By injecting malicious SQL code into the ‘username’ and ‘password’ parameters, an attacker could exploit the system to gain remote access to the system.
Hospital Management System v1.0 also suffers from a path redirect vulnerability. This could be exploited by attackers to redirect users to arbitrary locations on the web server.
In addition, Hospital Management System v1.0 is vulnerable to an XSS injection flaw. This can be exploited by injecting malicious code into the ‘referer’ HTTP header, causing the code to be displayed to the user.
It is highly recommended you update Hospital Management System v1.0 as soon as possible.
Source: https://www.vulnerability-lab.com/show/ Hospital Management System v1.0 was found to suffer from multiple severe vulnerabilities. These are summarized in the table below. Hospital Management System v1.0 could be exploited to gain access to critical functions of the software, such as uploading or deleting files, or changing system settings. An attacker would need only log in with the chosen username and password to start exploiting the vulnerabilities.
Summary of vulnerabilities
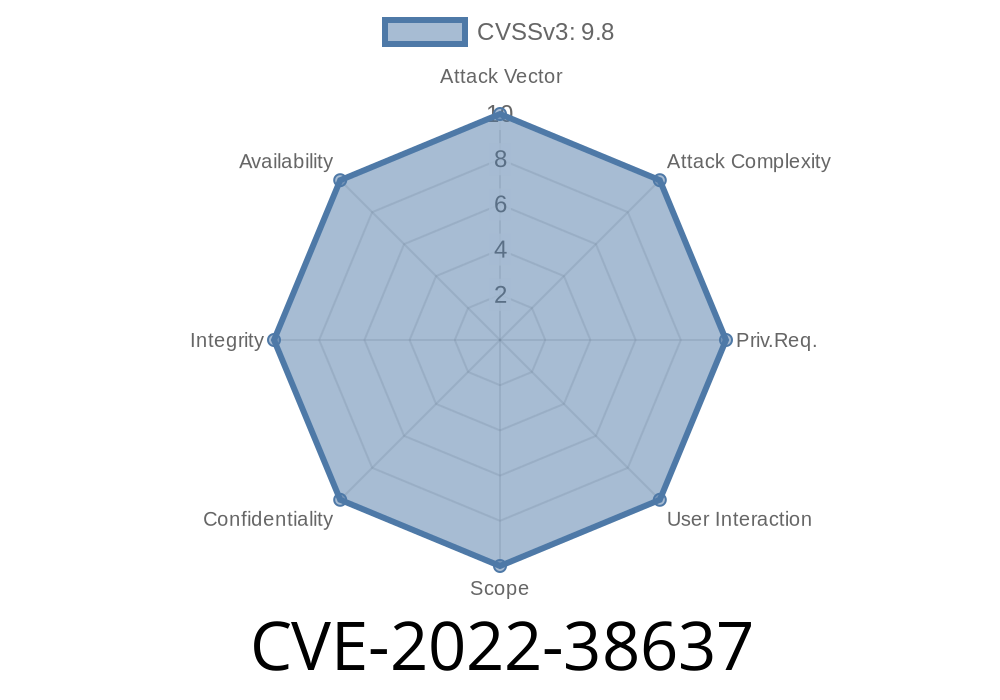
Summary of vulnerabilities in Hospital Management System v1.0 CVE-2022-38637
Path redirect vulnerability: the system is vulnerable to a race condition that can be exploited by an attacker to redirect users to arbitrary locations on the web server.
Multiple vulnerabilities of SQL injection: it was found that Hospital Management System v1.0 is prone to multiple SQL injection vulnerabilities, including one in which the username and password parameters are vulnerable to injection.
XSS vulnerability: this could be exploited by injecting malicious code into the ‘referer’ HTTP header, causing the code to be displayed to the user.
SQL Injection vulnerability
This vulnerability assesses a SQL injection vulnerability. What this means is an attacker can inject malicious SQL code into the ‘username’ and ‘password’ parameters of Hospital Management System v1.0. This code would then execute, allowing the attacker to gain remote access to the system.
1.1 Overview of the vulnerabilities
The vulnerabilities were found to be of severe importance and highly critical. The most critical vulnerability found was the SQL injection vulnerability that could be exploited by an attacker to gain remote access to the system. This could allow the attacker to upload or delete files, change system settings, or simply log in with a chosen username and password.
Additionally, Hospital Management System v1.0 is vulnerable to a path redirect vulnerability, which could be exploited by attackers to redirect users to arbitrary locales on the web server. Furthermore, it is vulnerable to an XSS injection flaw that can be exploited by injecting malicious code into the ‘referer’ HTTP header causing the code to be displayed back to the user. These vulnerabilities would need a valid user account and a valid username and password combination in order for them to be exploited successfully.
Timeline
Published on: 09/13/2022 21:15:00 UTC
Last modified on: 09/16/2022 02:58:00 UTC