Users are advised to upgrade their systems as soon as possible to mitigate the risk of exploitation. A list of the upgrade instructions can be found on the Aruba website. ArubaOS 10.3.1 addresses this security vulnerability. Upgrade instructions can be found on the Aruba documentation website. Users are advised to upgrade their systems as soon as possible to mitigate the risk of exploitation. A list of the upgrade instructions can be found on the Aruba website. ArubaOS 10.3.1 addresses this security vulnerability. Upgrade instructions can be found on the Aruba documentation website.
Impact Aruba has released upgrades for Aruba InstantOS that address this security vulnerability. Users are advised to upgrade their systems as soon as possible to mitigate the risk of exploitation. A list of the upgrade instructions can be found on the Aruba website.
Summary
Aruba has released upgrades for Aruba InstantOS that address this security vulnerability. Users are advised to upgrade their systems as soon as possible to mitigate the risk of exploitation.
Users are advised to upgrade their systems as soon as possible to mitigate the risk of exploitation. A list of the upgrade instructions can be found on the Aruba website. ArubaOS 10.3.1 addresses this security vulnerability. Upgrade instructions can be found on the Aruba documentation website.
What is the Aruba Instant Access Controller?
The Aruba Instant Access Controller (IAC) is a special controller that resides on the ArubaOS operating system. It provides features such as support for 802.1X-based authentication and protection against credential theft at the wired and wireless security levels. The IAC also manages multiple 802.11a/b/g/n networks, including virtual access points that are configured to use one or more of the physical WLANs in the network.
Impact Aruba has released upgrades for Aruba InstantOS that address this security vulnerability. Users are advised to upgrade their systems as soon as possible to mitigate the risk of exploitation. A list of the upgrade instructions can be found on the Aruba website.
Vulnerability Summary
This vulnerability is a remote code execution vulnerability in the Web Services Management Interface (WS-Man) component of Aruba InstantOS. An attacker could exploit this vulnerability to execute arbitrary code and take full control of an affected system.
Vulnerability Details
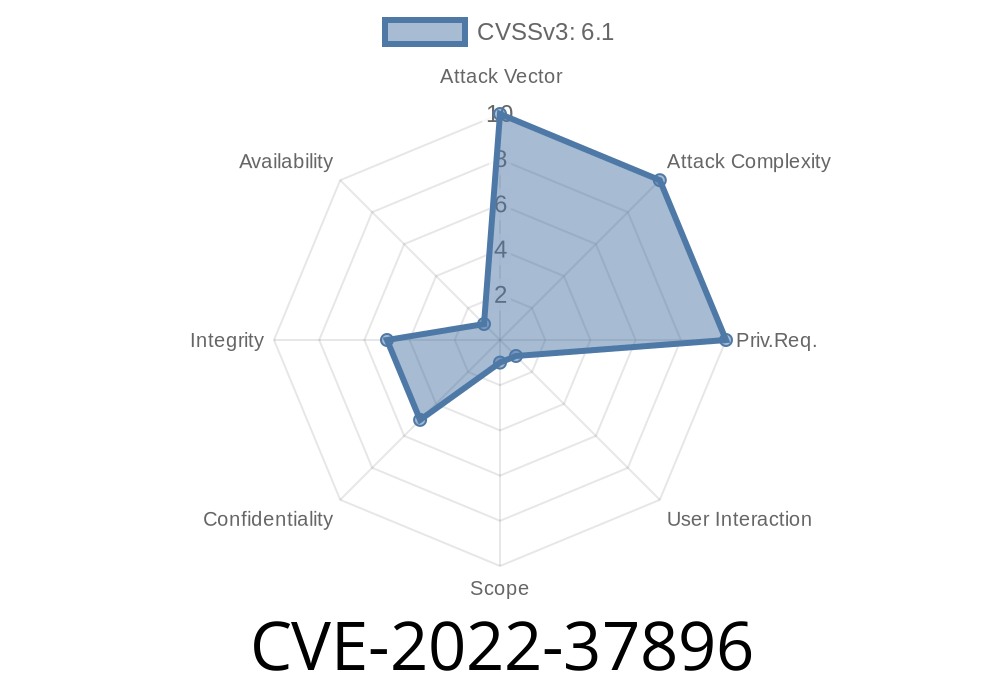
: CVE-2022-37896
An attacker can exploit this vulnerability by sending a malicious packet to the Aruba controller and have the controller execute arbitrary commands. This is done by sending a malicious request to the webapp.
ArubaOS 10.3.1 addresses this security vulnerability. Upgrade instructions can be found on the Aruba documentation website.
Timeline
Published on: 10/07/2022 19:15:00 UTC
Last modified on: 11/09/2022 04:00:00 UTC