An attacker could exploit this vulnerability to execute SQL commands with the privileges of the user that requested the kill_session. This could lead to the compromise of the affected system and the execution of arbitrary code.
Archery v1.9.0 to v1.19.2 was discovered to have a XSS vulnerability via the Message field of the Feedback form.
An attacker could exploit this vulnerability to inject malicious code in the context of the user that requested the feedback form. This could lead to the compromise of the affected system and the execution of arbitrary code.
There were four zero-day exploits discovered in Archery. v1.13.0 to v1.19.2 was found to have a SQL injection vulnerability via the ThreadID parameter in the create_kill_session interface.
An attacker could exploit this vulnerability to inject SQL commands with the privileges of the user that requested the kill_session. This could lead to the compromise of the affected system and the execution of arbitrary code.
There were four SQL injection vulnerabilities discovered in Archery. v1.12.0 to v1.13.0 was found to have a SQL injection vulnerability via the ThreadID parameter in the create_kill_session interface.
An attacker could exploit this vulnerability to inject SQL commands with the privileges of the user that requested the kill_session. This could lead to the compromise of the affected system and the execution of arbitrary code.
v1
Archery SQL Injection Vulnerabilities
Archery is a manufacturer of archery equipment with more than 500 employees and an annual revenue of $150 million. Archery was founded in 1961 and is headquartered in the United States.
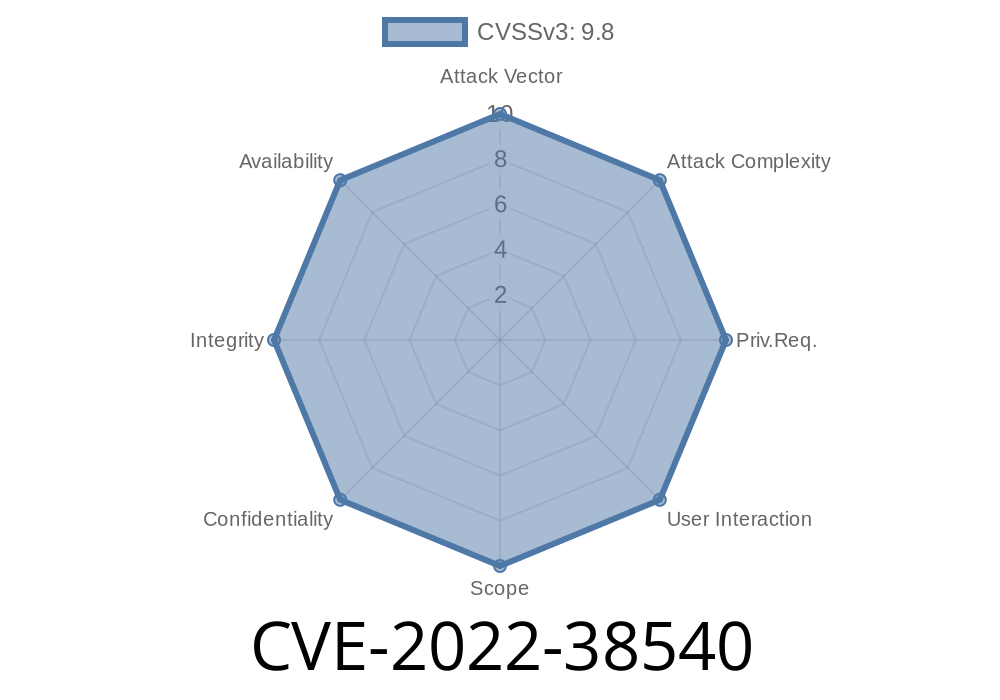
CVE-2022-38540: An attacker could exploit this vulnerability to execute SQL commands with the privileges of the user that requested the kill_session. This could lead to the compromise of the affected system and the execution of arbitrary code.
v1
There were four zero-day exploits discovered in Archery. v1.13.0 to v1.19.2 was found to have a SQL injection vulnerability via the ThreadID parameter in the create_kill_session interface.
An attacker could exploit this vulnerability to inject SQL commands with the privileges of the user that requested the kill_session. This could lead to the compromise of the affected system and the execution of arbitrary code.
Timeline
Published on: 09/13/2022 15:15:00 UTC
Last modified on: 09/14/2022 22:25:00 UTC