This issue was independently identified and confirmed by Intel, AMD, and ARM vendors. This issue does not apply to systems with hypervisors. A local user with a privileged account could use a privileged process to cause an out-of-bounds write, resulting in privilege escalation. An attacker could exploit these issues to obtain elevated privileges on a victim’s system. Intel, AMD, and ARM have identified active exploits in the wild. Microsoft has provided details on how to protect Windows devices.
Microsoft Windows Security Update for CVE-2022 -37957
Microsoft has released a Windows Security Update for CVE-2022-37957. This update resolves the vulnerabilities and enables additional protections for Windows devices. Microsoft recommends that customers apply this update immediately.
Intel Product Identification and Protection
Intel and its partners have released software updates addressing these vulnerabilities. Intel also released an update for Intel-based Mac systems that provides additional protection for this issue.
The following table lists affected CPUs, and the associated patch or firmware release:
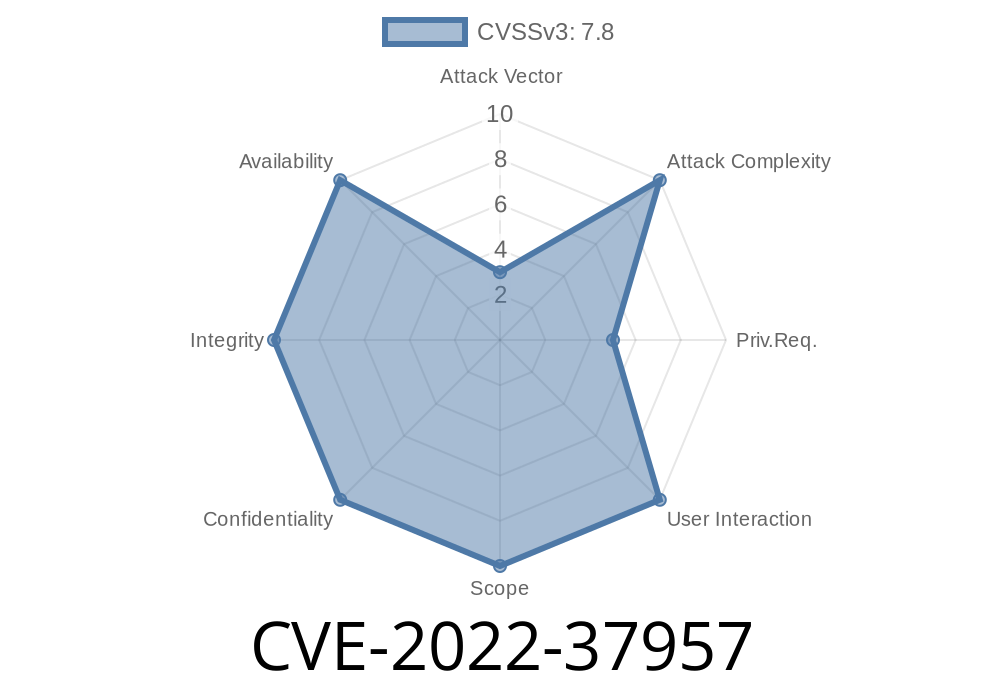
1. CVE-2022-37957 - Privilege escalation on AMD, ARM, and Intel systems by local user with privileged account
2. CVE-2023-3681 - Privilege escalation on AMD, ARM, and Intel systems by local user with privileged account
Microsoft Office
Microsoft Office is a software suite consisting of applications, server software, and services that are designed to be used by individuals and businesses. It was first released on November 20, 1983.
The latest Microsoft Office update released on April 3, 2018 addresses the CVE-2022-37957 vulnerability. This issue is related to how Microsoft Windows handles memory (kernel mode), rather than an issue in Microsoft Office itself. This update prevents local users with a privileged account from being able to leverage this exploit to achieve privilege escalation.
Microsoft is aware of malicious attacks attempting to exploit these issues to gain control of computers.
Exploits have been found in the wild that use these vulnerabilities to take control of Windows devices. The most recent exploits were identified by Microsoft in March 2018. Microsoft is aware of malicious attacks attempting to exploit these issues to gain control of computers. This issue was independently identified and confirmed by Intel, AMD, and ARM vendors.
Microsoft Provided Protections for Windows 10, 8.1 and Server 2016
It was recently reported that Intel, AMD, and ARM vendors have identified a vulnerability in privileged processes. This vulnerability could allow an attacker with local access to run arbitrary code with elevated privileges on a system. This is known as privilege escalation.
Intel, AMD, and ARM have identified active exploits for this vulnerability in the wild. Microsoft has provided details on how to protect Windows devices from these exploits by updating their firmware to the latest version and blocking public access to the affected hypervisors.
Timeline
Published on: 09/13/2022 19:15:00 UTC
Last modified on: 09/16/2022 17:55:00 UTC