These upgrades are available to customers through the Internet Provisioning Portal. Customers should upgrade their devices as soon as possible to prevent possible exploitation of these vulnerabilities. Additionally, these vulnerabilities are also addressed in the following releases: ArubaOS 10.4.x: 10.4.6.17 and below; ArubaOS 10.5.x: 10.5.3.5 and below; ArubaOS 10.6.x: 10.6.0.28 and below; ArubaOS 10.7.x: 10.7.1.14 and below; ArubaOS 10.8.x: 10.8.1.1 and below; ArubaOS 10.9.x: 10.9.0.1 and below; ArubaOS 10.10.x: 10.10.0.6 and below; ArubaOS 11.0.x: 11.0.0.0 and below. There are buffer overflow vulnerabilities in multiple underlying services that could lead to unauthenticated remote code execution by sending specially crafted packets destined to the PAPI (Aruba Networks AP management protocol) UDP port (8211). Successful exploitation of these vulnerabilities results in the ability to execute arbitrary code as a privileged user on the underlying operating system of Aruba InstantOS 6.4.x: 6.4.4.8-4.2.4.20 and below; Aruba InstantOS 6.5.x: 6
New Features and Functionality
- Enhanced Guest WLANs (WiFi) - Customer can now configure which WLAN device guests will use. This provides a layer of security without needing to have an 802.1x configuration or certificates in effect.
- Mobility-as-a-Service (MaaS) - Provides a centralized, scalable and secure mobility solution with self service capabilities that are easy to automate and manage.
- Aruba RF360 - The new Aruba RF360 platform offers up to 10 Gbps of bandwidth per radio controller and is optimized for 3G/4G/5G wireless deployments.
- Recovery Manager - Providing the ability to quickly recover from disasters such as flooding, fire, power outages and more.
Description
While ArubaOS versions 6.4.x, 6.5.x, and 6.6.x address the vulnerabilities in these releases, there are no fixes available for ArubaOS versions 7.0-7.1 and 11.0-11.1.
Aruba InstantOS versions 6.3-6.5 address the vulnerabilities in these releases, but there is no fix available for Aruba InstantOS version 7 that addresses this vulnerability.
References https://www.arubanetworks.com/blog/aruba-security-bulletins
https://www.arubanetworks.com/blog/aruba-security-bulletins
https://www.arubanetworks.com/blog/rfc7230
Vulnerability Description
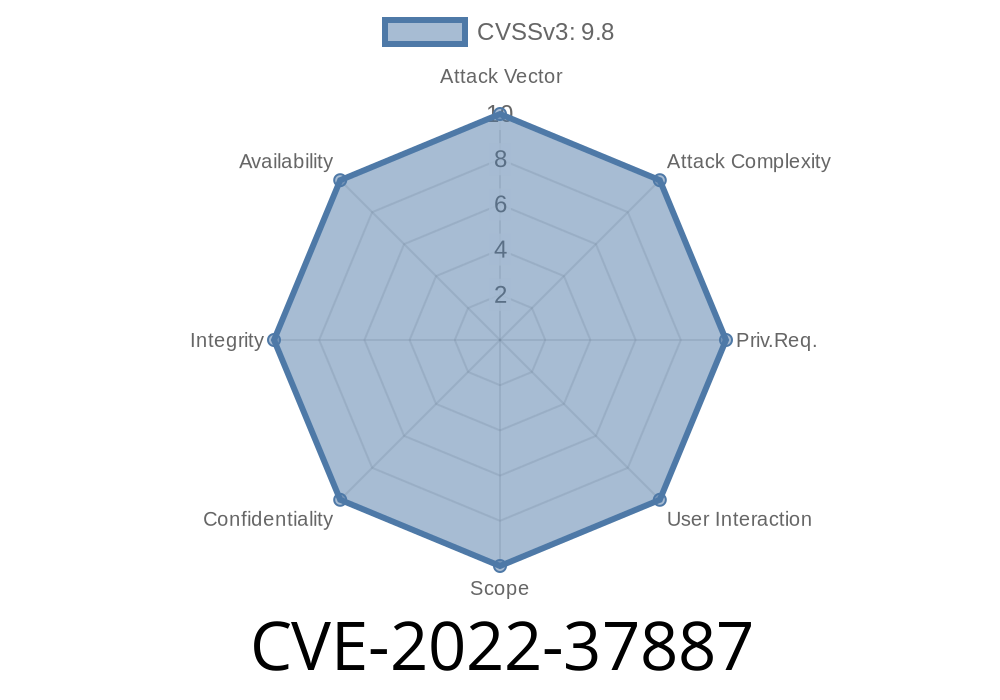
Buffer overflow vulnerabilities in multiple underlying services that could lead to unauthenticated remote code execution by sending specially crafted packets destined to the PAPI (Aruba Networks AP management protocol) UDP port (8211). Successful exploitation of these vulnerabilities results in the ability to execute arbitrary code as a privileged user on the underlying operating system.
Timeline
Published on: 10/07/2022 18:15:00 UTC
Last modified on: 10/11/2022 17:48:00 UTC