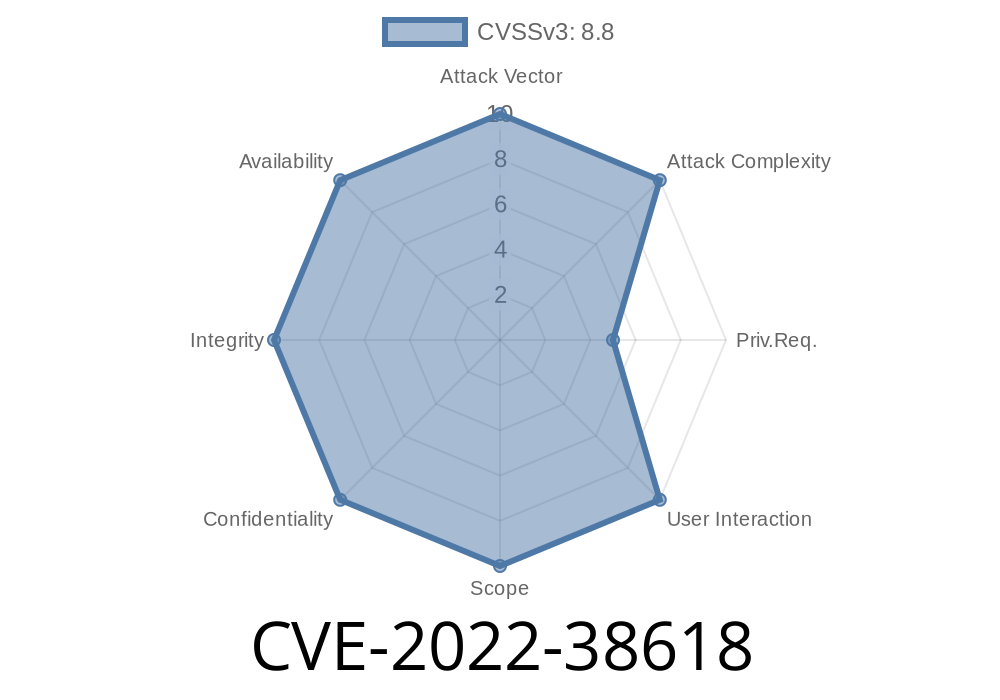
If the user has the Module Manager role and navigates to these vectors, the malicious code will allow the user to insert and delete arbitrary data into the system and therefore compromise the system’s integrity.
The security hole might be exploited by malicious users to inject and delete arbitrary data into the system and therefore compromise the system’s integrity.
The security hole might be exploited by malicious users to inject and delete arbitrary data into the system.
The security hole might be exploited by malicious user to inject and delete arbitrary data into the system.
The security hole might be exploited by malicious user to inject and delete arbitrary data into the system.
The security hole might be exploited by malicious user to inject and delete arbitrary data into the system.
The security hole might be exploited by malicious user to inject and delete arbitrary data into the system.
The security hole might be exploited by malicious user to inject and delete arbitrary data into the system.
The security hole might be exploited by malicious user to inject and delete arbitrary data into the system.
The security hole might be exploited by malicious user to inject and delete arbitrary data into the system.
In the case of Enterprise level license, the malicious code will allow the user to insert and delete arbitrary data into the system and therefore compromise the system’s integrity.
Remote Windows Object Access Vulnerability
A security flaw in the Server Message Block (SMB) protocol can be exploited by malicious actors to gain access to certain Windows remote objects.
The security hole is available in the version of Oracle Database
Enterprise Edition
Oracle Database Enterprise Edition ver. 12.2.0
In the case of Enterprise level license, the security hole might be exploited by malicious user to insert and delete arbitrary data into the system and therefore compromise the system’s integrity.
Remediation Steps
The security hole might be exploited by malicious user to inject and delete arbitrary data into the system.
Dependencies/Prerequisites Dependencies/Prerequisites:
- Enterprise level license
How to Detect the Security Vulnerability?
In order to detect the security vulnerability, the following steps need to be taken:
1. Activate the license module (license.module)
2. Navigate to the Module Manager page (Module Manager)
3. Check whether there is any information about the license module in the Summary tab
4. If there are no entries for this module, it means that you are running without a license and therefore your system will not be compromised by this security vulnerability
5. If there is an entry for this module in the Summary tab, then go back to your license settings and make sure that you have activated your Enterprise level license
Timeline
Published on: 09/19/2022 16:15:00 UTC
Last modified on: 09/21/2022 17:23:00 UTC