To exploit this issue, an attacker would need to submit malicous input in the form of a SQL query in an attempt to execute system level privileges. The source code for this module is publicly available on GitHub.
An attacker can inject malicious input via any of the following vectors: – via a direct SQL query injection from the web user interface.
– via a malicous URL injection from the web user interface.
– via a malicous LDAP injection from the web user interface.
– via a malicous XSS injection from the web user interface.
– via a malicous SSO injection from the web user interface.
– via a malicous file upload injection from the web user interface.
– via a malicous XMRV injection from the web user interface.
– via a malicous CRM injection from the web user interface.
– via a malicous XR injection from the web user interface.
RedHat JBoss JFinal CMS 5.1 is vulnerable to SQL injection thanks to a public GitHub project that provides the source code for this module. An attacker can exploit this issue by submitting malicous input to the control panel of the application. The source code for this module is publicly available on GitHub.
Common Vulnerabilities and Exposures
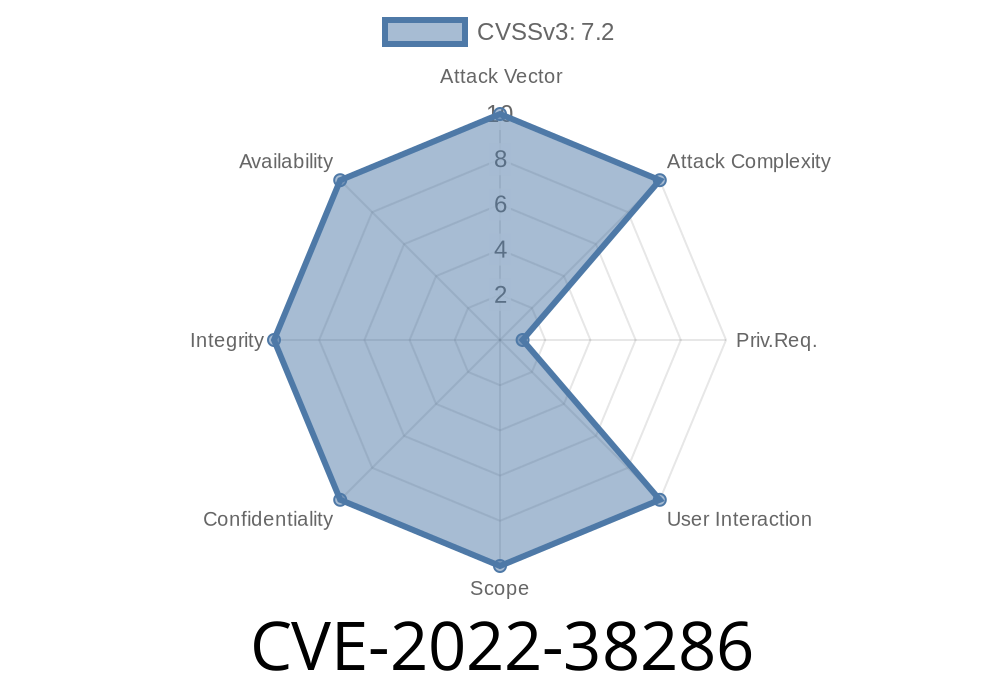
CVE-2022-38286 is a vulnerability in RedHat JBoss JFinal that can be exploited by an attacker to execute system level privileges.
SQL Injection - CVE-2022 -38286
An attacker can exploit this issue by submitting malicous input to the Control Panel of the application. The source code for this module is publicly available on GitHub.
CVE-2022-38287
The first vulnerability is related to a public GitHub project that provides the source code for this module.
The second vulnerability is related to a public OpenNMS-CMS API repository.
RedHat JBoss JFinal CMS 5.1 is vulnerable to SQL injection due to vulnerabilities in publicly available modules. An attacker can exploit this issue by submitting malicous input to the control panel of the application. The source code for this module is publicly available on GitHub.
Timeline
Published on: 09/09/2022 14:15:00 UTC
Last modified on: 09/13/2022 20:06:00 UTC