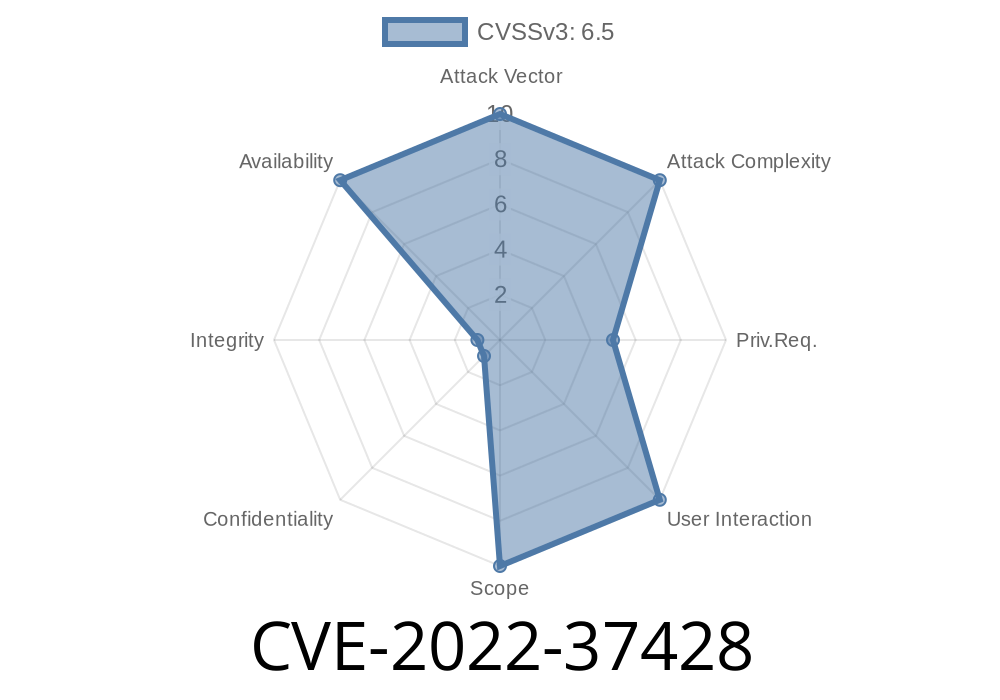
This issue has been patched in these releases. This issue has been patched in these releases. The DNS protocol is designed to be stateless and decentralized. Any data that needs to be persisted should be done outside of DNS. If a DNS server is subject to a denial of service, this can have severe consequences.
Concerns have been raised with the DNS protocol recently as it is prone to state-level attacks. The DNS protocol is stateless and decentralized. If a DNS server is subject to a denial of service attack, this can have severe consequences. This has been demonstrated with the recent global takedown of the DNS provider Dyn. A large number of queries coming from a single source can easily exhaust the resources of a DNS provider. In such a situation, a server that is being targeted with a denial of service attack can easily crash, resulting in a serious outage for the targeted server. When a server is being targeted with a denial of service attack, it is critical that the server does not crash.
What is a DNS Denial of Service Attack?
A denial of service (DoS) attack is an attempt to make a system resource unavailable for legitimate users. An attacker may try to deny service by flooding the targeted server or network connection with superfluous information, thus preventing it from responding to valid traffic.
A DNS denial of service attack is when a server that has been targeted with a DoS attack is unable to respond to valid queries because there are too many queries coming in. This can cause the targeted server to crash, resulting in a large-scale outage for the targeted server. The target should therefore not be one of the servers that are being used during a DoS attack.
What is a DNS Denial of Service?
A denial of service (DoS) is an attempt to make a computer resource unavailable to its intended users. A DoS attack typically involves overloading a target machine with more traffic than it can handle, usually by sending a large amount of useless communication in the form of a flood of requests.
In the case of DNS, a denial of service attack is when an attacker sends a large number of queries to a single target server trying to crash it and render the site inaccessible. As mentioned before, this has been demonstrated by the recent takedown of Dyn. The attacker sent an extremely high number of queries from one source in order to overload the server and force it offline. This is why it is critical that any targeted server does not crash as this could have severe consequences for all websites hosted on that server.
DNS Denial of Service (DoS) Protection
To avoid this, some DNS providers are adding special protections in their software that can detect if a server is overloaded. They do this by monitoring the load on the DNS server, and when it gets too heavy, they automatically throttle all incoming queries. This is a more sophisticated protection mechanism than what was previously described in RFC 4389 and as such is not considered “DoS” protection.
DNS Protocol
The DNS protocol is designed to be stateless and decentralized. Any data that needs to be persisted should be done outside of DNS. If a DNS server is subject to a denial of service, this can have severe consequences.
Concerns have been raised with the DNS protocol recently as it is prone to state-level attacks. A large number of queries coming from a single source can easily exhaust the resources of a DNS provider. In such a situation, a server that is being targeted with a denial of service attack can easily crash, resulting in serious outage for the targeted server. When a server is being targeted with a denial of service attack, it is critical that the server does not crash.
DNS Stateless Operation
& How This Affects Security
DNS is designed to be stateless and decentralized. The DNS protocol is designed to operate without any sort of centralized authority. In order to ensure the security of DNS, there are no central authorities that can make changes or intercede in the operation of DNS servers. Centralized authorities would need to be able to implement changes in DNS servers, which is not possible with the current architecture of DNS. Any data that needs to be persisted should be done outside of the DNS protocol. If a server becomes compromised and has its data stolen, this can have severe consequences for the entire network.
Timeline
Published on: 08/23/2022 17:15:00 UTC
Last modified on: 09/01/2022 12:15:00 UTC
References
- https://docs.powerdns.com/recursor/security-advisories/powerdns-advisory-2022-02.html
- https://docs.powerdns.com/recursor/lua-config/protobuf.html
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/FXSREJKTT6RNE3GXQENQ4R4HS37UNSPX/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-37428