTP protocol handles URLs with an incorrect number of slashes could allow an attacker to cause a denial-of-service condition by causing the server to consume a large amount of resources.
Timeline
Published on: 08/31/2022 23:15:00 UTC
Last modified on: 09/02/2022 23:26:00 UTC